Justin Hutchings
Director of Product Management for supply chain security. I manage the team that's behind Dependabot, the Advisory Database, and the dependency graph. Twitter: https://twitter.com/jhutchings0
Commit signing is now enabled for all bots by default.
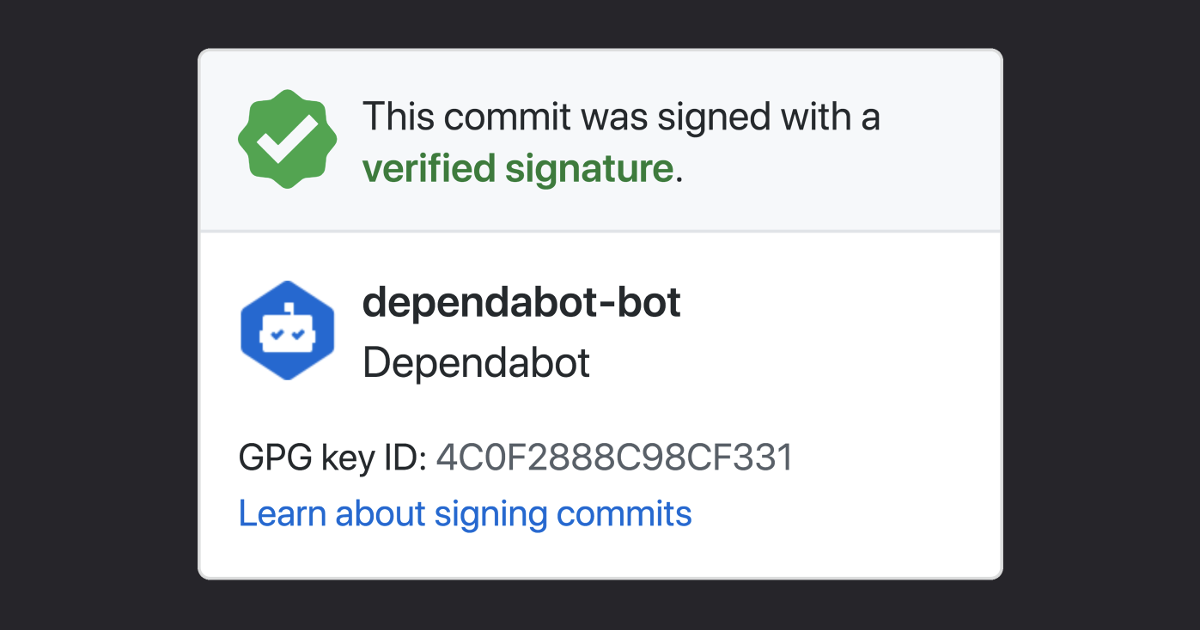
Businesses and open source projects alike want to be sure that a commit is from a verified source—whether it’s from a developer across the world or a bot that’s integrated into their workflow.
GitHub has supported GPG signature verification for human-authored commits for a while, but bots like Dependabot are becoming an increasingly important part of our workflows. That changes now—bot commit signing has been enabled for all bots by default.

Commit signing allows a user (or bot) to cryptographically vouch for the integrity of the commit, and that they authored it. If a commit or tag has a GPG or S/MIME signature that is cryptographically verifiable, GitHub marks the commit or tag as verified with a big green checkmark ✓.
Find out more about commit signature verification
Did you know? Support for commit signing was introduced in January 2012 when v1.7.9 was released. We introduced support on GitHub.com back in April 2016.
Learn how GitHub built an accessible, multi-terminal-safe ASCII animation for the Copilot CLI using custom tooling, ANSI color roles, and advanced terminal engineering.

User feedback led us to clean up outdated mitigations. See why observability and lifecycle management are critical for defense systems.
GitHub is introducing post-quantum secure key exchange methods for SSH access to better protect Git data in transit.