
3 ways to get Remote Code Execution in Kafka UI
In this blog post, we’ll explain how we discovered three critical vulnerabilities in Kafka UI and how they can be exploited.
Resources for securing your supply chain, building more secure applications, and staying up-to-date with the latest vulnerability research. Get comprehensive insights into the latest security trends—and news from the GitHub Security Lab. You can also check out our documentation on code security on GitHub to find out how to keep your code and applications safe.

In this blog post, we’ll explain how we discovered three critical vulnerabilities in Kafka UI and how they can be exploited.

In this post, I’ll exploit CVE-2024-3833, an object corruption bug in v8, the Javascript engine of Chrome, that allows remote code execution (RCE) in the renderer sandbox of Chrome by a single visit to a malicious site.

Can an attacker execute arbitrary commands on a remote server just by sending JSON? Yes, if the running code contains unsafe deserialization vulnerabilities. But how is that possible? In this blog post, we’ll describe how unsafe deserialization vulnerabilities work and how you can detect them in Ruby projects.

Let’s take a look at 10 key moments from the first decade of the GitHub Security Bug Bounty program.

GitHub is working with the OSS community to bring new supply chain security capabilities to the platform.
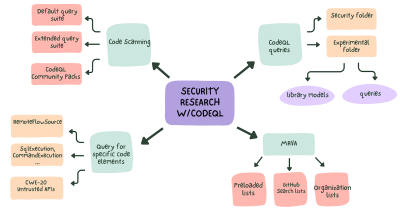
Learn how to use CodeQL for security research and improve your security research workflow.

We’ve dramatically increased 2FA adoption on GitHub as part of our responsibility to make the software ecosystem more secure. Read on to learn how we secured millions of developers and why we’re urging more organizations to join us in these efforts.

This blog post is an in-depth walkthrough on how we perform security research leveraging GitHub features, including code scanning, CodeQL, and Codespaces.

In this post, I’ll look at CVE-2023-6241, a vulnerability in the Arm Mali GPU that allows a malicious app to gain arbitrary kernel code execution and root on an Android phone. I’ll show how this vulnerability can be exploited even when Memory Tagging Extension (MTE), a powerful mitigation, is enabled on the device.

Repo-jacking is a specific type of supply chain attack. This blog post explains what it is, what the risk is, and what you can do to stay safe.

In practice, shifting left has been more about shifting the burden rather than the ability. But AI is bringing its promise closer to reality. Here’s how.

Consider deploying the GitHub Action: Evergreen so that you know each of your repositories are leveraging active dependency management with Dependabot.

The GitHub Security Lab teamed up with Ekoparty once again to create some challenges for its yearly Capture the Flag competition!

Learn about how we run a scalable vulnerability management program built on top of GitHub.

This blog post describes two linked vulnerabilities found in Frigate, an AI-powered security camera manager, that could have enabled an attacker to silently gain remote code execution.
Build what’s next on GitHub, the place for anyone from anywhere to build anything.
Last chance: Save $700 on your IRL pass to Universe and join us on Oct. 28-29 in San Francisco.