Justin Hutchings
Director of Product Management for supply chain security. I manage the team that's behind Dependabot, the Advisory Database, and the dependency graph. Twitter: https://twitter.com/jhutchings0
These days software is subject to an ever-changing threat landscape. Check out the many ways you can keep your projects secure on GitHub today.

We’ve been blogging a lot lately about different things that you can do to help improve security for your projects. You might have seen recent blogs, like this one on end-to-end supply chain security from my colleague @steiza, or this one from @15mariams about how to prevent secret leaks with GitHub Advanced Security. With today’s evolving threat landscape, it can be tough to stay on top of all the different things you need to do to keep ahead of the ever-changing threat landscape.
A couple of years ago, we did some research as part of the Octoverse report about dependency security, and one statistic stood out in my mind. The median JavaScript project on GitHub uses just 10 open source dependencies directly. That’s probably not surprising if you’ve written any JavaScript lately, but what is surprising is that the same repository ends up with 683 transitive dependencies that are pulled in as dependencies of the set of 10 direct dependencies they chose.
The sheer number of dependencies that most projects are using means that if you’re not leveraging automation to stay on top of the security risks from your dependency tree, then chances are you’re already vulnerable. While most security vulnerabilities are not malicious, they’re from accidental coding mistakes, they can still open the door for malicious actors to go after your users or their data.
GitHub provides a number of tools, which are built-in and designed to help you manage your dependency tree, including the dependency graph and dependency review. For each repository, the dependency graph shows the dependencies, dependents, ecosystems, and packages that each dependency relies on.
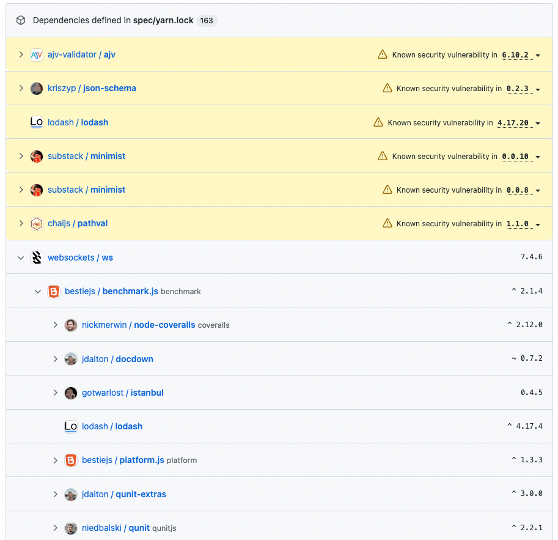
Learn more about how to interact with your dependency graph.
Dependency review allows you to quickly understand your dependencies before you introduce them into your project. As part of a pull request, you can see what you’re introducing, changing, or removing, as well as the information about the vulnerabilities, age, license, and usage.
Dependency review gives you:
Learn more about dependency review.
Having this instant snapshot and review of your dependencies in your project gives you the power to act, which is where Dependabot comes in. With Dependabot, not only can you catch vulnerable dependencies, but you can fix them as well. It automatically checks your dependency files for outdated requirements and opens individual pull requests for any it finds. It then notifies you and suggests fixes—enabling you to always work on the latest, most secure releases.
Dependabot alerts can be enabled on your public and private repositories. You can also customize notifications, so you only receive the alerts you want and nothing more. Additionally, you can see all of the alerts that affect a particular project in your security tab or in your dependency graph.
How do I turn on Dependabot?

Learn how we are using the newly released GitHub Security Lab Taskflow Agent to triage categories of vulnerabilities in GitHub Actions and JavaScript projects.

Announcing GitHub Security Lab Taskflow Agent, an open source and collaborative framework for security research with AI.

Learn why some long-enrolled OSS-Fuzz projects still contain vulnerabilities and how you can find them.