
Agents panel: Launch Copilot coding agent tasks anywhere on GitHub
Delegate coding tasks to Copilot and track progress wherever you are on GitHub. Copilot works in the background, creates a pull request, and tags you for review when finished.

Delegate coding tasks to Copilot and track progress wherever you are on GitHub. Copilot works in the background, creates a pull request, and tags you for review when finished.

In May, we launched Copilot coding agent, our autonomous developer agent. You can delegate tasks to Copilot, and Copilot will work in the background and create a draft pull request…

You can now participate in a public preview to migrate repositories to GitHub Enterprise Cloud (GHEC) with GitHub Enterprise Importer (GEI) using GitHub-owned blob storage. You no longer need to…

The open source Git project just released Git 2.51. Here is GitHub’s look at some of the most interesting features and changes introduced since last time.

GitHub Actions is powered by a diverse ecosystem of first-party and community contributed actions. If one of these actions has a vulnerability or is compromised by a malicious actor, it…
How GitHub’s new MCP server and GPT-5 are revolutionizing developer workflows — with live build examples.

Discover the latest trends and insights on public software development activity on GitHub with the quarterly release of data for the Innovation Graph, updated through March 2025.
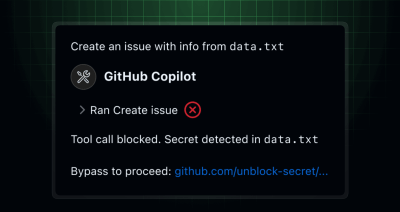
The remote GitHub MCP server now scans all of its tool call inputs in public repositories. If an exposed secret is detected, the call is blocked by default with clear…
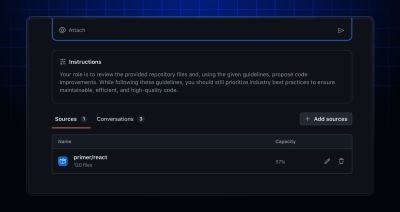
What’s New You can now add entire repositories to your spaces. Get up and running faster when you’re exploring unfamiliar codebases or need comprehensive context across your project. Key benefits…

Learn how the International Telecommunication Union made the switch to open source, and how you can too!

Secret scanning is adding validity check support for 12 additional token types across 11 providers. In addition to previously announced token types, you will now see validity checks for the…

Dependabot now supports automatic dependency updates for vcpkg, the free C/C++ package manager from Microsoft. This enables teams using vcpkg to keep their C and C++ dependencies secure and up-to-date…

Learn how maintainers are using the GitHub MCP Server and what they are building in this episode of the GitHub Podcast.

Following our previous announcement, the Dependabot reviewers configuration option has been removed. We’ve retired this configuration option because the functionality overlaps with GitHub code owners. You can use code owners…

Discover practical ways GitHub Copilot streamlines code reviews, pull requests, and daily engineering tasks with real prompts, examples, and workflow tips from our engineering team.

Starting today, Linux and Windows arm64 standard hosted runners in public repositories are generally available. Developers can take advantage of the performance benefits of using arm64 processors or run their…

Earlier, we announced copilot-instructions.md customization for Copilot code review was in public preview. Now it is generally available! All you need to do is add a copilot-instructions.md file in your…
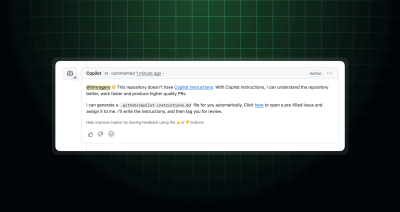
With GitHub Copilot coding agent, you can delegate tasks to Copilot that it will work on in the background. By adding custom instructions to your repository, you can guide Copilot…

This week we’ve focused on making Spark more reliable and responsive when building your apps. Enhanced reliability We’ve resolved several issues that were interrupting your workflow: Fixed errors that prevented…
You can delegate tasks to GitHub Copilot coding agent that it will work on in the background. Copilot opens a pull request, pushes its changes, and then requests a review.…

Learn how to integrate AI features with GitHub Models directly in GitHub Actions workflows.
Build what’s next on GitHub, the place for anyone from anywhere to build anything.
Last chance: Save $700 on your IRL pass to Universe and join us on Oct. 28-29 in San Francisco.