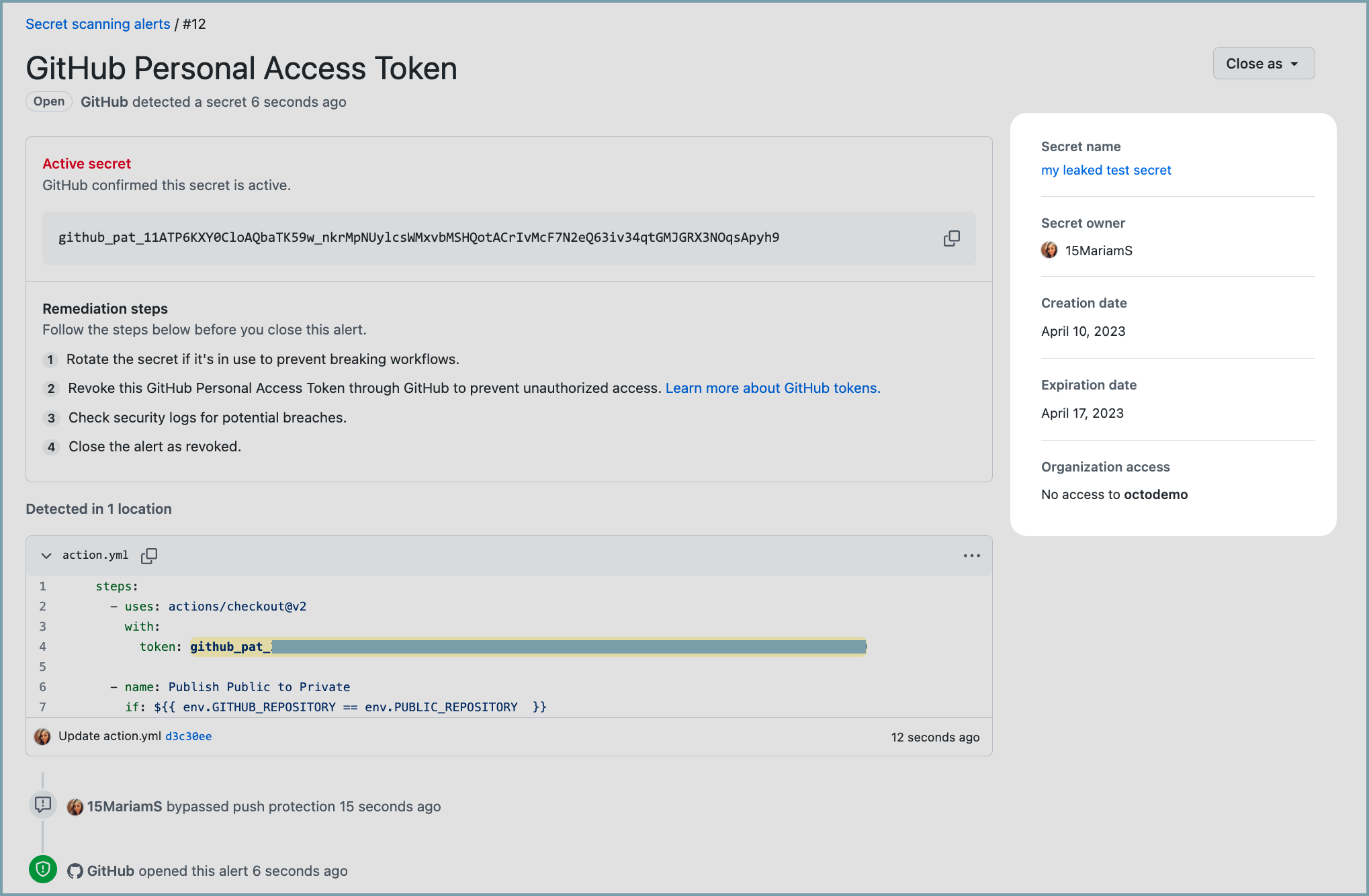
GitHub secret scanning protects users by searching repositories for known types of secrets. By identifying and flagging these secrets, our scans help prevent data leaks and fraud.
We have partnered with Doppler to scan for their tokens and help secure our mutual users on public repositories. Doppler tokens allow users to access and manage their secrets from their existing tooling and infrastructure. GitHub will forward access tokens found in public repositories to Doppler, who will revoke the tokens and email affected customers. You can read more information about Doppler tokens here.
GitHub Advanced Security customers can also scan for Doppler tokens and block them from entering their private and public repositories with push protection.