Improvement
Pinned gists
You can now pin your gists to your profile. Feature your favorite gists alongside your favorite repos!
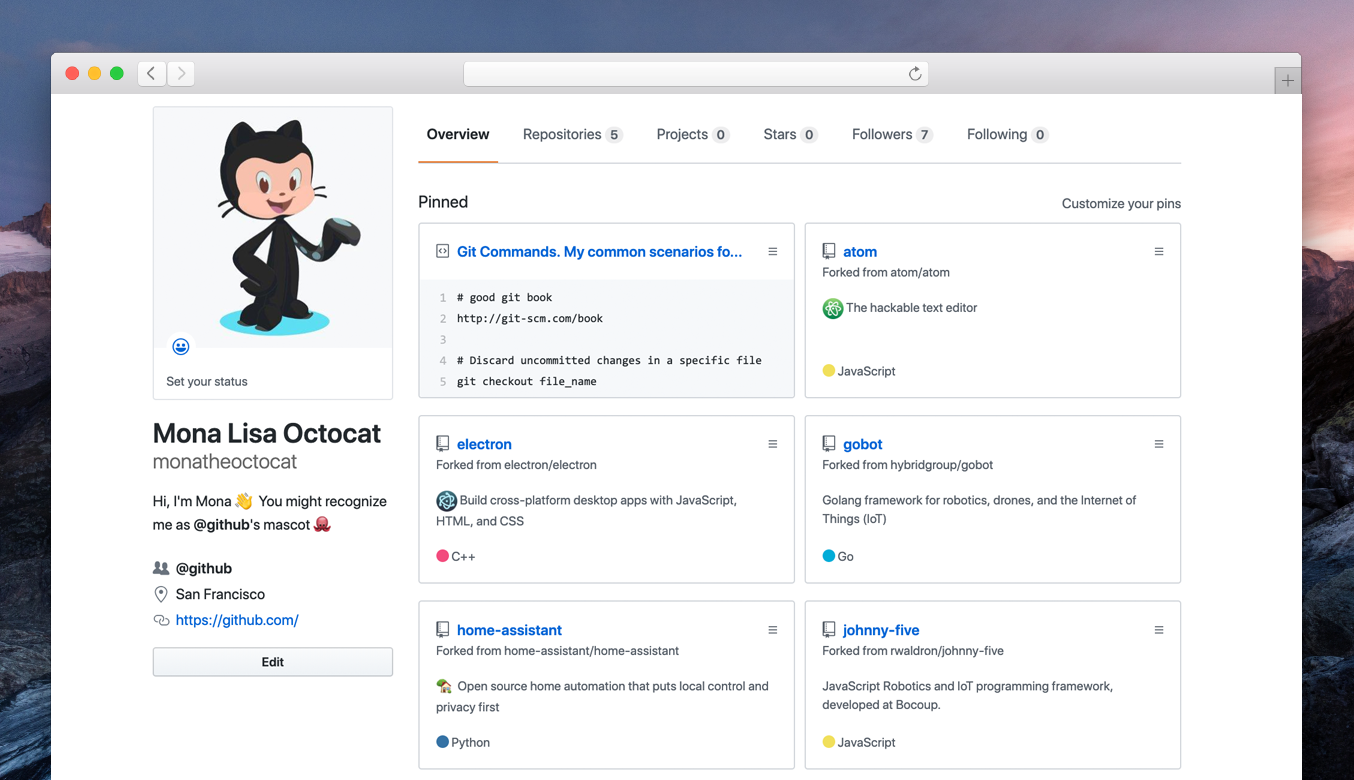
You can now pin your gists to your profile. Feature your favorite gists alongside your favorite repos!

Discover tips, technical guides, and best practices in our biweekly newsletter just for devs.