GitHub Advisory Database now open to community contributions
Anyone can now provide additional information to further the community’s understanding and awareness of security advisories.

The world of open source security is fast moving, with new vulnerabilities and different attack vectors driving the community to continuously seek to learn more. GitHub has teams of security researchers that review all changes and help keep security advisories up to date, but often there are community members with additional insights and intelligence on CVEs that do not have a place to share this knowledge.
GitHub believes that free and open security data is critical to empowering the industry as a whole to best secure our software supply chains.
Today, we are excited to announce that the GitHub Advisory Database is now open to community contributions! GitHub is publishing the full contents of the Advisory Database to a new public repository to make it easier for the community to benefit from this data. We’ve also built a user interface for making contributions, which is documented below. The data is licensed under a Creative Commons license, and has been since the database’s inception, making it forever free and usable by the community.
The GitHub Advisory Database is maintained by a dedicated team of full-time curators and powers the security audit experience for npm and NuGet, as well as GitHub’s own Dependabot alerts. By making it easier to contribute to and consume, we hope it will power even more experiences and will further help improve the security of all software.
How to contribute to a security advisory
With community contributions, security researchers, academics, and enthusiasts will now be able to provide additional information and context to further the community’s understanding and awareness of security advisories. To provide a community contribution to a security advisory, navigate to the advisory to which you wish to contribute to, and submit your research through the “suggest improvements for this vulnerability” workflow. In the following form, you can suggest changes or provide more context on packages, affected versions, impacted ecosystems, and more.
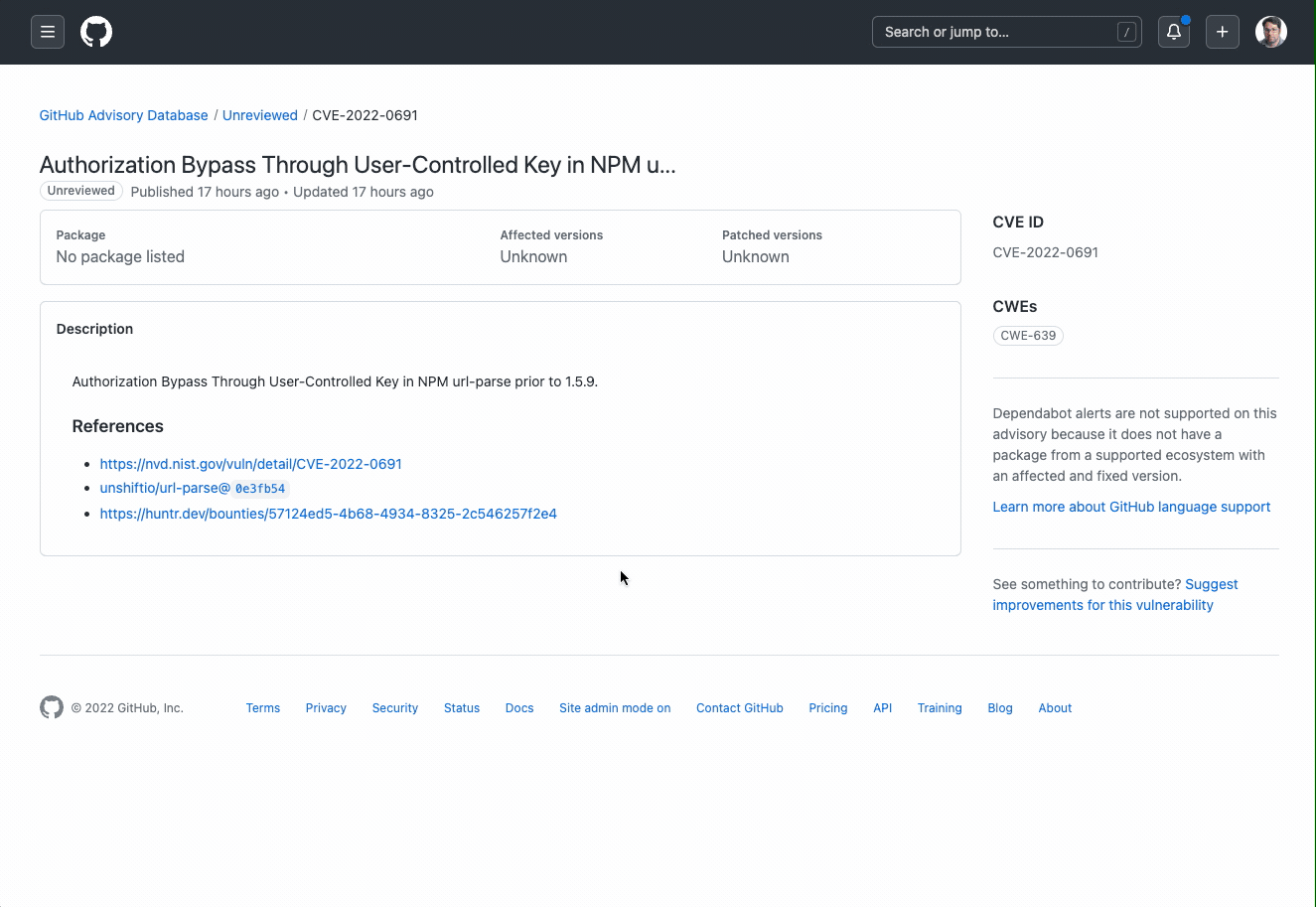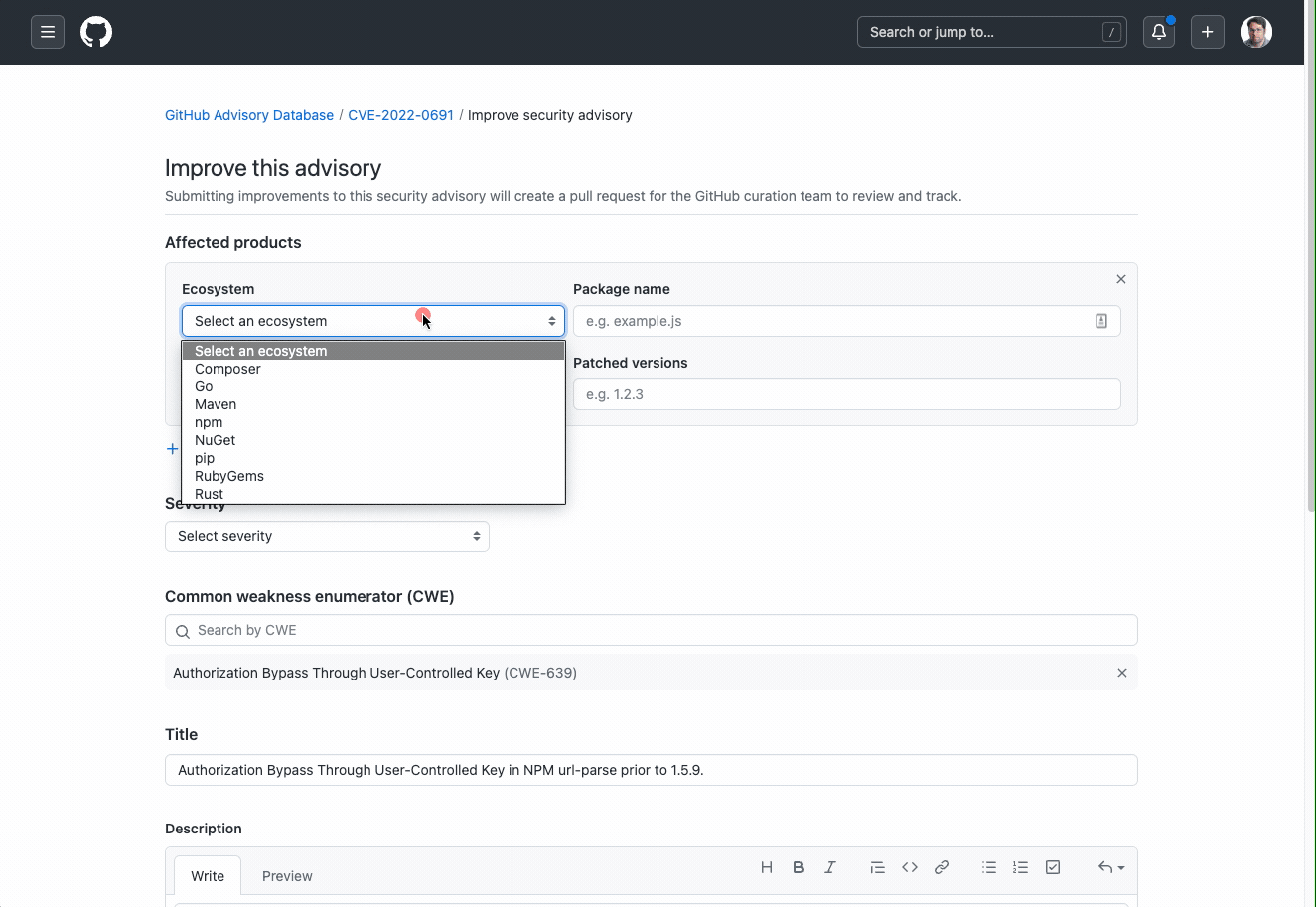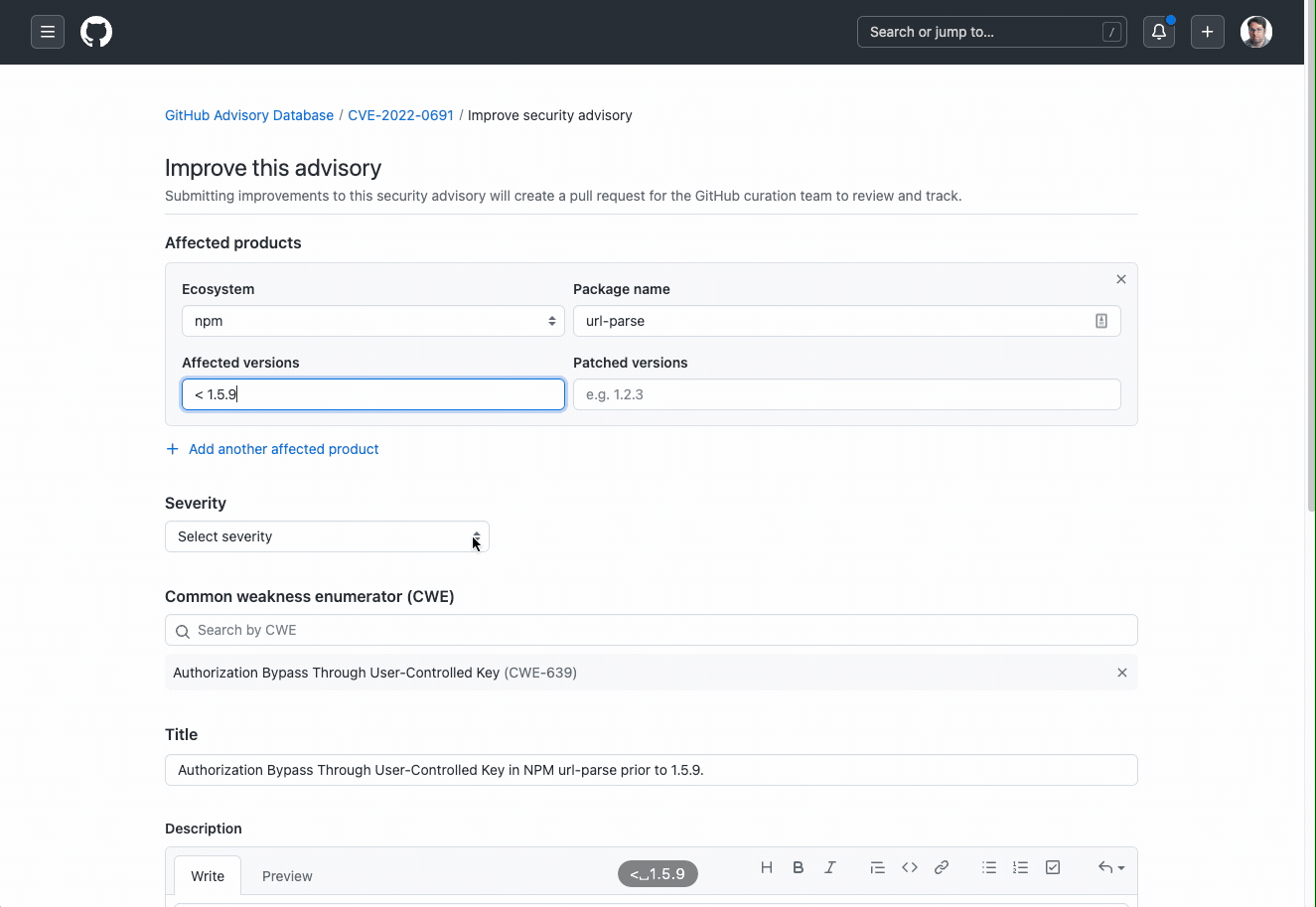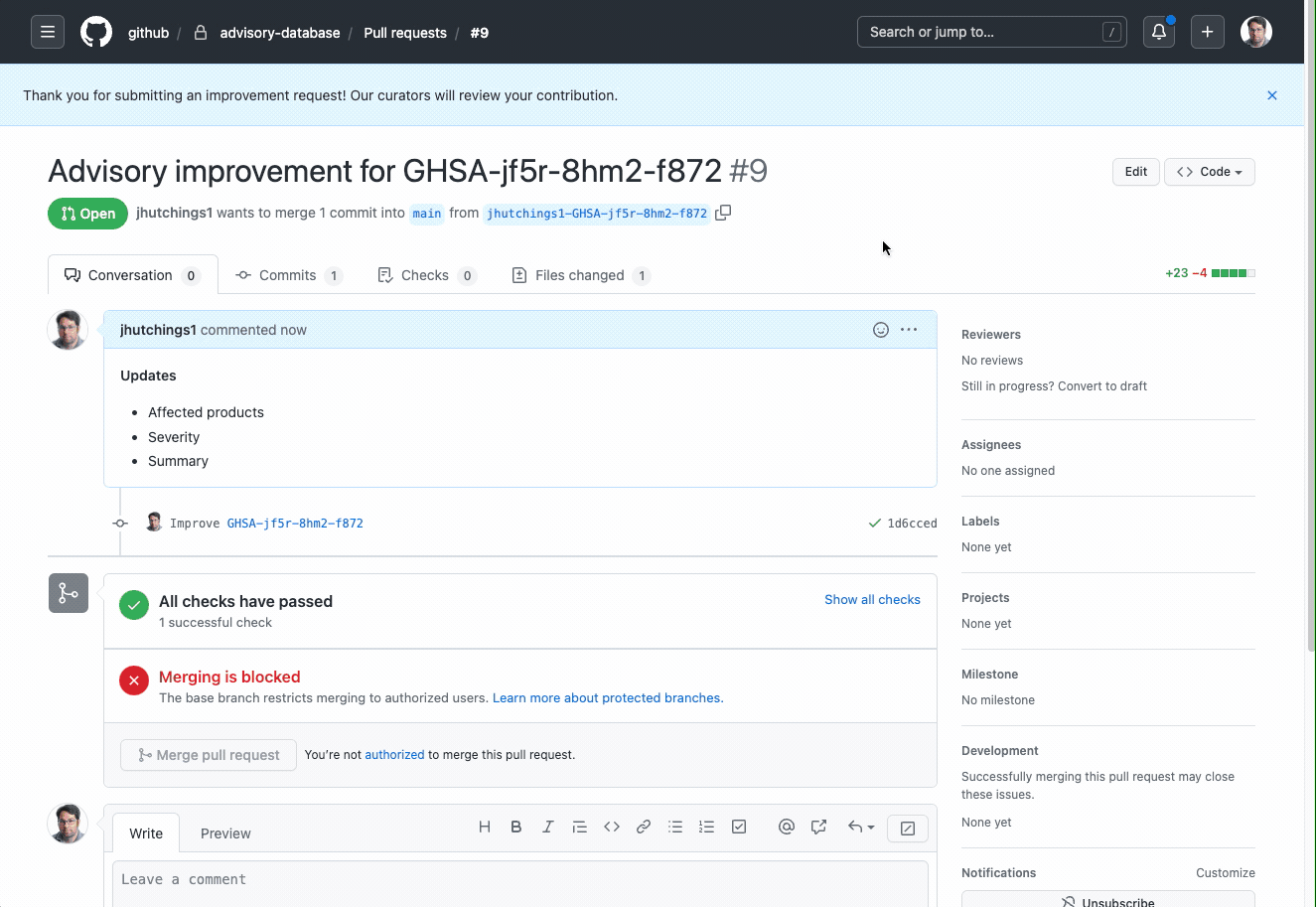
To complete your submission, the form will walk you through opening a pull request that details your suggested changes. Once the pull request is open, security researchers from the GitHub Security Lab, as well as the maintainer of the project who filed the CVE (if known), will be able to review your request. Contributors will get public credit on their GitHub profile once their contribution is merged!
Advisory Database format
In the spirit of furthering interoperability, advisories in the GitHub Advisory Database repository use the Open Source Vulnerabilities (OSV) format. “In order for vulnerability management in open source to scale, security advisories need to be broadly accessible and easily contributed to by all,” said Oliver Chang, software engineer for Google’s Open Source Security Team. “OSV provides that capability.”
Learn more about GitHub supply chain security
The GitHub Advisory Database is the foundation of GitHub’s supply chain security capabilities, including Dependabot alerts and Dependabot security updates. If you have a security vulnerability in an open source repository that you maintain, the built-in security advisories feature in every GitHub open source repository can help.
For more information about our supply chain security capabilities, check out the following pages:
- Learn about managing vulnerable dependencies on GitHub
- Visit the GitHub Advisory Database
Tags:
Written by
Related posts

AI-supported vulnerability triage with the GitHub Security Lab Taskflow Agent
Learn how we are using the newly released GitHub Security Lab Taskflow Agent to triage categories of vulnerabilities in GitHub Actions and JavaScript projects.

Community-powered security with AI: an open source framework for security research
Announcing GitHub Security Lab Taskflow Agent, an open source and collaborative framework for security research with AI.

Bugs that survive the heat of continuous fuzzing
Learn why some long-enrolled OSS-Fuzz projects still contain vulnerabilities and how you can find them.