Release
Mobile monthly: February’s general availability and more
January and February brought a number of improvements to GitHub Mobile, making it more powerful and flexible. We’re rolling out exciting new features designed to make coding and collaboration easier on the go. From third-party integrations that extend GitHub Copilot’s capabilities to in-chat coding assistance, sub-issues, and refined notification preferences, these updates are designed to boost productivity and keep you connected wherever you are.
What’s new:
- Introducing GitHub Copilot Chat to all users on GitHub Mobile for free. Just tap the Copilot button to start getting answers for coding questions, or chat about issues, pull requests, and repositories wherever you are.
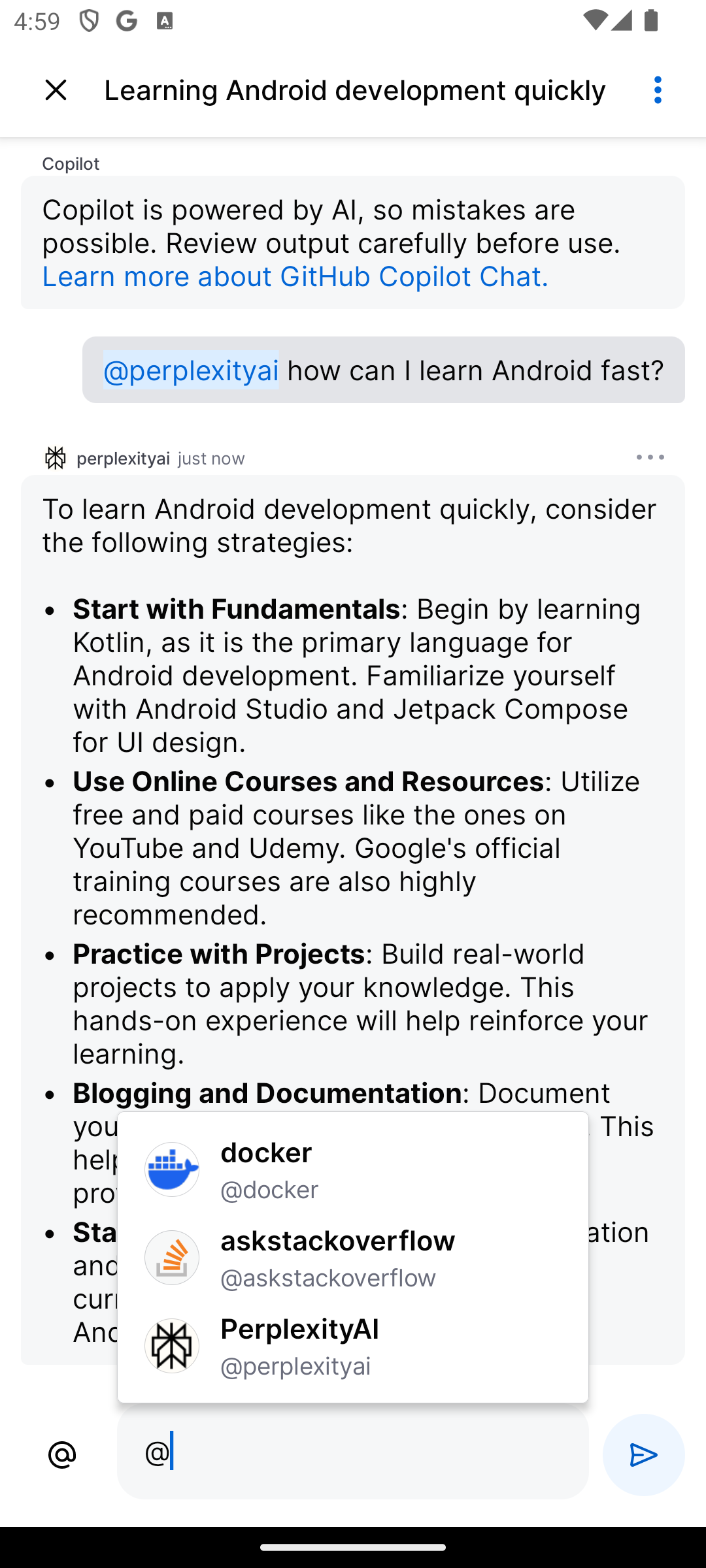
- Copilot Extensions on GitHub Mobile are generally available. Developers can extend Copilot’s capabilities on the go, integrating third-party tools, automating tasks, and receiving personalized code suggestions.
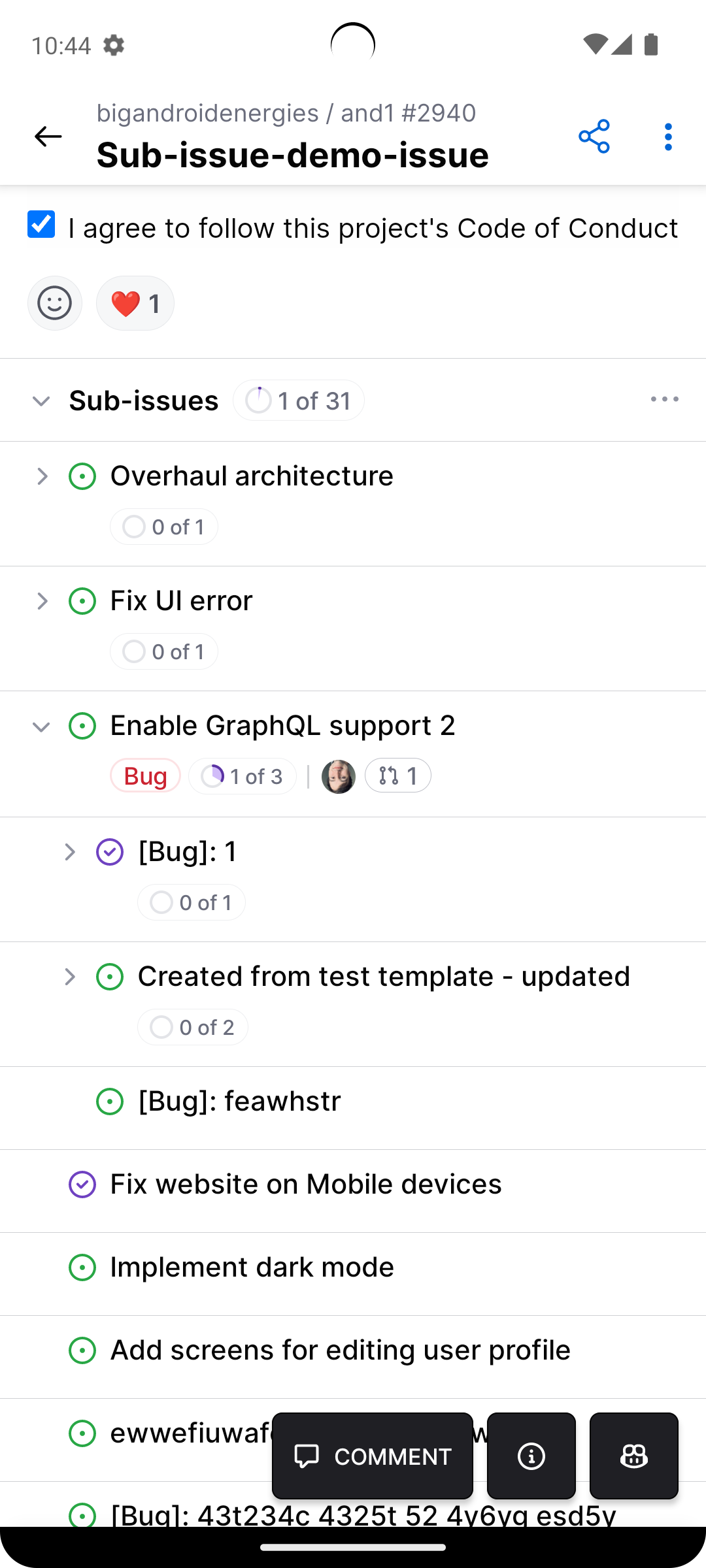
- Introducing sub-issues on GitHub Mobile. Track progress and understand remaining work within a parent-child hierarchy on the go.
- Review your notification preferences: from time to time, we’ll ask that you check in on your notification preferences to ensure that you’re receiving the kinds of notifications you want, at times you want to receive them.
| Copilot Extensions | Sub-issues |
|---|---|
 |
 |
iOS bug fixes:
- Widgets reflect the accent color when tinted.
- Add reactions to the latest release in the Releases view.
- Inbox swipe actions get dismissed before entering batch selection mode.
- In the Explore view, avatars load correctly with transparent background.
- In the Issue view, remove an extra animation when data loads.
- Navigate content in the Explore view’s “For You” feed using assistive technologies.
- Pull request reviews from Copilot code review show the “Copilot” brand name.
- Clearing a field used for a grouping within a project re-groups content without duplicate group titles.
- Fixed an issue where the search bar was improperly updated during text input with marked text in Japanese or Chinese input methods.
- Fixed an issue where pull-to-refresh in discussions failed to refresh data and the loading indicator remained stuck.
- The pull request widget responds to user specified tints.
- Issues in archived repositories no longer show update actions.
- Code vulnerability alerts in Copilot chat are no longer duplicated.
- Indented code blocks in Copilot chat display within a chat response.
- Nested lists in markdown content display with less indentation when viewed with larger text sizes.
- Issue and pull requests display their issue or pull request number when scoped to a single repository.
- Shortcuts scoped to a single repository will no longer list the repository name for each issue or pull request.
Android bug fixes:
- Improved scrolling performance for lists where list items contains web views.
- The correct default commit message now appears when creating a new file in a repository.
- Improved line wrapping in the Code view.
- Various sub-issues design tweaks and improvements.
- Fixed file header appearance in pull request reviews.
- Pull request reviews now display the correct submission date.
- Anchor links in markdown files will now scroll to the correct position.
- The delete branch button will now be shown after closing a pull request.
- Bots are now mentionable in pull request reviews if they are the author.
Learn more about GitHub Mobile and share your feedback to help us improve.
Join the discussion within GitHub Community.