GitHub brings supply chain security features to the Rust community
The Rust community can now discover, report, and prevent security vulnerabilities.

GitHub’s supply chain security features help you understand what dependencies you use, be aware of vulnerabilities in those dependencies, and then patch them so you can get back to work. This helps keep your code secure. As the home for all developers, GitHub is enabling more projects to benefit from this functionality, and we now support the fastest growing language on GitHub: Rust. With the latest addition of Rust support in GitHub’s dependency graph, the entire suite of supply chain security features are available for Cargo files. Here’s an overview of what that looks like and what it means for you.
Advisories
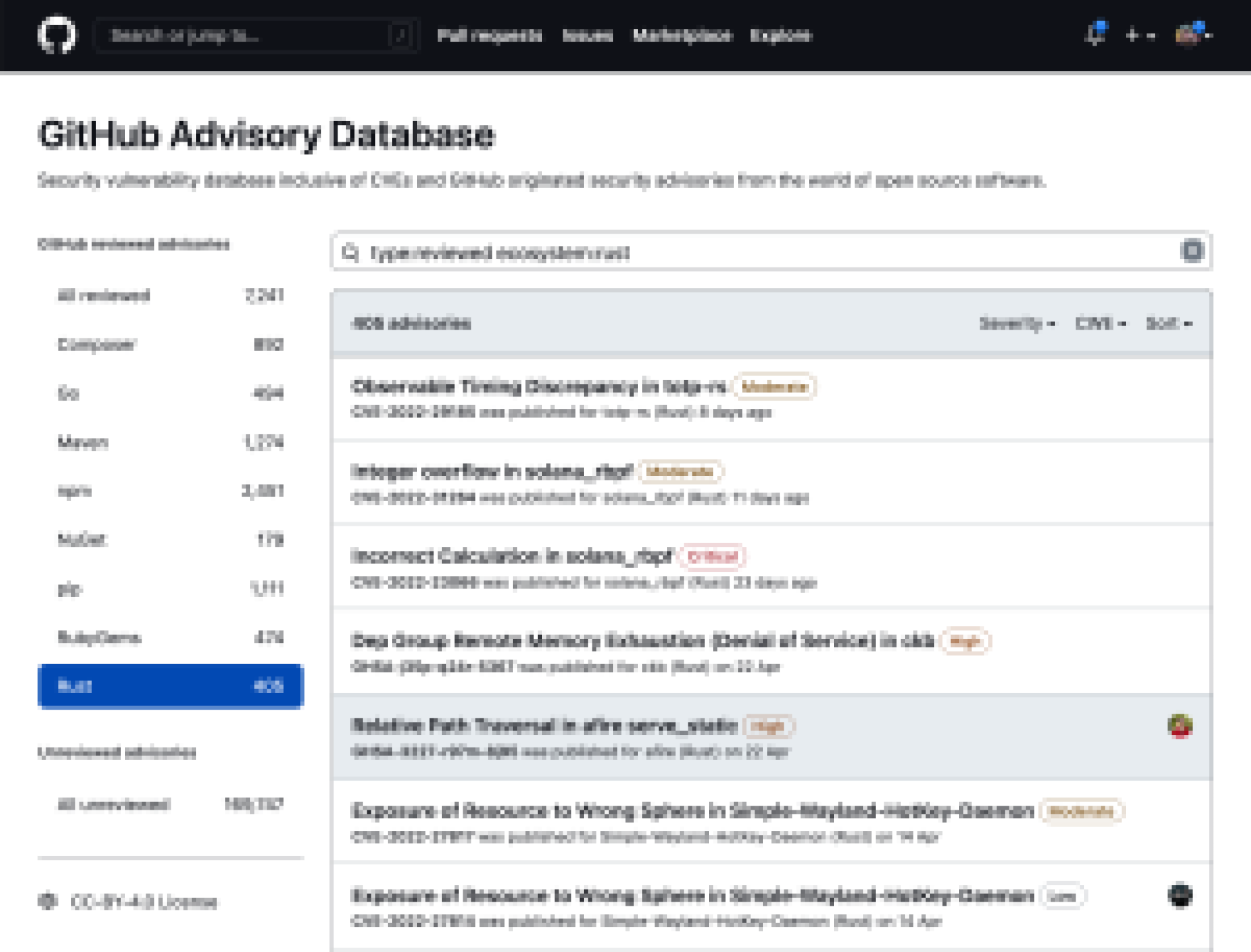
The GitHub Advisory Database is an open database of security advisories focused on high quality, actionable vulnerability information for developers. We’ve published over 400 existing Rust vulnerabilities, a number which grows as we curate existing vulnerabilities and triage newly discovered ones. The majority of these vulnerabilities come from RustSec, an independent organization that collects, standardizes, and publishes security advisories related to Rust libraries.
If you’re a Rust package maintainer, you can use GitHub Security Advisories to collaborate with vulnerability reporters to privately discuss and fix vulnerabilities before announcing them publicly. Additionally, if you’re aware of a Rust vulnerability with a CVE that isn’t in the GitHub Advisory Database you can report it through a community contribution.
Dependency graph
The dependency graph analyzes a repository’s Cargo.toml and Cargo.lock files to determine the dependencies being used in your project. This serves as a backbone for Dependabot, which alerts you when there is a known vulnerability and creates pull requests to update the affected dependency. To view a repository’s detected dependencies, select the repository’s Insights tab, then select Dependency graph from the sidebar on the left.
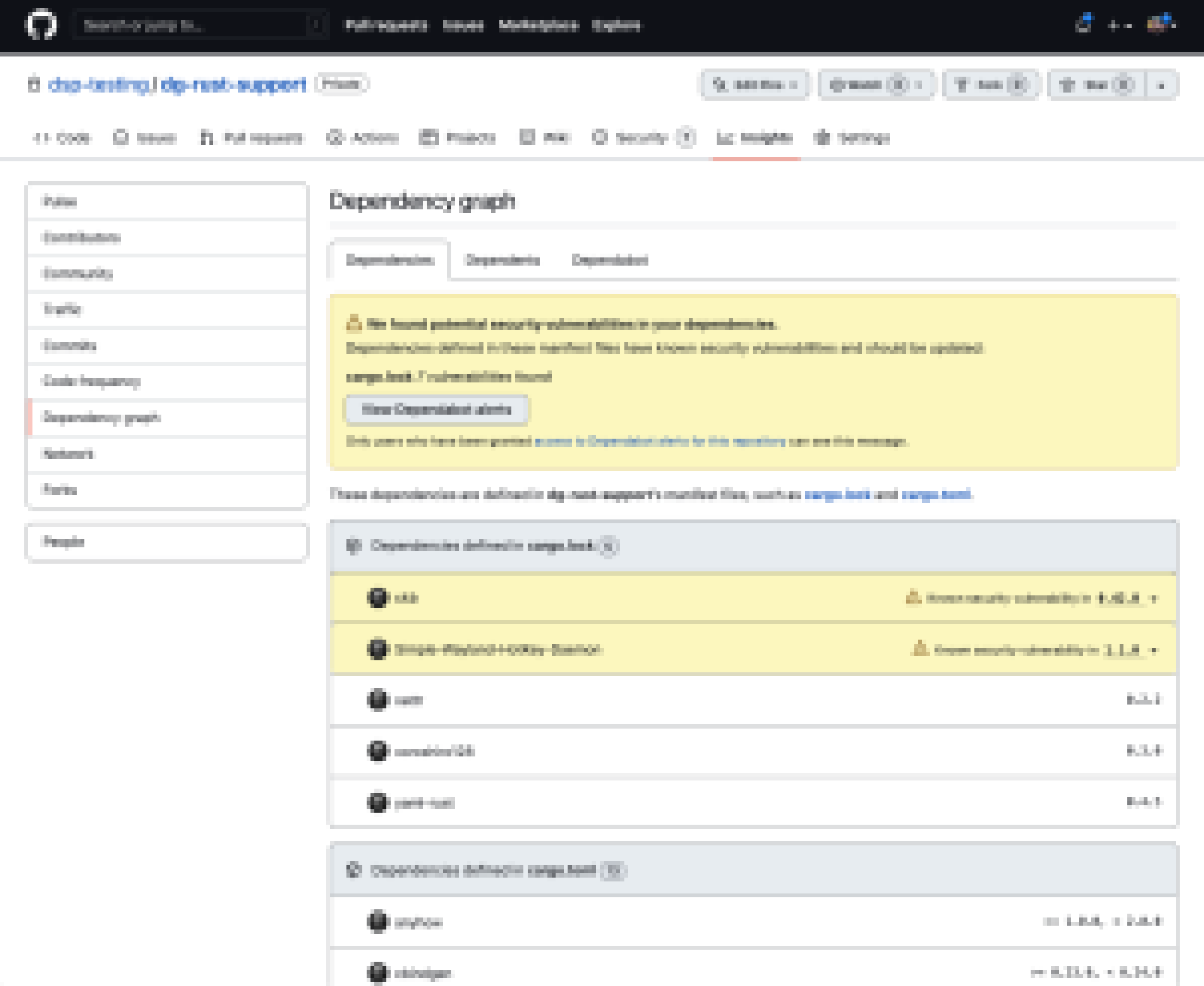
The dependency graph is enabled by default for public repositories, but you must enable it for private repositories. If the dependency graph for your public repository hasn’t already been populated, it will be soon. Please note that we’re rolling out dependency graph support for Rust in two phases, and full package metadata for Rust dependencies (including mapping the packages to GitHub repositories) is coming in a future release.
You can prevent Rust vulnerabilities from being introduced in the first place with the dependency review GitHub Action. This action scans pull requests for changes in your Rust dependencies and identifies if any new ones have known vulnerabilities. You can then block them from being merged into your code.
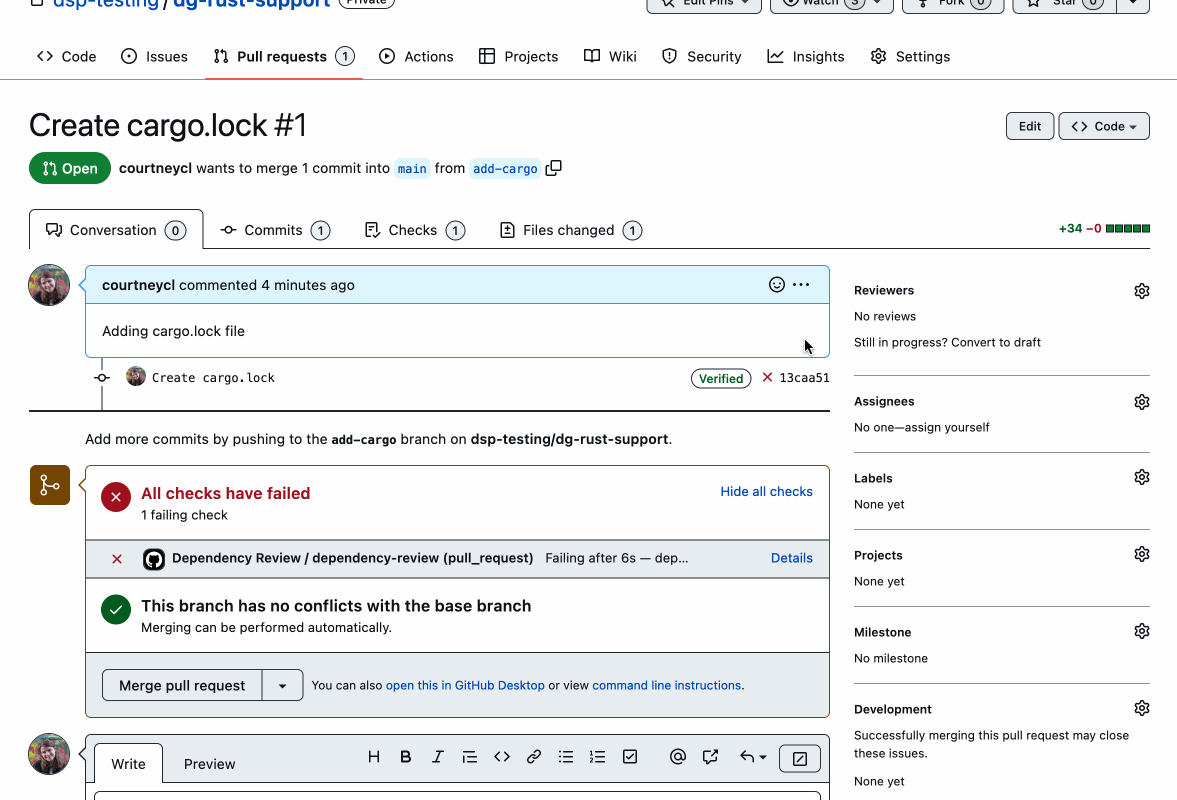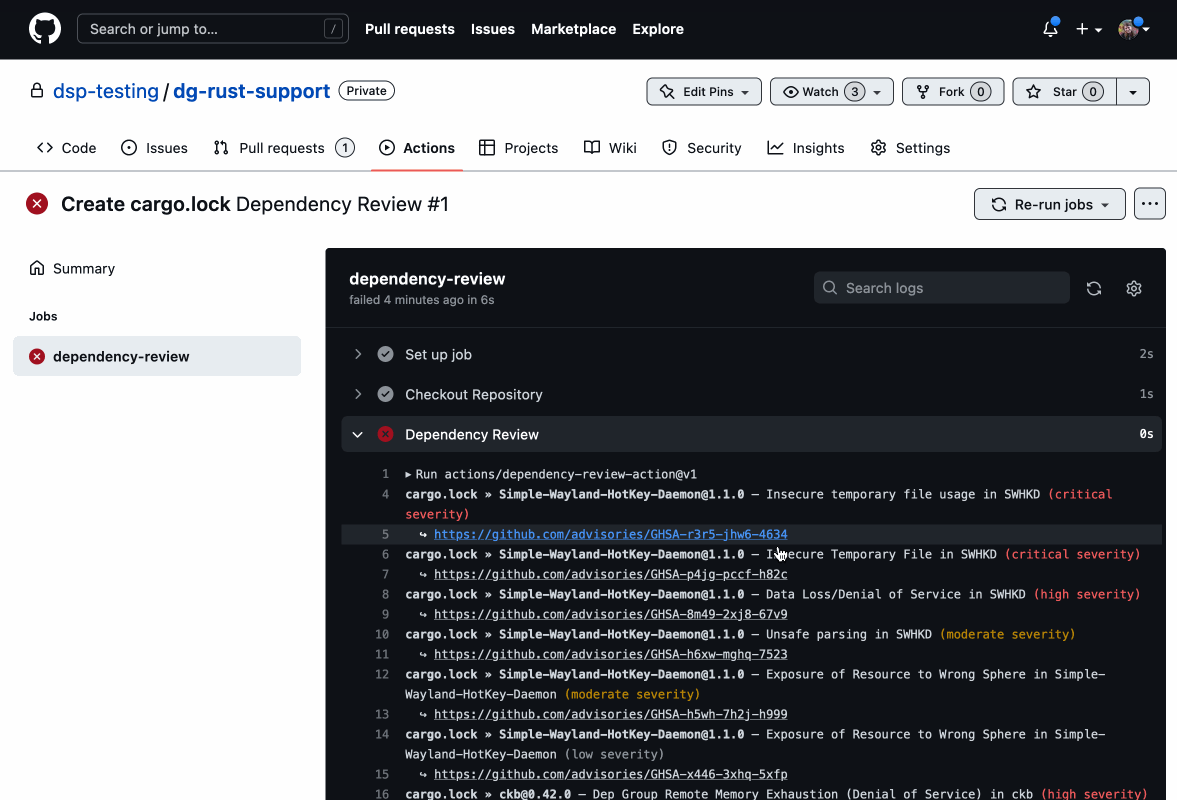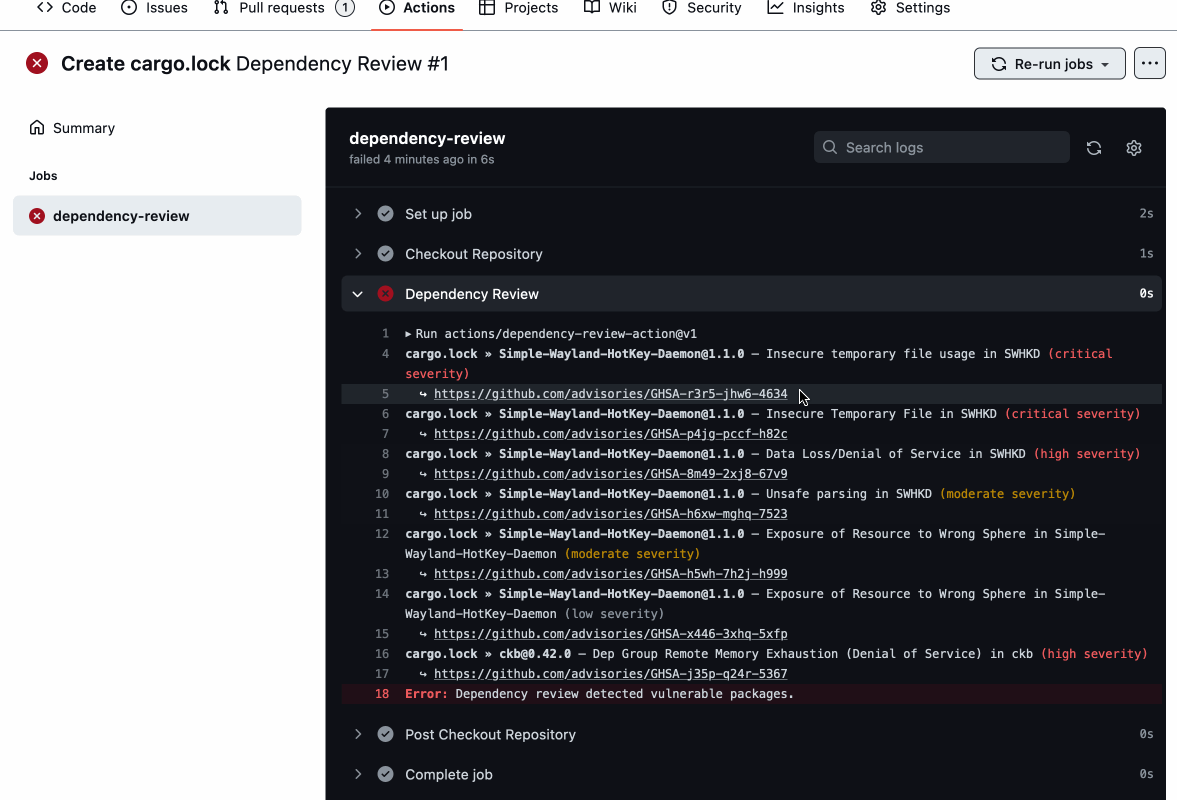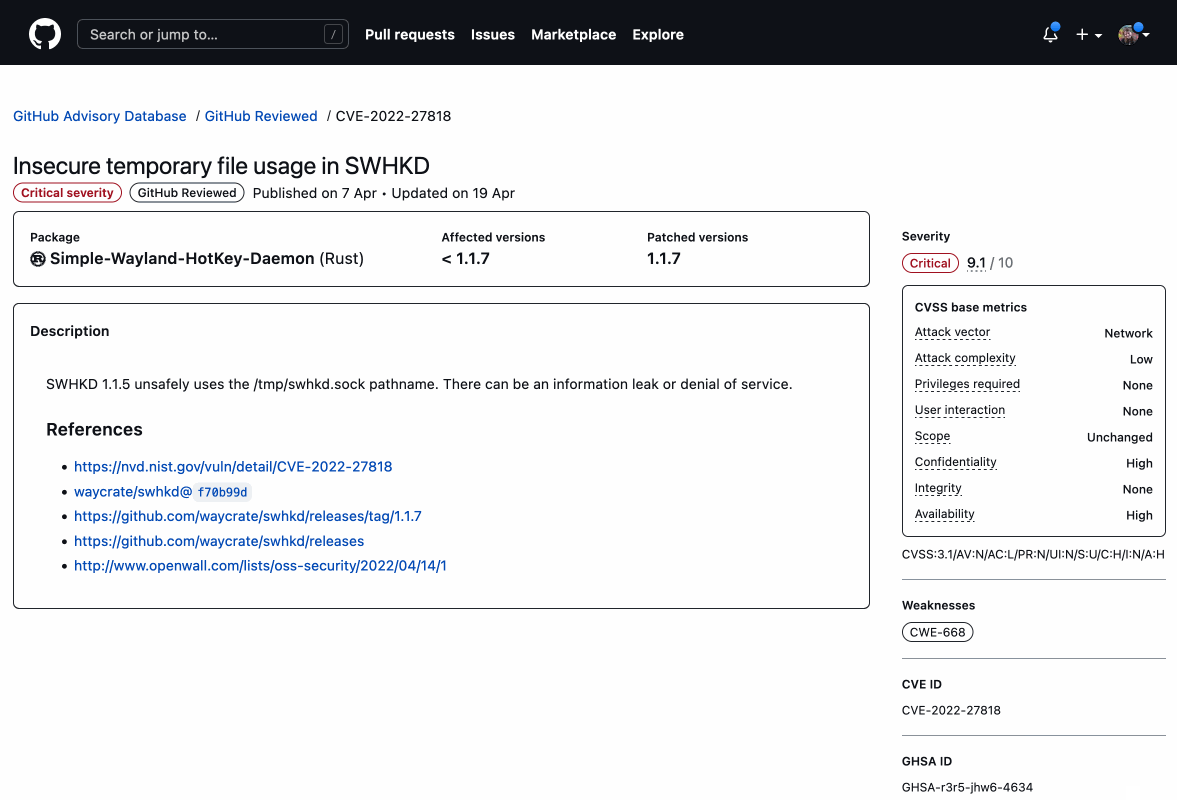
Dependabot alerts and security updates
Dependabot alerts notify you when new vulnerabilities are discovered in Rust packages you’re already using, and Dependabot security updates will create pull requests that automatically upgrade your vulnerable Rust packages to a version without the vulnerability. You can configure both Dependabot alerts and Dependabot security updates so you’re just getting the notifications and pull requests you want for your repository.
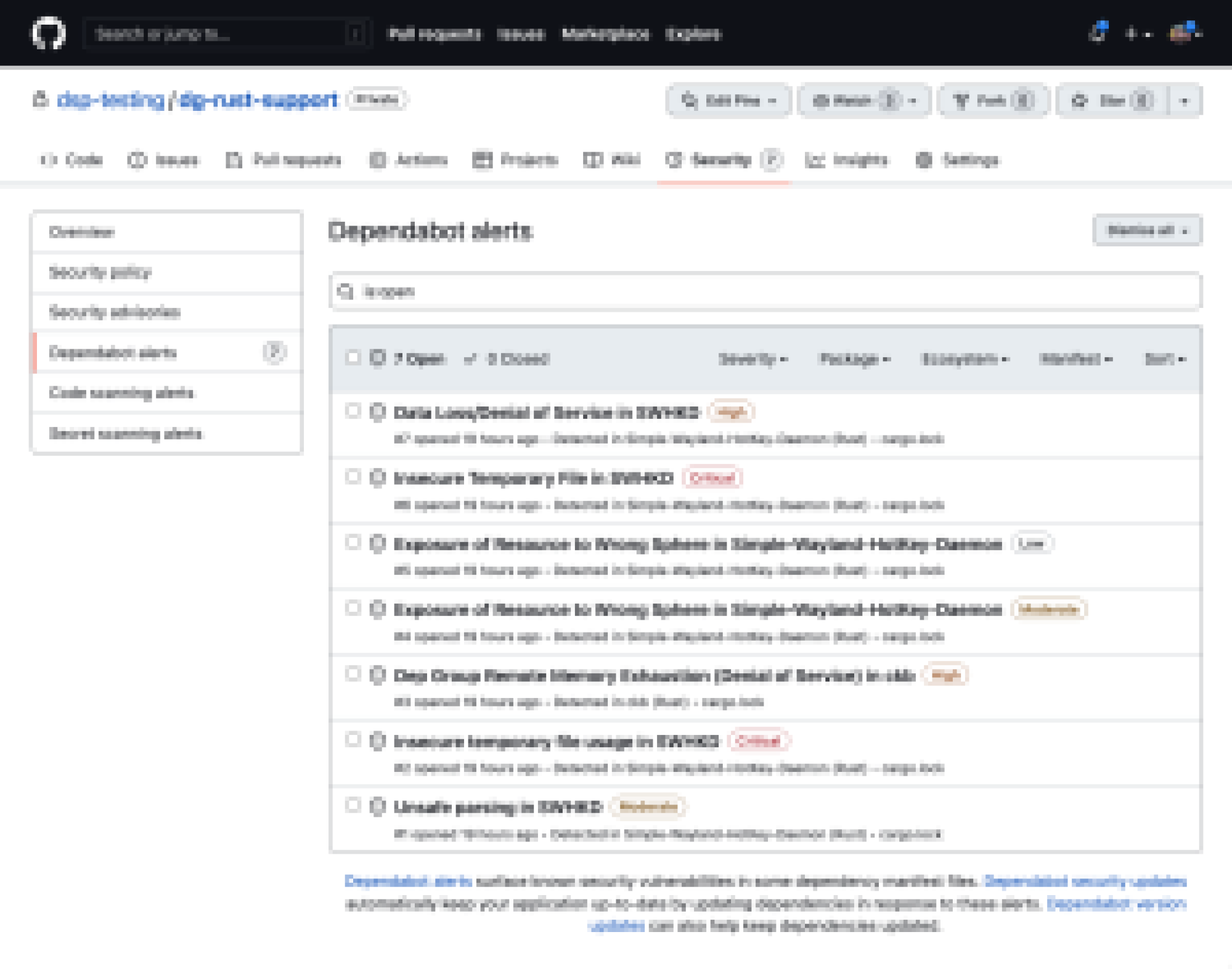
Secure your Rust repository
There’s a lot of different functionality here! You can get started by securing your Rust repository, or learn more about each of GitHub’s supply chain security features:
- Security advisories
- Dependency graph
- Dependency review
- Dependabot alerts
- Dependabot security updates
Tags:
Written by
Related posts

AI-supported vulnerability triage with the GitHub Security Lab Taskflow Agent
Learn how we are using the newly released GitHub Security Lab Taskflow Agent to triage categories of vulnerabilities in GitHub Actions and JavaScript projects.

Community-powered security with AI: an open source framework for security research
Announcing GitHub Security Lab Taskflow Agent, an open source and collaborative framework for security research with AI.

Bugs that survive the heat of continuous fuzzing
Learn why some long-enrolled OSS-Fuzz projects still contain vulnerabilities and how you can find them.