Justin Hutchings
Director of Product Management for supply chain security. I manage the team that's behind Dependabot, the Advisory Database, and the dependency graph. Twitter: https://twitter.com/jhutchings0
Now available, code scanning is a developer-first, GitHub-native approach to easily find security vulnerabilities before they reach production.

GitHub code scanning is a developer-first, GitHub-native approach to easily find security vulnerabilities before they reach production. We’re thrilled to announce the general availability of code scanning. You can enable it on your public repository today!
One year ago, GitHub welcomed Semmle. We’ve since worked to bring the revolutionary code analysis capabilities of its CodeQL technology to GitHub users as a native capability. At GitHub Satellite in May, we released the first beta of our native integration: code scanning. Now, thanks to the thousands of developers in the community who tested and gave feedback, we’re proud to announce that code scanning is generally available.
Code scanning is designed for developers first. Instead of overwhelming you with linting suggestions, code scanning runs only the actionable security rules by default so that you can stay focused on the task at hand.
Code scanning integrates with GitHub Actions—or your existing CI/CD environment—to maximize flexibility for your team. It scans code as it’s created and surfaces actionable security reviews within pull requests and other GitHub experiences you use everyday, automating security as a part of your workflow. This helps ensure vulnerabilities never make it to production in the first place.
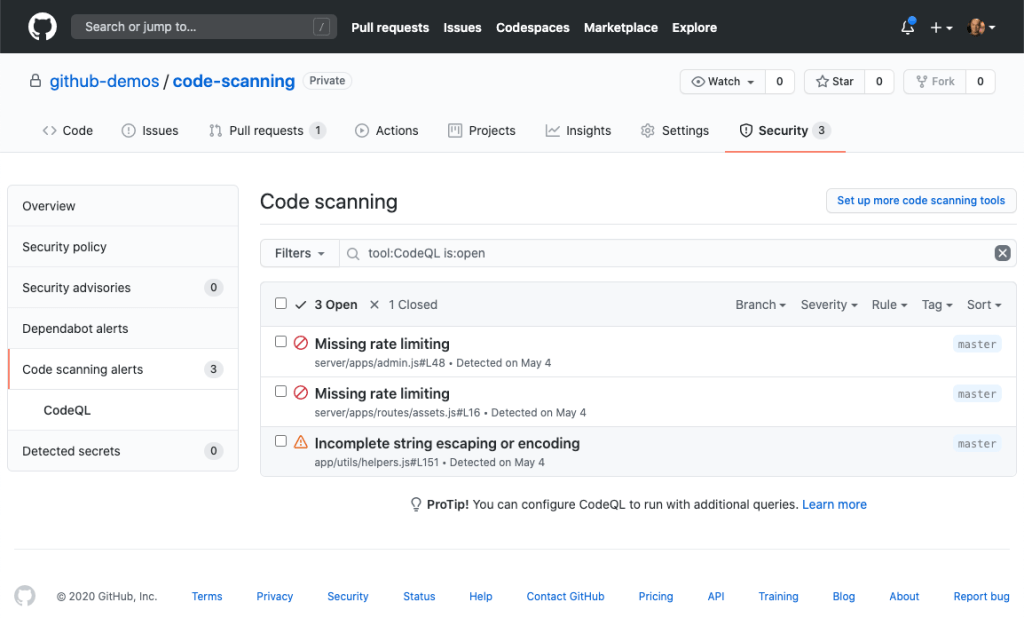
Code scanning is powered by CodeQL—the world’s most powerful code analysis engine. You can use the 2,000+ CodeQL queries created by GitHub and the community, or create custom queries to easily find and prevent new security concerns.
Built on the open SARIF standard, code scanning is extensible so you can include open source and commercial static application security testing (SAST) solutions within the same GitHub-native experience you love. You can integrate third-party scanning engines to view results from all your security tools in a single interface and also export multiple scan results through a single API. We’ll share more on our extensibility capabilities and partner ecosystem soon, so stay tuned.
Since introducing the beta in May, we’ve seen tremendous adoption within the community:
Code scanning is free for public repositories and is a GitHub Advanced Security feature for GitHub Enterprise. Here’s what some teams have shared about their experience with code scanning so far:
“We chose Advanced Security for its out-of-the-box functionality and the custom functionality that we can build off of. Instead of it taking a full day to find and fix one security issue, we were able to find and fix three issues in the same amount of time.”
– Charlotte Townsley, Director of Security Engineering, Auth0
“GitHub allows us to enable security, versus enforcing it. The sooner we can catch vulnerabilities and product issues, the better it is for the company in the long run.”
– James Hurley, Director of Developer Services, McKesson Labs
“If Advanced Security reports error issues, the pull request isn’t allowed to be merged. If a security issue is found, we’re informed immediately. We go over anything GitHub has highlighted, and we make sure that it’s resolved before releasing a stable release. For the developer who will press the merge button, it inspires confidence.”
– Dimosthenis Kaponis, CTO, Netdata

In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.