Release
Copilot Immersive update for Copilot Enterprise customers
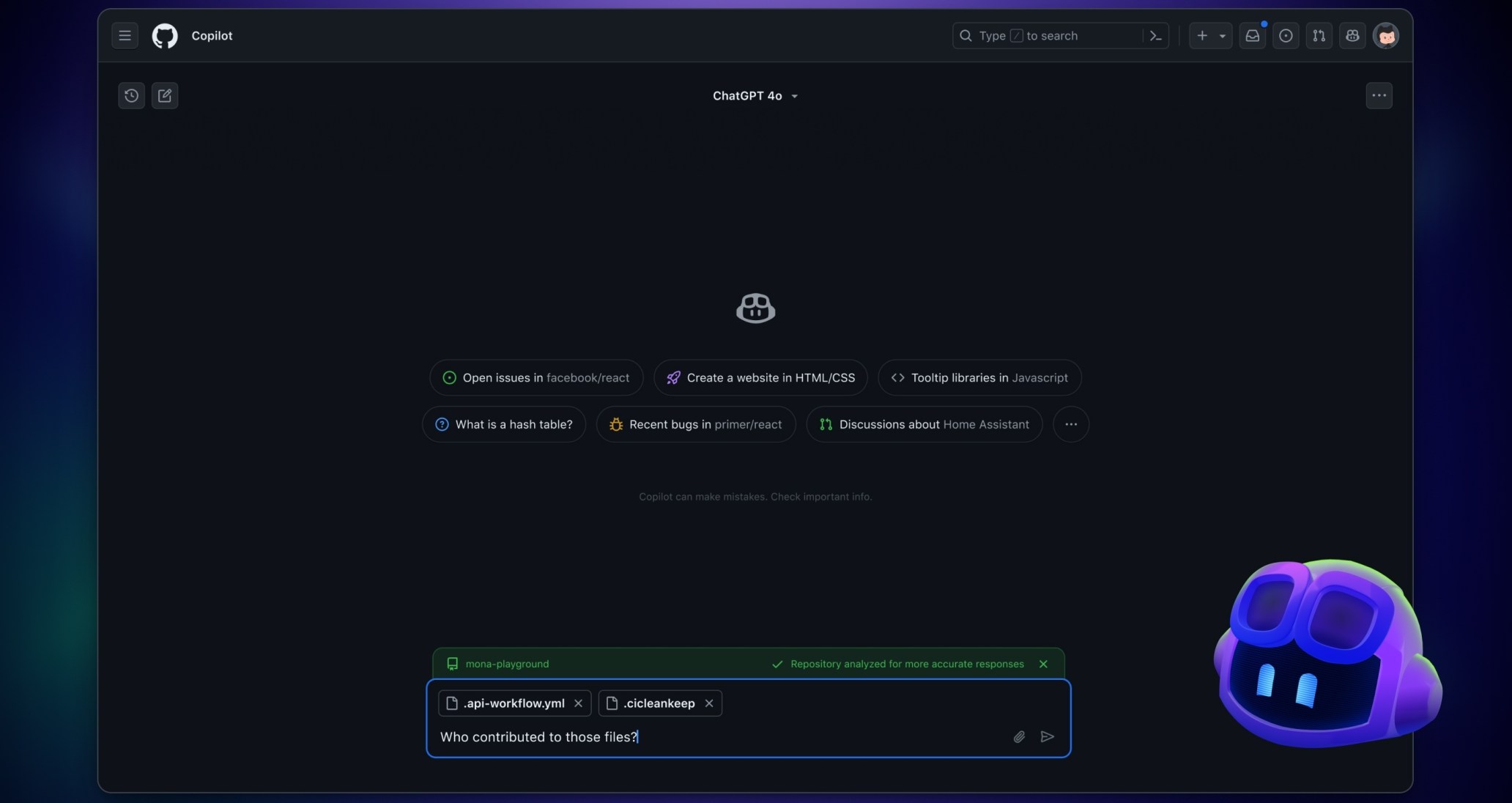
We’ve enhanced the fullscreen Copilot chat experience on github.com/copilot with a streamlined UI and an even easier way to handle context:
- Effortlessly see and navigate previous conversations with a new collapsible sidebar
- Dynamically set and remove repository context to suit your workflow
- Manage all your resources seamlessly in a unified attachment menu
These updates are available in preview for Copilot Business and Copilot Individual users. Check out the updates, and let us know what you think using the in-product feedback option.