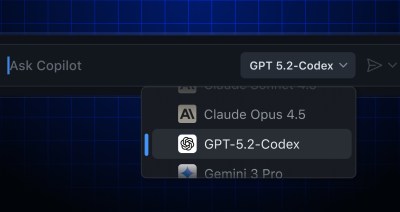
Simplified Copilot model enablement experience for individual users
We’ve made it easier to discover and use the latest models across all Copilot features. If you’re a Copilot Pro+, Pro, or Free user, newly released models are now available…

We’ve made it easier to discover and use the latest models across all Copilot features. If you’re a Copilot Pro+, Pro, or Free user, newly released models are now available…

CodeQL is the static analysis engine behind GitHub code scanning, which finds and remediates security issues in your code. We’ve recently released CodeQL 2.24.0, which adds support for new language…
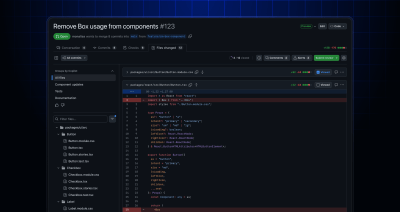
The improved pull request “Files Changed” experience, currently in public preview, is rolling out as the default experience to all users! 🎉 This improved experience is designed to be familiar…

CodeQL is the static analysis engine behind GitHub’s Code Scanning and Code Quality products, which find and remediate issues relating to code quality and security. We’ve recently released CodeQL 2.23.7…

Run multiple Copilot agents from one place. Learn prompt techniques, how to spot drift early, and how to review agent work efficiently.

Finding the perfect gift for your favorite developer is easy with our top tips.
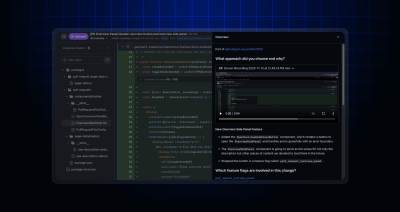
You can now view the pull request description without leaving the new “Files changed” page. No need to scroll to the top of the page, switch tabs, or lose context.…

The open source Git project just released Git 2.52. Here is GitHub’s look at some of the most interesting features and changes introduced since last time.
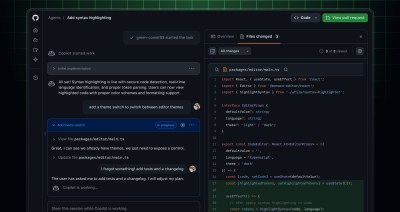
We’ve redesigned how you manage your Copilot coding agent tasks on github.com. Instead of jumping between pages to track progress, monitor changes, and manage tasks, everything you need now lives…

You can now assign GitHub code scanning alerts directly to Copilot to assist with automated remediation. This extends Copilot coding agent capabilities to security vulnerabilities, enabling faster resolution of common…

For this year’s Cybersecurity Awareness Month, the GitHub Bug Bounty team is excited to put the spotlight on a talented security researcher—André Storfjord Kristiansen!

Starting September 29, 2025, a new comprehensive premium request dashboard will be available that provides insights about your premium request activity dating back to August 1, 2025. This new dashboard…

We have a major update to announce to the new pull request “Files changed” page: you can now comment anywhere in a changed file! 🎉 This feature and the new…

This guide offers five essential tips for writing effective GitHub Copilot custom instructions, covering project overview, tech stack, coding guidelines, structure, and resources, to help developers get better code suggestions.

@cole-hartman and @dorisbwang joined the GitHub Apps team for the summer with a focus on improving the developer experience around fine-grained PAT creation. They worked with our design and product…

Learn Model Context Protocol by building a turn-based game server that shows how to extend GitHub Copilot with custom tools, resources, and prompts.

Open source is aging. We can better support Gen Z contributors through purpose, flexibility, and pathways to leadership.

Now generally available, GitHub Secret Protection users have the ability to configure which secret scanning patterns are included in push protection. This customization helps you to better meet your organization’s…

Discover the latest trends and insights on public software development activity on GitHub with the quarterly release of data for the Innovation Graph, updated through March 2025.

We’ve made numerous improvements to the new pull request “Files changed” page that launched as a public preview in June. This new page will eventually replace the existing page and…

Security teams can now choose which secret scanning patterns are included in push protection. Previously, push protection only covered a subset of patterns that met strict criteria. With this update,…
Build what’s next on GitHub, the place for anyone from anywhere to build anything.
Catch up on the GitHub podcast, a show dedicated to the topics, trends, stories and culture in and around the open source developer community on GitHub.