Improvement
Global Navigation Optimizations
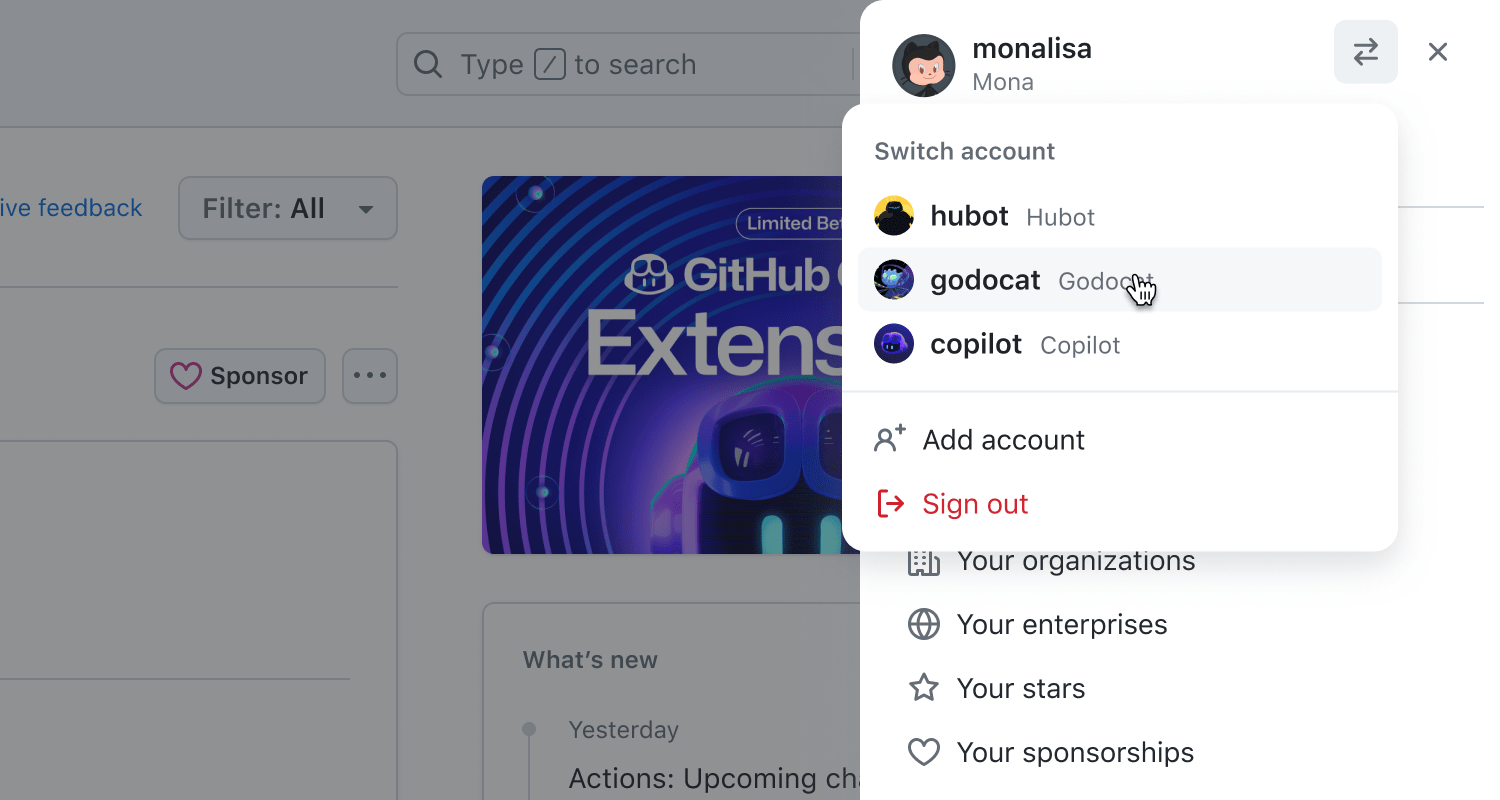
Improvements to GitHub’s global navigation:
– We’ve optimized parts of the global navigation to load up to 25% faster, enhancing your overall experience.
– Switching between accounts is now more seamless and efficient.