
How AI enhances static application security testing (SAST)
Here’s how SAST tools combine generative AI with code scanning to help you deliver features faster and keep vulnerabilities out of code.

Here’s how SAST tools combine generative AI with code scanning to help you deliver features faster and keep vulnerabilities out of code.
Learn how to use CodeQL for security research and improve your security research workflow.

Now in public beta for GitHub Advanced Security customers, code scanning autofix helps developers remediate more than two-thirds of supported alerts with little or no editing.

A peek under the hood of GitHub Advanced Security code scanning autofix.
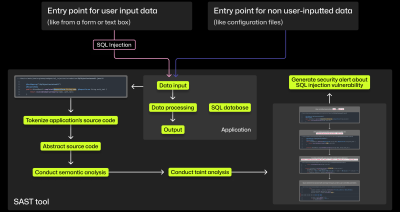
More developers will have to fix security issues in the age of shifting left. Here, we break down how SAST tools can help them find and address vulnerabilities.

In practice, shifting left has been more about shifting the burden rather than the ability. But AI is bringing its promise closer to reality. Here’s how.

This blog post describes two linked vulnerabilities found in Frigate, an AI-powered security camera manager, that could have enabled an attacker to silently gain remote code execution.

We’ve added new improvements to default setup, including automatically scheduling scans on repositories and support for all CodeQL covered languages.

Learn how researchers and security experts at GitHub, Microsoft, and Santander came together to address the challenges presented by the post-quantum cryptography world.

The effectiveness of a static application security solution hinges on its ability to provide extensive vulnerability coverage and support for a wide range of languages and frameworks. Today, we’re highlighting two releases that’ll help you discover more vulnerabilities in your codebase, so you can ship more secure software.

Learn how GitHub’s CodeQL leveraged AI modeling and multi-repository variant analysis to discover a new CVE in Gradle.

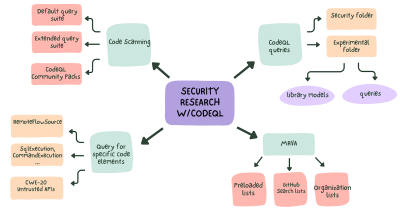
Learn the basics of CodeQL and how to use it for security research! In this blog, we will teach you how to leverage GitHub’s static analysis tool CodeQL to write custom CodeQL queries.

We’ve launched the beta of code scanning support for Swift. This launch, paired with our launch of Kotlin support in November, means that CodeQL covers both IOS and Android development languages, bringing a heightened level of security to the mobile application development process.
Code scanning’s tool status gives you a bird’s eye view of your application security stack, allowing you to quickly confirm everything is working, or troubleshoot any tool in your application security arsenal.
We’ve gotten great feedback on default setup, a simple way to set up code scanning on your repository. Now, you have the ability to use default setup across your organization’s repositories, in just one click.
Build what’s next on GitHub, the place for anyone from anywhere to build anything.
Get tickets to the 10th anniversary of our global developer event on AI, DevEx, and security.