Secret scanning alerts are now available (and free) for all public repositories
Secret scanning alerts are now generally available for all public repositories. Admins can now turn on the alert experience with one click.

In December, we announced the public beta for free secret scanning alerts across public repositories. Since its release, 70 thousand public repositories have turned on secret scanning alerts, helping users like you to triage thousands of leaked secrets.
As of today, GitHub secret scanning’s alert experience is generally available and free for all public repositories. You can enable secret scanning alerts across all the repositories you own to notify you of leaked secrets across your full repository history including code, issues, description, and comments.
GitHub secret scanning works with 100+ service providers in the GitHub Partner Program. In addition to alerting users, we will continue to notify our partners when one of their secrets is leaked. But with secret scanning alerts enabled, you’ll now also receive alerts for secrets where it’s not possible to notify a partner–for example, if self-hosted keys are exposed–along with a full audit log of actions taken on the alert.
This empowers you with full visibility into your risk at scale. One example of this in practice is @rajbos, DevOps Consultant and Trainer, who enabled secret scanning on approximately 14 thousand repositories and discovered over one thousand secrets. Rob remarked, “My research proves the point to why everyone should have secret scanning enabled. I have researched 14 thousand public GitHub Action repositories and found over one thousand secrets in them!”
“Even though I train a lot of folks on using GitHub Advanced Security, I found secrets in my own repositories through this.”
Despite multiple years of experience, it also happens to myself. That’s how easy it is to include secrets by mistake.
“With secret scanning enabled, you’ll get notified of secrets and the partner can already revoke them automatically, making the code world a little more safe.” Read more about Rob’s experience in his blog post.
Get started in one click
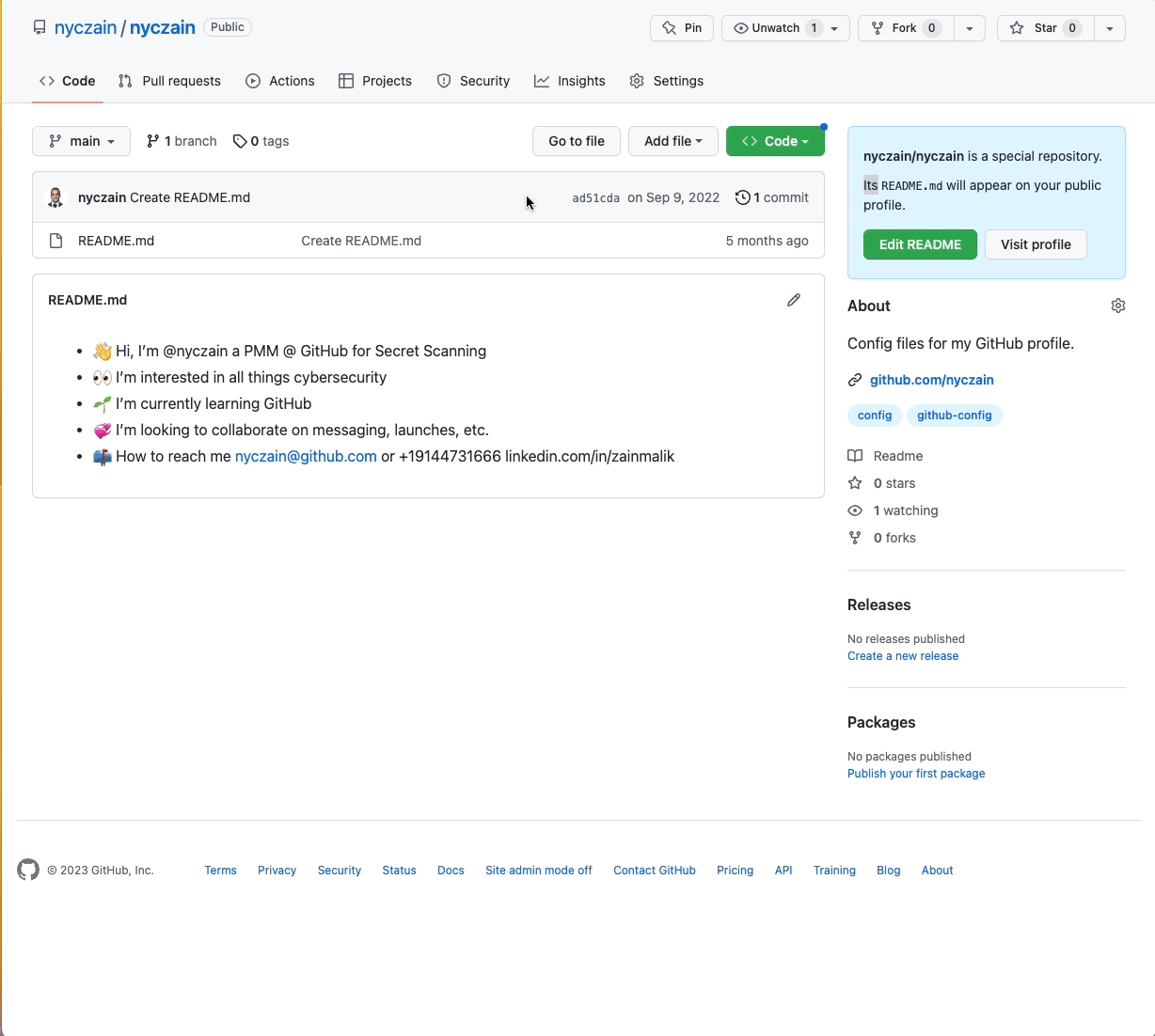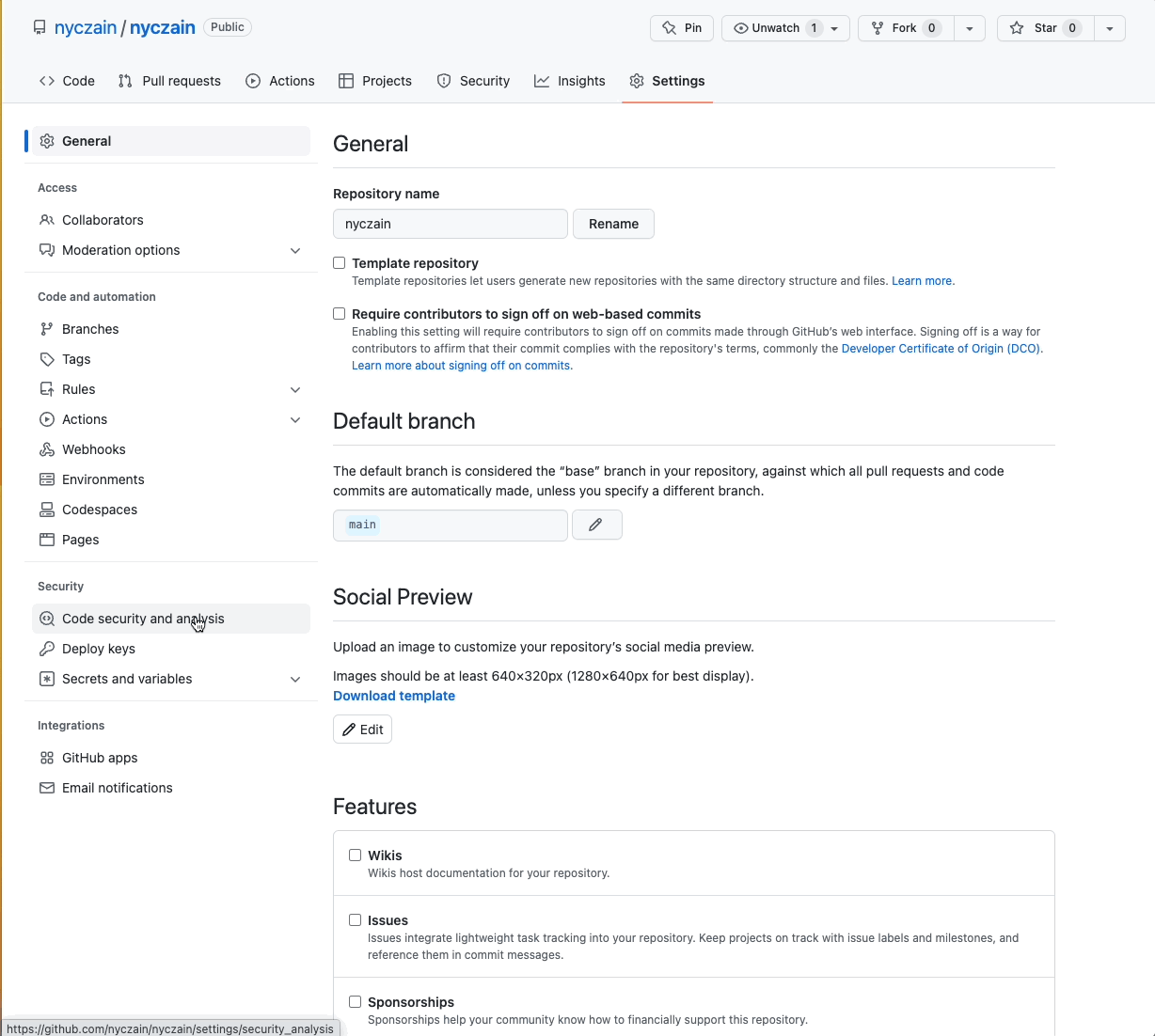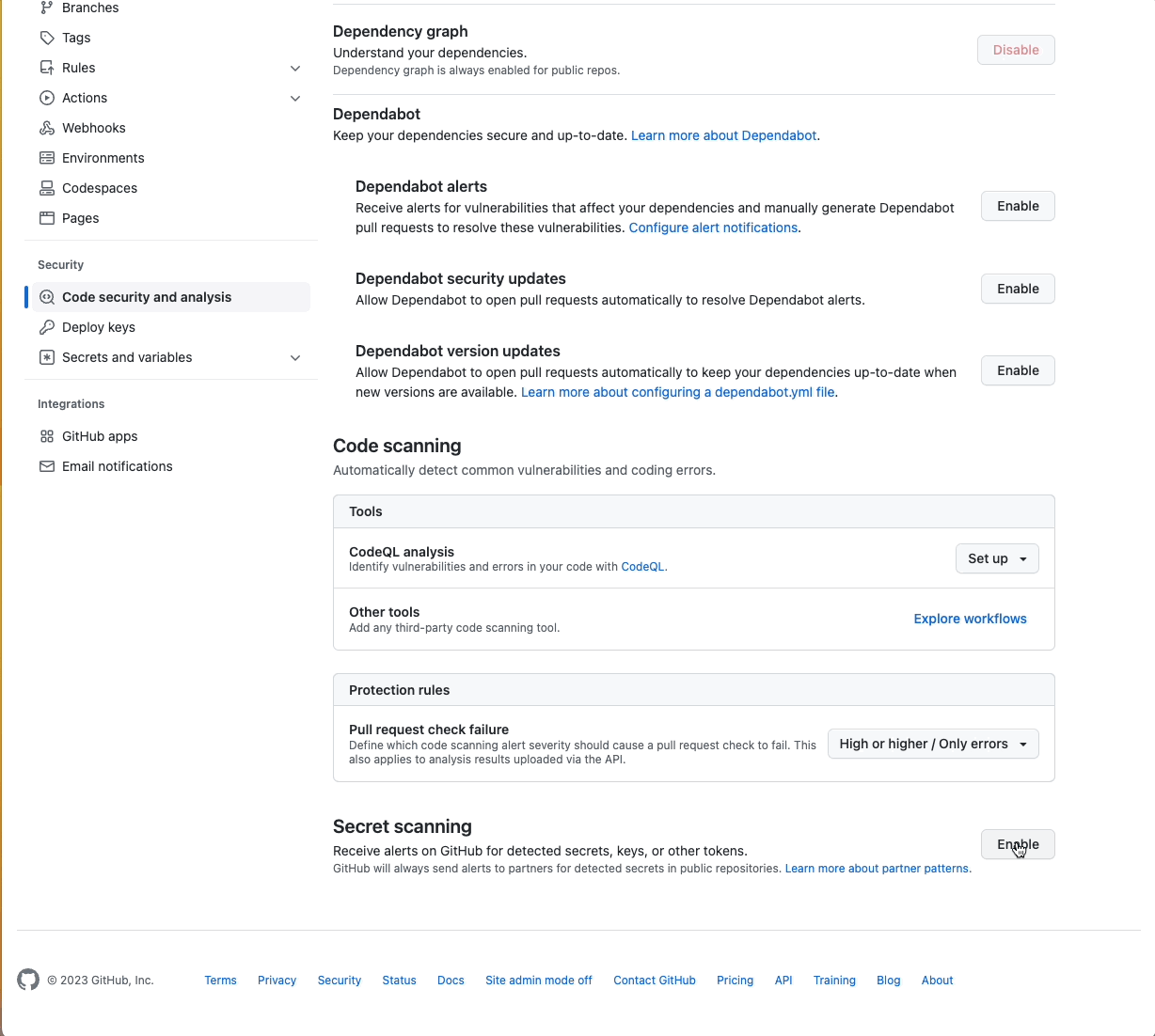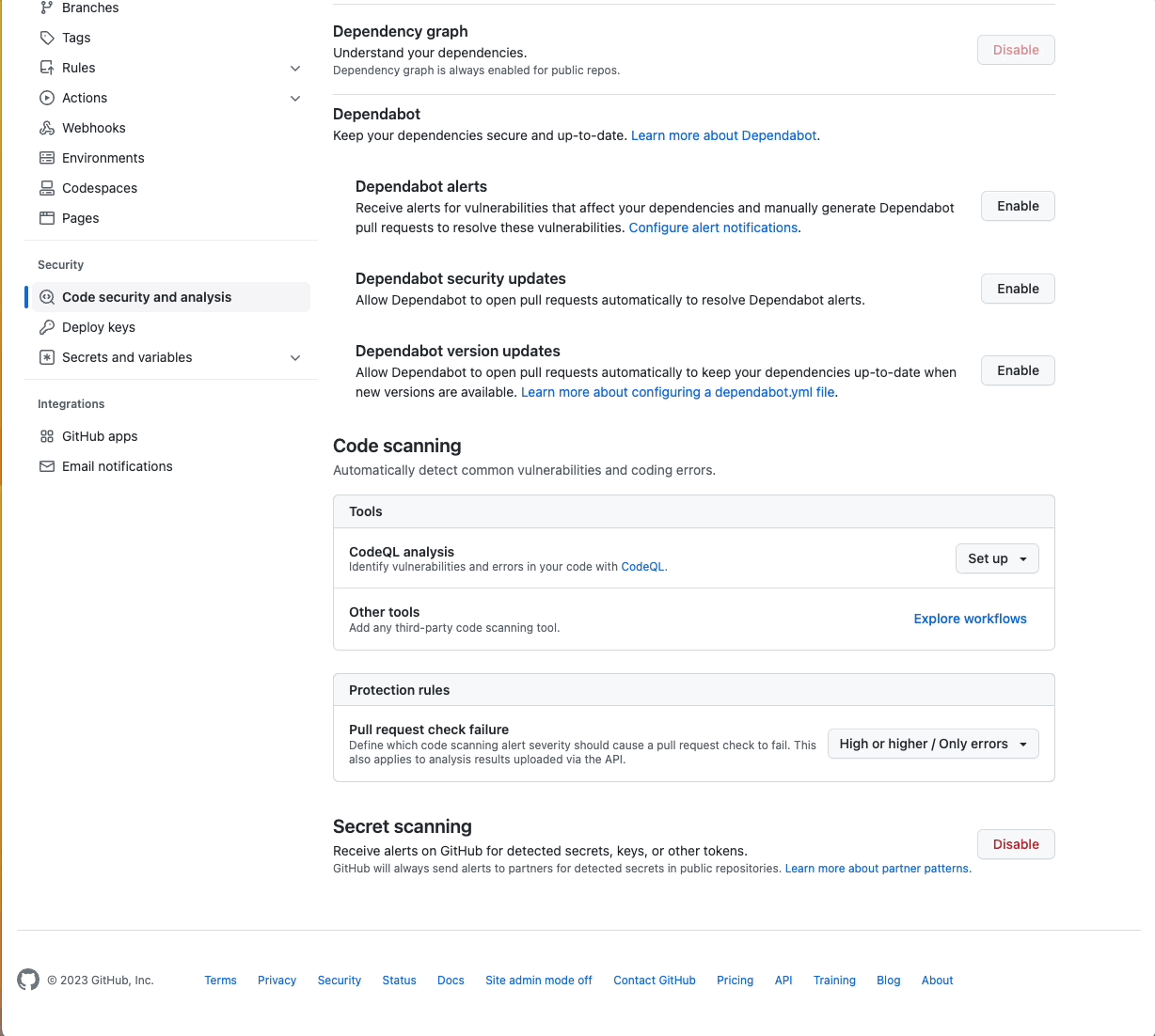
Any owner or admin of a public repository can enable secret scanning alerts. Enterprise administrators and organization owners can also bulk enable alerts for multiple repositories. You can do this by going to the ‘Settings’ tab and clicking on ‘Code security and analysis’ under ‘Security’. Find ‘Secret scanning’ and click ‘Enable’.
You can find more information on how to enable secret scanning alerts for your repository in our documentation.
Become a GitHub secret scanning partner
If you’re a service provider and interested in protecting our shared users from leaking secrets, we encourage you to join the secret scanning partner program. We currently support 200+ patterns and 100+ partners. To get started, please email secret-scanning@github.com.
Tags:
Written by
Related posts

From pair to peer programmer: Our vision for agentic workflows in GitHub Copilot
AI agents in GitHub Copilot don’t just assist developers but actively solve problems through multi-step reasoning and execution. Here’s what that means.

GitHub Availability Report: May 2025
In May, we experienced three incidents that resulted in degraded performance across GitHub services.

GitHub Universe 2025: Here’s what’s in store at this year’s developer wonderland
Sharpen your skills, test out new tools, and connect with people who build like you.