Reducing security risk in open source software with GitHub Actions and OpenSSF Scorecards V4
We’re excited to announce the V4 release of the OpenSSF’s Scorecard project in partnership with Google.

GitHub is committed to helping secure the future of open source security, and it is why we continue to partner with our industry peers through the Open Source Security Foundation (OpenSSF). Today we’re excited to announce the V4 release of the OpenSSF’s Scorecard project in partnership with Google.
Scorecards is an automated security tool that flags risky supply chain practices in open source projects. We have added a GitHub Action and starter workflow into the GitHub user interface and Marketplace to help developers follow best security practices. Once configured, the Scorecards Action runs automatically on repository changes, and alerts developers about risky supply chain practices using the built-in code scanning experience. The Scorecards project makes a number of checks, including whether the project has a static analysis tool, like CodeQL, configured.
The results are automatically sent to the GitHub code scanning alerts API and appear under the security tab for the project. This will help open source software projects to understand whether they are implementing the Scorecards project’s best practices, and help assure their users about the precautions they’re taking on security.
To give it a try, head over to GitHub and create a personal access token, if you don’t already have one. Then, navigate to your project, click on the Security tab, and Set up code scanning.
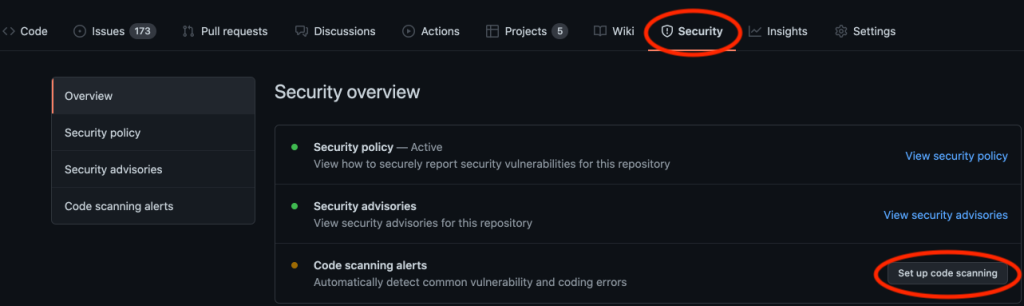
Then select the OSSF Scorecards option, and click Set up this workflow.
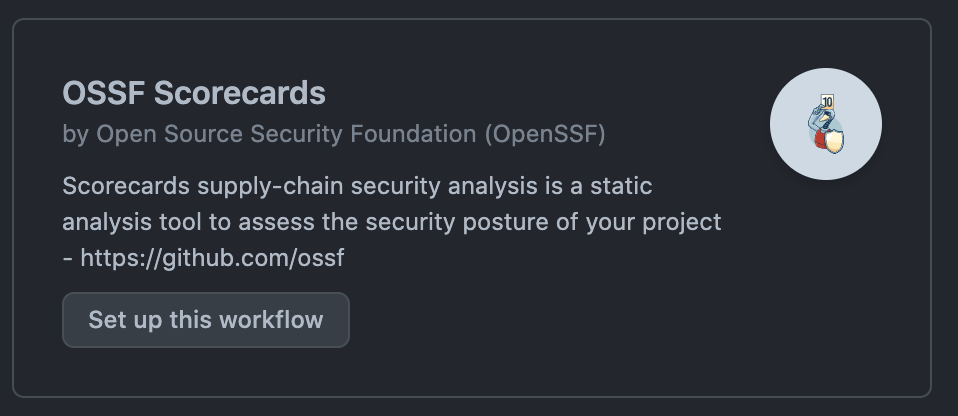
The workflow is preconfigured to run on every contribution and will upload results to the code scanning API for remediation. You will need to copy your PAT into the workflow. Check the comments for the appropriate location.
Note: If you already have code scanning configured on your project, you may see a different UI experience within the code scanning alerts page. Simply click Add more scanning tools as shown below.
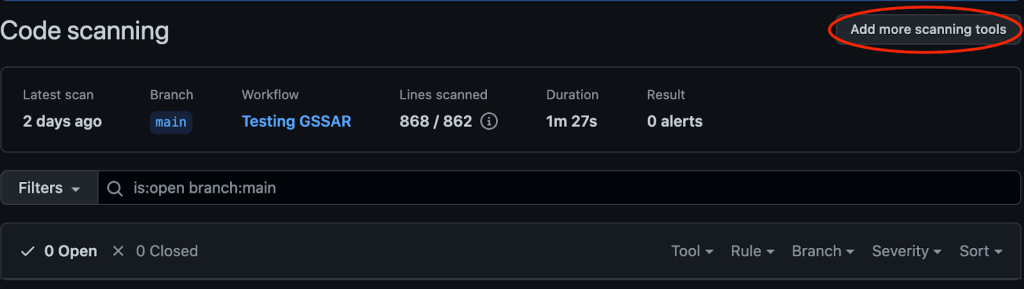
And just like that, results will start flowing into your Security tab for review.
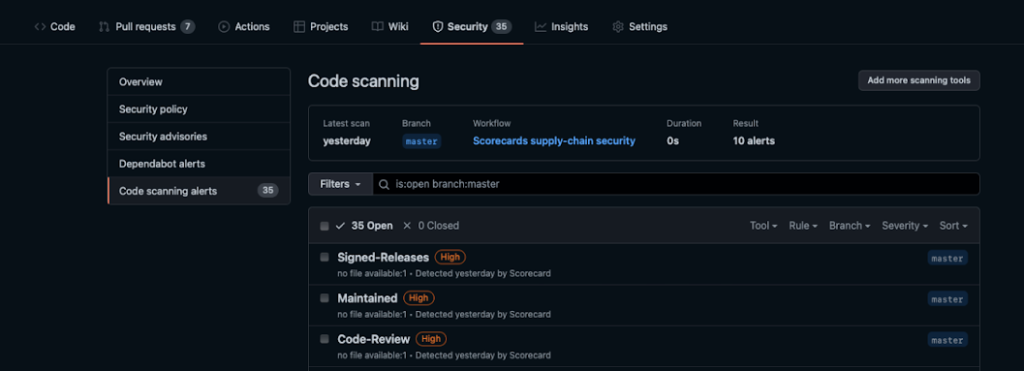
While you’re setting up Scorecards, you can also configure CodeQL or one of our other integrated third-party static analysis tools, which is a great first step toward securing your project.
CodeQL, the code scanning API, and 1,000 Actions minutes are included for free to public repositories on GitHub.com.
These features are also available to enterprises through GitHub Enterprise and GitHub Advanced Security. To learn more about GitHub’s Platform and Application Security, please see https://github.com/features/security.
Tags:
Written by
Related posts

What to expect for open source in 2026
Let’s dig into the 2025’s open source data on GitHub to see what we can learn about the future.

Securing the AI software supply chain: Security results across 67 open source projects
Learn how The GitHub Secure Open Source Fund helped 67 critical AI‑stack projects accelerate fixes, strengthen ecosystems, and advance open source resilience.

Welcome to the Eternal September of open source. Here’s what we plan to do for maintainers.
Open source is hitting an “Eternal September.” As contribution friction drops, maintainers are adapting with new trust signals, triage approaches, and community-led solutions.