Announcing GitHub Security Lab: securing the world’s code, together
On Day Two of GitHub Universe 2019, we announced GitHub Security Lab to bring together security researchers, maintainers, and companies across the industry who share our belief that the security of open source is important for everyone.

We all share a collective responsibility to keep open source software secure—none of us can do it alone. Today at GitHub Universe, we announced GitHub Security Lab to bring together security researchers, maintainers, and companies across the industry who share our belief that the security of open source is important for everyone.
We’re excited to have an initial set of partners that have all committed to achieving this goal. Together, we’re contributing tools, resources, bounties, and thousands of hours of security research to help secure the open source ecosystem.
As part of today’s announcement, GitHub Security Lab is making CodeQL freely available for anyone to find vulnerabilities in open source code. CodeQL is a tool many security research teams around the world use to perform semantic analysis of code, and we’ve used it ourselves to find over 100 reported CVEs in some of the most popular open source projects.
We’re also launching the GitHub Advisory Database, a public database of advisories created on GitHub, plus additional data curated and mapped to packages tracked by the GitHub dependency graph.
GitHub’s approach to security addresses the whole open source security lifecycle. GitHub Security Lab will help identify and report vulnerabilities in open source software, while maintainers and developers use GitHub to create fixes, coordinate disclosure, and update dependent projects to a fixed version.
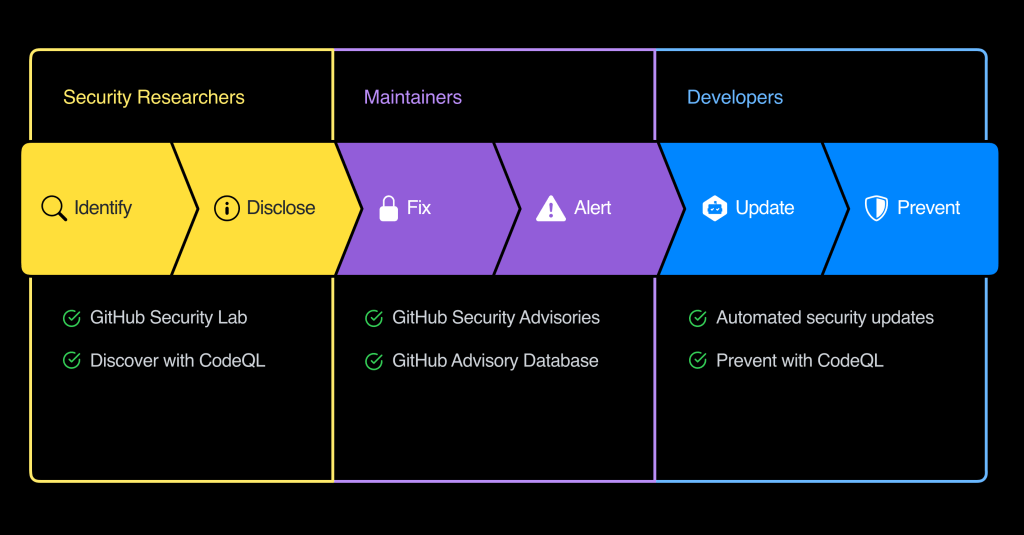
GitHub Security Lab
GitHub Security Lab’s mission is to inspire and enable the global security research community to secure the world’s code. Our team will lead by example, dedicating full-time resources to finding and reporting vulnerabilities in critical open source projects. The team has already had over 100 CVEs issued for security vulnerabilities it has found.
Securing the world’s open source software is a daunting task. First, there’s scale: the JavaScript ecosystem alone has over one million open source packages. Then there’s the shortage of security expertise: security professionals are outnumbered 500 to one by developers. Finally there’s coordination: the world’s security experts are spread across thousands of companies. GitHub Security Lab and CodeQL will help level the playing field.
Joining us in this effort are the following companies, donating their time and expertise to find and report vulnerabilities in open source software. Each have committed to contribute in a different way, and we hope others will join us in future.
- F5
- HackerOne
- Intel
- IOActive
- J.P. Morgan
- Microsoft
- Mozilla
- NCC Group
- Okta
- Trail of Bits
- Uber
- VMWare
To empower the research community, we’re also making our state-of-the art code analysis engine, CodeQL, free to use on open source. CodeQL lets you query code as though it were data. If you know of a coding mistake that caused a vulnerability, you can write a query to find all variants of that code, eradicating a whole class of vulnerabilities forever. See how to get started with CodeQL.
If you’re a security researcher or work in a security team, we want your help. Securing the world’s open source software will require the whole community to work together. GitHub Security Lab will run events and share best practices to help everyone participate. Follow the @GHSecurityLab account on Twitter for more details.
Improving the open source security workflow
As the world’s security researchers uncover more vulnerabilities, maintainers and end users need better tools to handle them.
Today the process for addressing a new vulnerability is often ad hoc. Forty percent of new vulnerabilities in open source don’t have a CVE identifier when they’re announced, meaning they’re not included in any public database. Seventy percent of critical vulnerabilities remain unpatched 30 days after developers have been notified.
We’re fixing that. Maintainers and developers can now work together directly on GitHub to help ensure new vulnerabilities are only disclosed when maintainers are ready, and that developers can update to fixed versions quickly and easily.
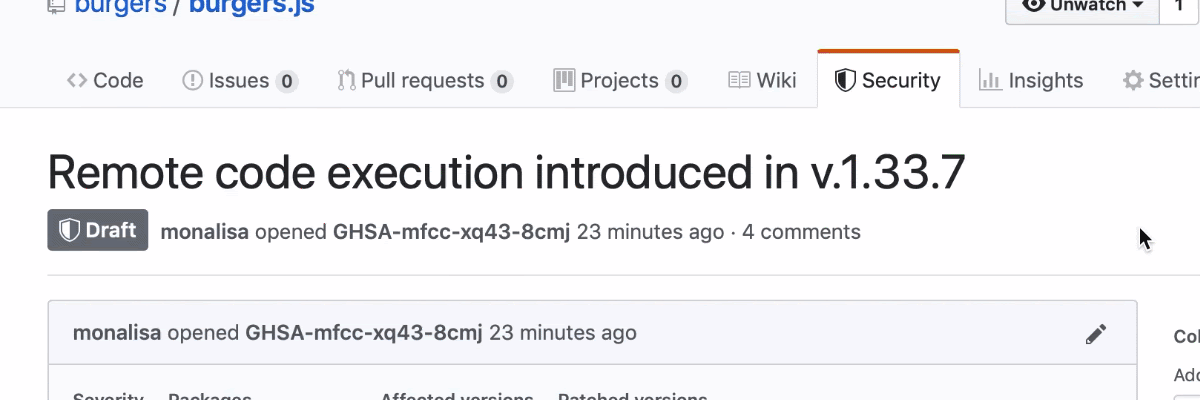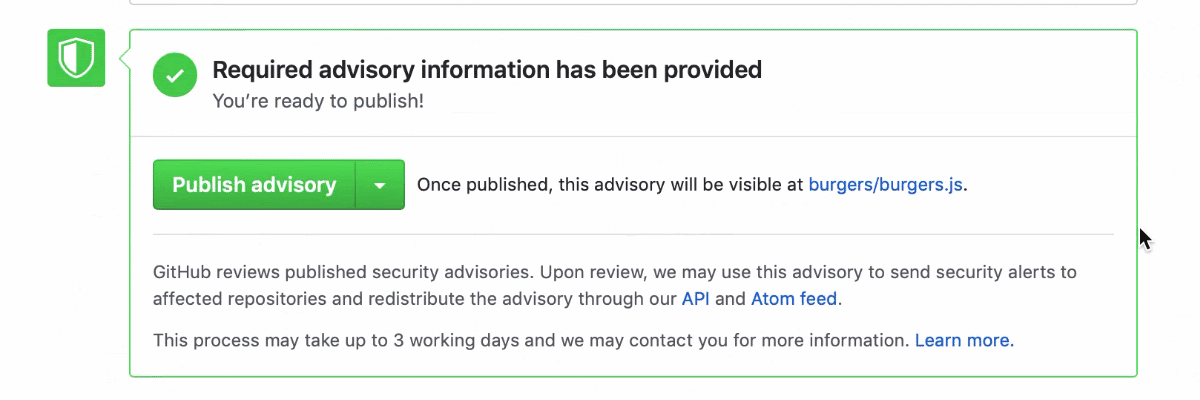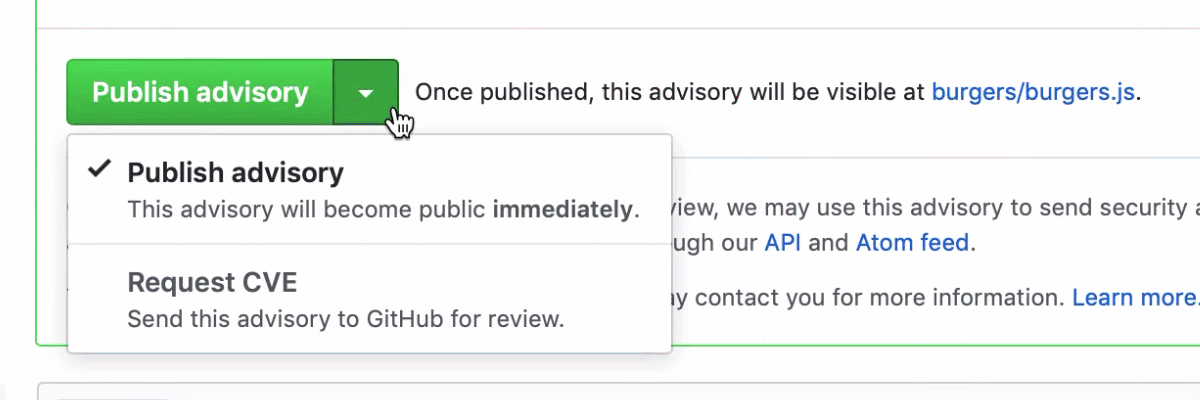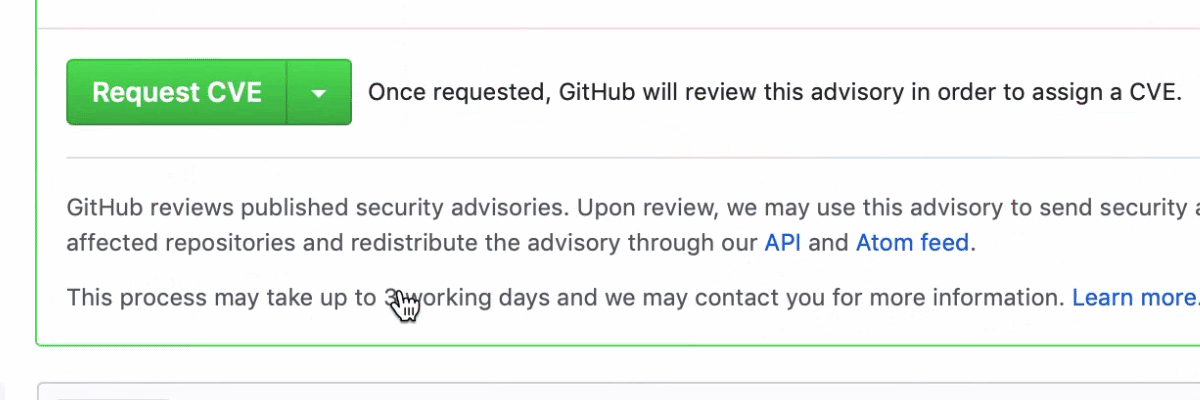
GitHub Security Advisories
With Security Advisories, maintainers can work with security researchers on security fixes in a private space, apply for a CVE directly from GitHub, and specify structured details about the vulnerability. Then, when they’re ready to publish the Security Advisory, GitHub will send security alerts to affected projects.
Automated security updates
Receiving a notification about vulnerable dependencies is helpful, but getting a pull requests with a fix is even better. To help developers respond quickly to new vulnerabilities GitHub creates automated security updates—pull requests that update a vulnerable dependency to a fixed version.
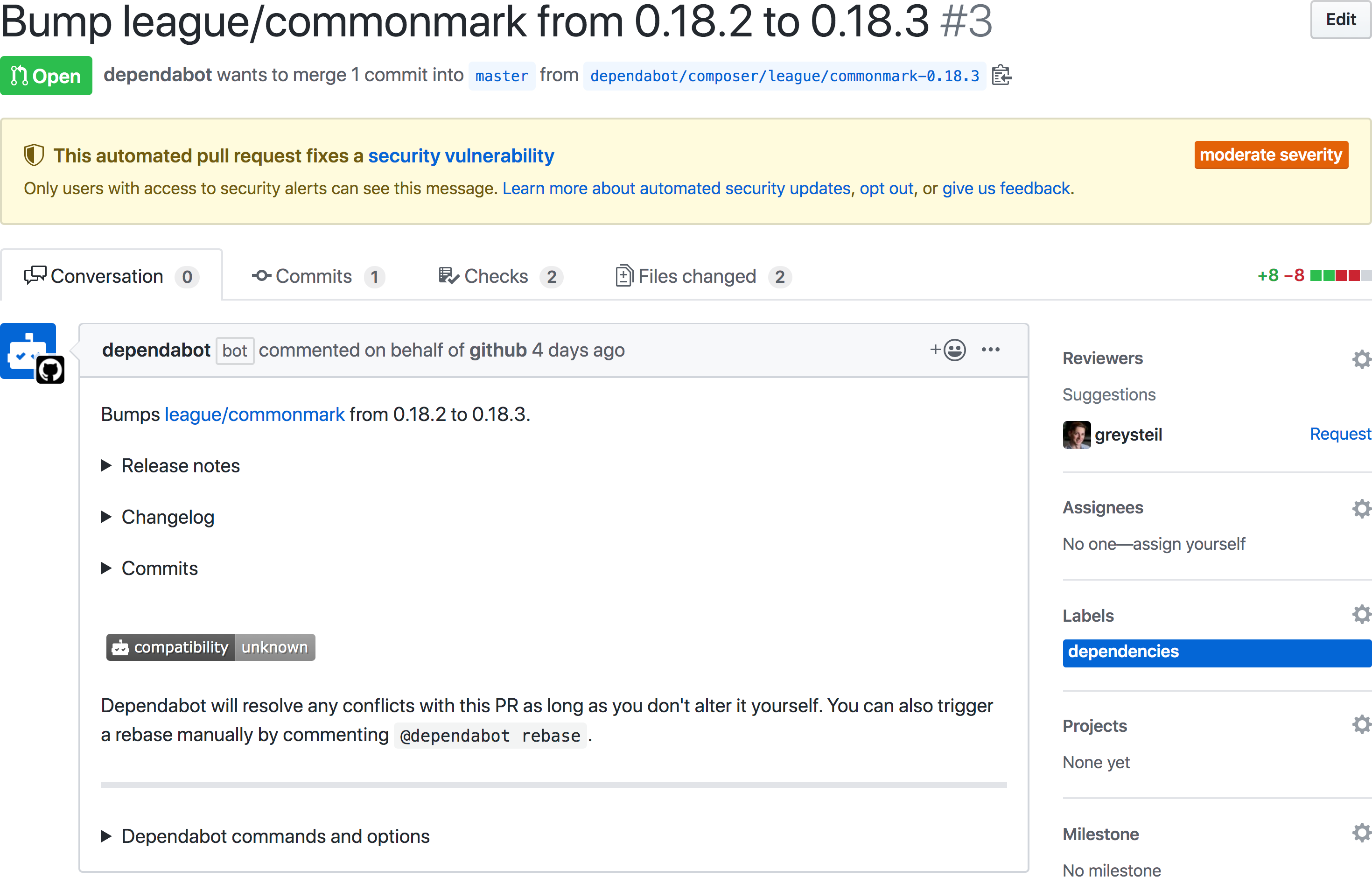
Automated security updates were launched in beta at GitHub Satellite 2019 and are now generally available and rolled out to every active repository with security alerts enabled.
Token scanning
One of the most common security mistakes is hard coding tokens or credentials into a project. Within seconds of a commit being pushed to GitHub (or a repositories being made public), we scan it for token formats from 20 different cloud providers. When we detect a match, we notify the appropriate service provider and they take action, generally revoking the tokens and notifying the affected users. And today we announced four more partners: GoCardless, HashiCorp, Postman, and Tencent.
GitHub Advisory Database
We’ve made all of the data that maintainers create in GitHub Security Advisories, plus additional data curated and mapped to packages tracked by the GitHub dependency graph, available for free. Explore the new GitHub Advisory Database in your browser, link directly to records with CVE identifiers in comments, or access the data programmatically using the Security Advisory API endpoint.
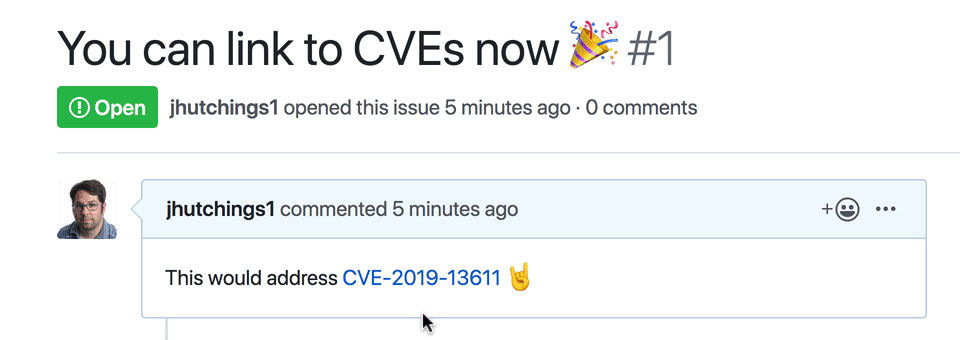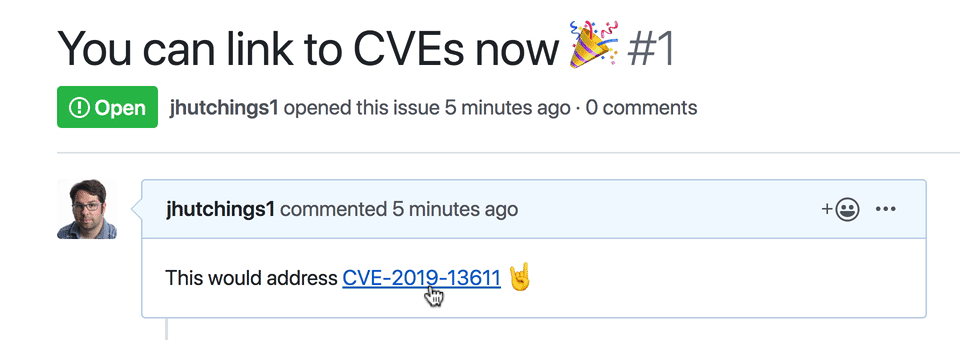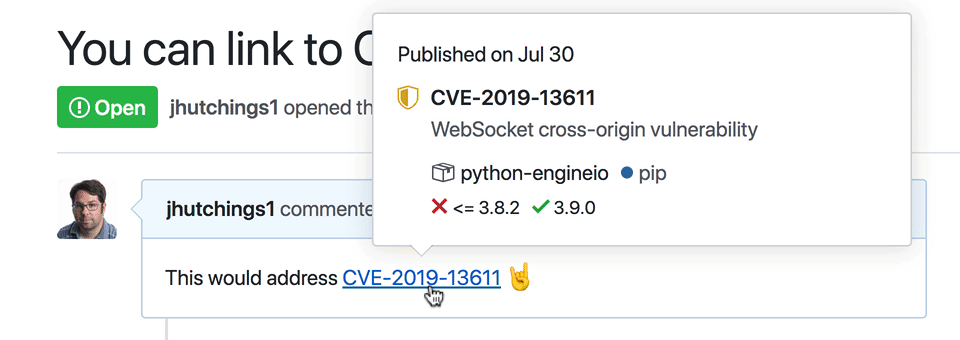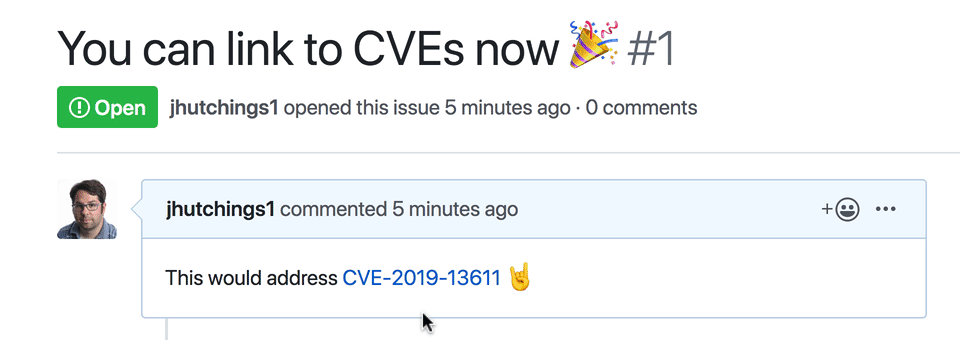
Review all of today’s ships on the GitHub Changelog:
› Automated security updates now generally available
› Security Advisories generally available, can request CVEs
› GitHub Security Lab and CodeQL for Research announced
› GoCardless, Hashicorp, Postman, and Tencent Cloud join our token scanning program
Written by
Related posts

From pair to peer programmer: Our vision for agentic workflows in GitHub Copilot
AI agents in GitHub Copilot don’t just assist developers but actively solve problems through multi-step reasoning and execution. Here’s what that means.

GitHub Availability Report: May 2025
In May, we experienced three incidents that resulted in degraded performance across GitHub services.

GitHub Universe 2025: Here’s what’s in store at this year’s developer wonderland
Sharpen your skills, test out new tools, and connect with people who build like you.