Keep all your packages up to date with Dependabot
Keeping your dependencies updated is one of the easiest ways to keep the software you build secure. However, while it’s critically important to keep your dependencies updated, in a recent…

Keeping your dependencies updated is one of the easiest ways to keep the software you build secure. However, while it’s critically important to keep your dependencies updated, in a recent survey, 52% of developers said they find it painful1. Dependabot alleviates that pain by updating your dependencies automatically, so you can spend less time updating dependencies and more time building. Up until now, the Dependabot features we’ve brought to GitHub have focused on automated security updates, which update packages that have known vulnerabilities.
Today, we’re taking the next step and announcing Dependabot version updates, which keep all of your packages updated on a regular basis.
Keep all your dependencies updated
Version updates regularly update all the packages used by your repository, even if they don’t have any known vulnerabilities. To enable version updates, check a dependabot.yml configuration file into your repository.
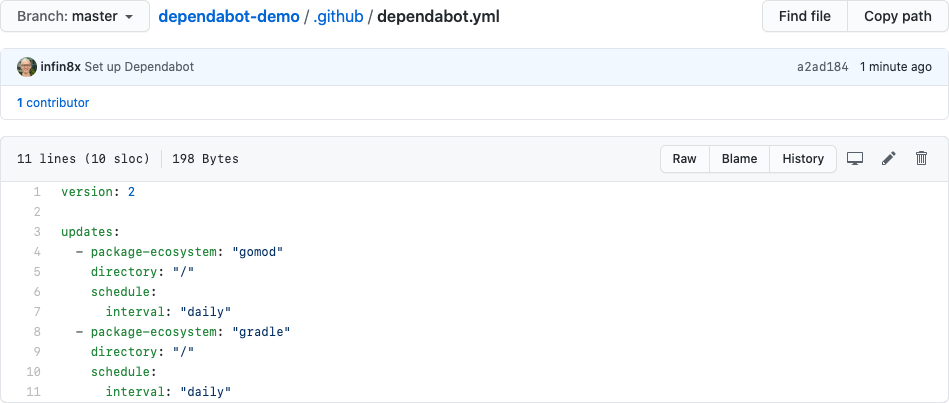 Your configuration file tells Dependabot the kind of dependency you want to update (like Go modules or npm packages), where the dependency manifest is located, and how often you want Dependabot to look for updates. On the schedule you specify, Dependabot will check if new versions are available. If updates are available, Dependabot sends pull requests to update your dependency manifest with the new versions.
Your configuration file tells Dependabot the kind of dependency you want to update (like Go modules or npm packages), where the dependency manifest is located, and how often you want Dependabot to look for updates. On the schedule you specify, Dependabot will check if new versions are available. If updates are available, Dependabot sends pull requests to update your dependency manifest with the new versions.
“GitHub’s integration of Dependabot has made keeping dependencies up to date in our Go project trivial. We know that staying up to date with dependencies is important for security, and GitHub has made it easier than ever for teams to adopt.”
– Alex Gaynor, Chief Information Security Officer at Alloy
Dependabot version updates are in public beta, and you can start using them today.
Stop using vulnerable dependencies: Dependabot alerts and security updates
When you check in an insecure dependency, or a new vulnerability is discovered in a dependency you already have, we already let you know with security alerts for vulnerable dependencies. This system also powers our automated security updates, which we announced last November. GitHub users have merged more than 776,000 automated security update pull requests since the announcement.
With the launch of version updates, security alerts for vulnerable dependencies and automated security updates have new names: Dependabot alerts and Dependabot security updates. None of the goodness has changed, and they still work the same way. GitHub watches the National Vulnerability Database and other sources for vulnerabilities in open source packages. If Dependabot finds a vulnerability in a package you depend on, it sends you an alert. If it can suggest a fix, it also sends a pull request to update your dependency manifest with the closest non-vulnerable version.
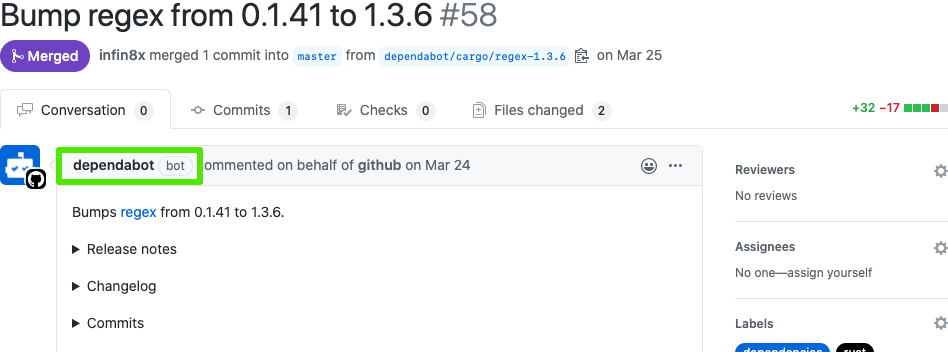
If you’ve merged a pull request that looks like this, from the dependabot bot, you’ve already enabled Dependabot security updates.
If you haven’t already enabled Dependabot alerts or Dependabot security updates, or want to check if they’re enabled, you can do it now by going to your repository’s Settings page. Click the new Security & analysis tab on the left, and then click Enable next to Dependabot alerts and Dependabot security updates.

Moving forward from Dependabot.com and dependabot-preview
If you use Dependabot.com to manage how Dependabot works in your repository, or have pull requests in your repository from dependabot-preview, you can take advantage of the benefits of version updates with a quick upgrade.
Upgrading from dependabot-preview to GitHub-native Dependabot requires two steps: enabling security updates and enabling version updates.
To enable Dependabot security updates, go to your repository’s Settings page, click the new Security & analysis tab on the left, and then click Enable next to Dependabot security updates. You can also check on this tab if they’re already enabled. Security updates are already enabled on most repositories.
To enable Dependabot version updates, look for a pull request with the updated configuration file in the next few days, or use the Update config file button in your Dependabot.com dashboard to create a pull request now.
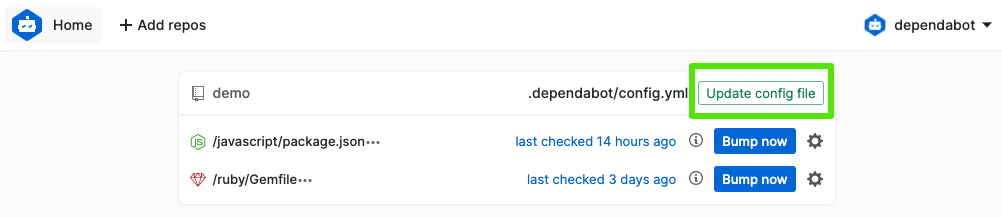
In GitHub-native Dependabot, all configuration of version updates is done via the configuration file. This file is very similar to the dependabot-preview configuration file, but we’ve made a few changes and improvements that will be automatically included in the update pull request. You can see the update logs that used to be on the Dependabot.com dashboard by going to your repository’s Insights page, clicking the Dependency graph tab on the left, and then clicking Dependabot.
Keeping dependencies updated is a crucial part of securing your software supply chain, whether you’re working on an open source project or a large enterprise. To make that easy, we’re sticking to our promise to make all Dependabot features free for every repository on GitHub.
1 2019 State of the Software Supply Chain Report, Sonatype.
Tags:
Written by
Related posts

GitHub availability report: January 2026
In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Pick your agent: Use Claude and Codex on Agent HQ
Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What the fastest-growing tools reveal about how software is being built
What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.