Securing your open source dependencies with GitHub dependency insights
GitHub dependency insights helps both developers and security teams manage their open source security with confidence—automatically compiling relevant CVE information, aiding in OSS license compliance, and helping them better understand their OSS dependency versions.

Handling your company’s open source security and open source dependencies can be challenging. Managing open source CVEs, staying compliant with open source software (OSS) licenses, or just keeping track of what dependency version you’re using can quickly consume time away from development, and can leave security teams to manually manage the risk of vulnerable OSS code.
GitHub’s dependency insights can solve these challenges, and provide a clean overview of your open source dependencies on GitHub.
Understanding your open source usage
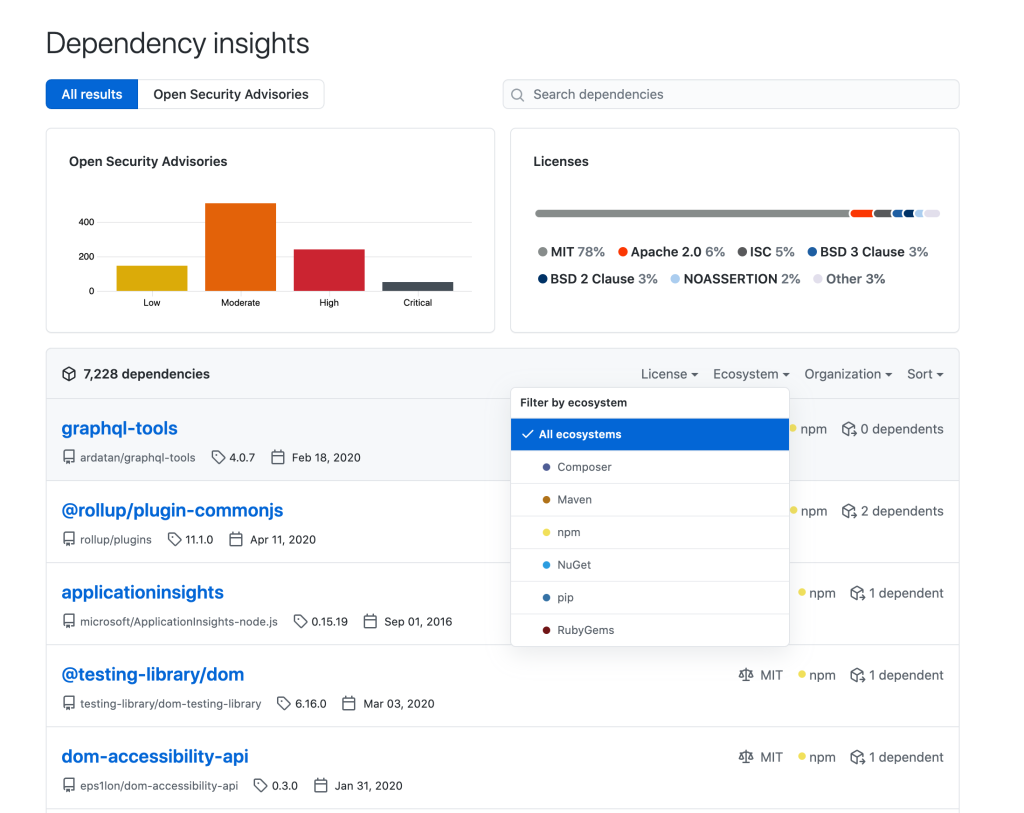
To start, GitHub’s dependency insights compiles all of your OSS dependencies across the repositories in your organizations. In this view, you have various filtering options to drill into—like the dependency ecosystem, license type, or a particular GitHub organization you’re a member of.
This open source dependency data is pulled from your Dependency Graph, currently covering Javascript, Ruby, Python, Java, Scala, PHP, and .NET dependencies across GitHub.com.
Staying license compliant
Understanding and maintaining license compliance is an increasingly hard problem to solve for companies in both regulated industries, and those wanting to mitigate the challenge of using a non-compliant OSS license.
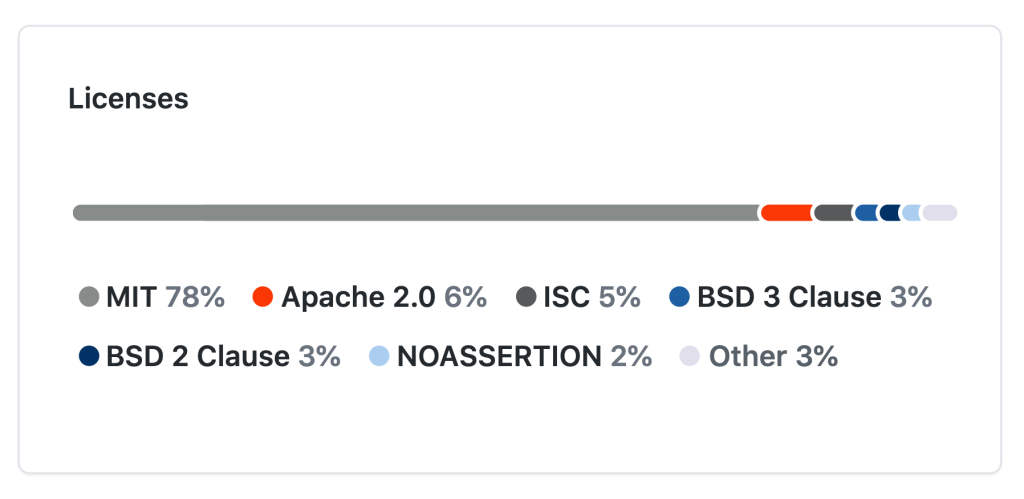
With dependency insights, GitHub compiles all of your OSS licenses in use, along with a histogram to help understand the frequency breakdown between each license type in your repositories. This makes it easy to see all the OSS licenses you have, and avoid any other license usage that might introduce new risk to your business.
GitHub Security Advisories
Just within the first page of dependencies insights, you can start to understand more about our organization’s OSS dependencies—however we haven’t covered the related open source security information that dependency insights can offer.
Within the Insights view, we can drill down into the GitHub Security Advisories we are vulnerable to. For example, by clicking on the high-risk advisories in the top left corner of this view, our dependency list updates to show the high-risk dependency versions, and how many advisories are associated with each package.
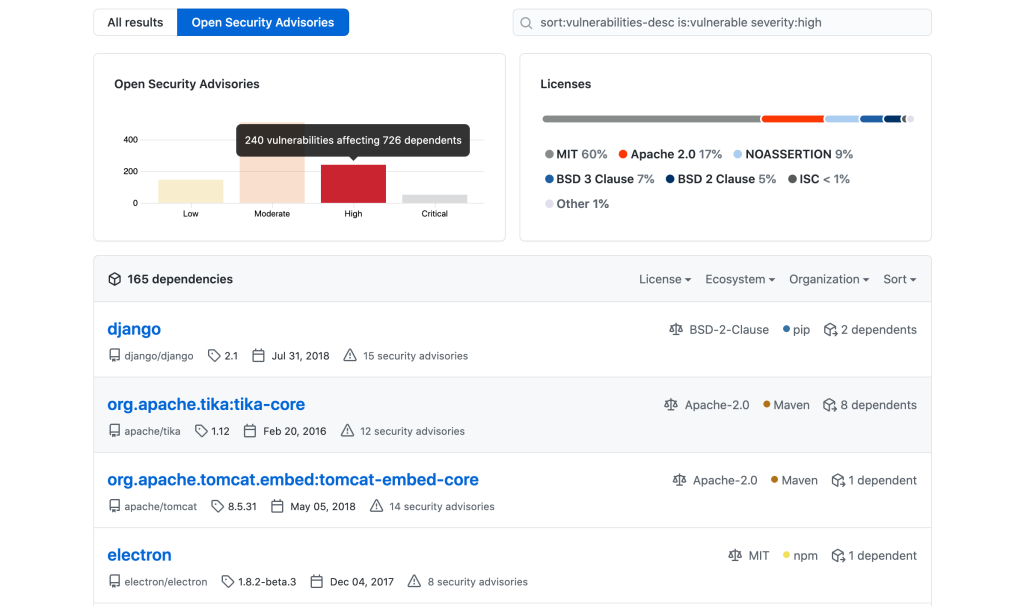
From here, a security team can tackle the most severe advisories first, and developers can better understand how secure their particular package versions are.
Viewing a vulnerable dependency version
If you click on a specific dependency in the Security Advisory list, we’ll land on an dependency overview page.

In this page, we can learn what that dependency does, the versions of it affected by CVEs, and its most recent updates from the maintainers. We can also use this information to dig one step further into our open source security—learning which of our repositories consume the vulnerable version of this dependency.
Remediating a vulnerability risk
In this example, we see a repository we own is vulnerable to various CVEs from a Django dependency version we’re referencing in our code.
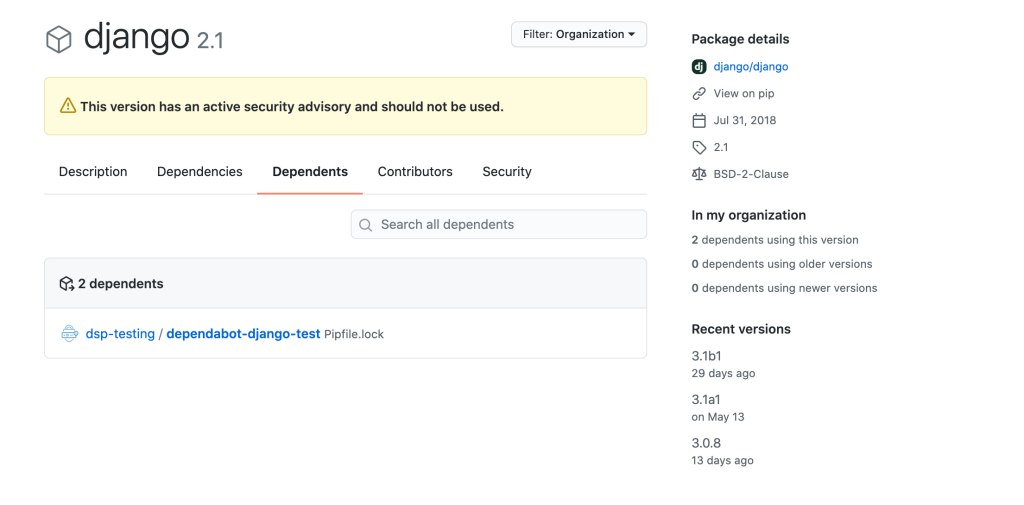
Navigating to this repository, we’ll see a pull request automatically generated from Dependabot that we can review to fix this vulnerable version.
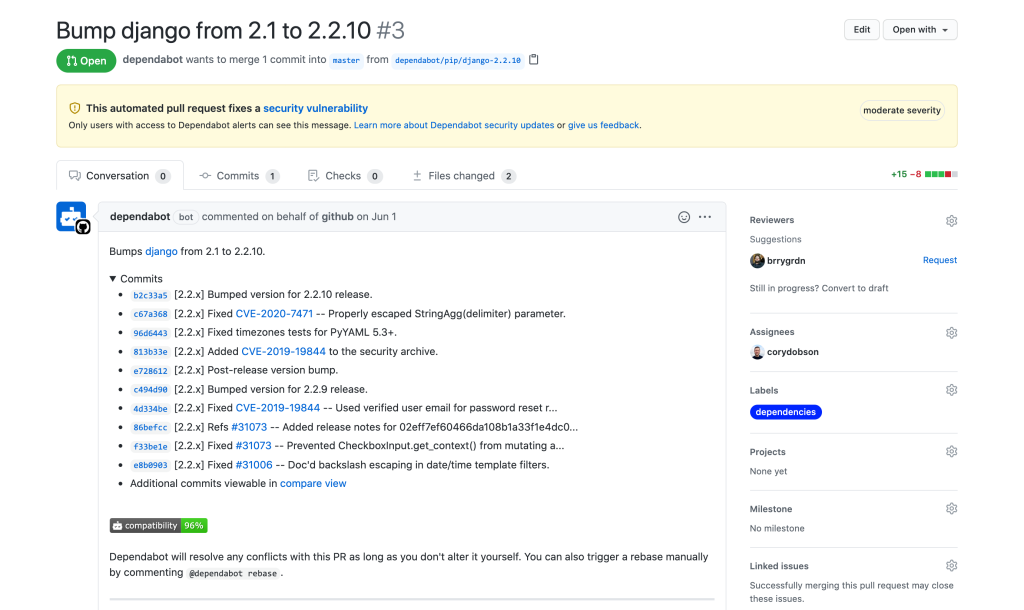
When GitHub detects a vulnerable dependency in your code, Dependabot creates a pull request to fix it. These automatic pull requests contain all the information needed to fix the vulnerability—including release notes from the OSS contributors, changelog entries, and Git commits. Dependabot also calculates a compatibility score for each pull request, letting you know if merging this pull request could potentially cause breaking changes in the project.
In this example, Dependabot calculated a high compatibility score, and the attached release notes from the OSS contributor give us confidence to merge the change, remediating the underlying CVE risk.
So with just a few clicks, we used GitHub dependency insights, Security Advisories, and Dependabot to narrow down and remediate a OSS security vulnerability from over 7000-plus OSS dependencies in our organization.
Looking to learn more?
Come see GitHub dependency insights in action during our next GitHub Demo Day on July 24, 2020 at 11am PT hosted by myself, and Glenn Wester of our Enterprise Solutions Engineering Team. Glenn and I will be digging deeper into dependency insights, and GitHub’s built-in DevSecOps workflows.
Want to start using GitHub to better secure your code?
Contact your account management team or the GitHub Sales Team to see how GitHub can help your engineering team build better, more secure software together.
Written by
Related posts

AI-supported vulnerability triage with the GitHub Security Lab Taskflow Agent
Learn how we are using the newly released GitHub Security Lab Taskflow Agent to triage categories of vulnerabilities in GitHub Actions and JavaScript projects.

Community-powered security with AI: an open source framework for security research
Announcing GitHub Security Lab Taskflow Agent, an open source and collaborative framework for security research with AI.

Bugs that survive the heat of continuous fuzzing
Learn why some long-enrolled OSS-Fuzz projects still contain vulnerabilities and how you can find them.