Raising the bar for software security: next steps for GitHub.com 2FA
GitHub will require all users who contribute code on GitHub.com to enable one or more forms of two-factor authentication (2FA) by the end of 2023. Learn more about our approach, when we’ll begin our rollout, and what you can expect as we begin requiring 2FA.

GitHub is committed to raising the bar for the security of the software development ecosystem, and that starts with the developer. We continue to improve the npm 2FA experience, and now require maintainers of packages with more than 1 million weekly downloads or more than 500 dependents to enable 2FA. To better protect developers from account theft, we announced our intention to require all developers who contribute code on GitHub.com to enable one or more forms of 2FA by the end of 2023. Read on to learn more about how GitHub is approaching this challenge, and what you can expect as we begin requiring 2FA in March 2023.
The challenge and how we’re approaching it
Millions of developers on GitHub.com will be required to enable 2FA during 2023. We want to meet this challenge while also providing a positive experience for developers. To do so, we’ll gradually roll out the 2FA requirement to users over the course of 2023.
Beginning in March 2023, we’ll start requiring distinct groups of users to enable 2FA over time. This will allow us to learn about the efficacy of the rollout and make adjustments as needed before we scale to larger groups as 2023 progresses.
While GitHub won’t be providing specifics regarding how users qualify for these groups or which group a specific user will fall into, these groups are built from the following criteria with an emphasis on impact to security of the broader ecosystem:
- Users who published GitHub or OAuth apps or packages
- Users who created a release
- Users who are Enterprise and Organization administrators
- Users who contributed code to repositories deemed critical by npm, OpenSSF, PyPI, or RubyGems
- Users who contributed code to the approximate top four million public and private repositories
At GitHub, we ship to learn and ship and iterate to help us optimize for successful user experiences. Accordingly, we’ll assess the outcomes of the rollout after each group–observing user success rates for 2FA onboarding, rates of account lockout and recovery, and our support ticket volume. This data will enable us to adjust our approach and more appropriately size and schedule remaining groups as needed to ensure a positive experience for developers, and support workloads GitHub can sustain.
What to expect if you are required to enable 2FA
GitHub has designed a rollout process intended to both minimize unexpected interruptions and productivity loss for users and prevent account lockouts.
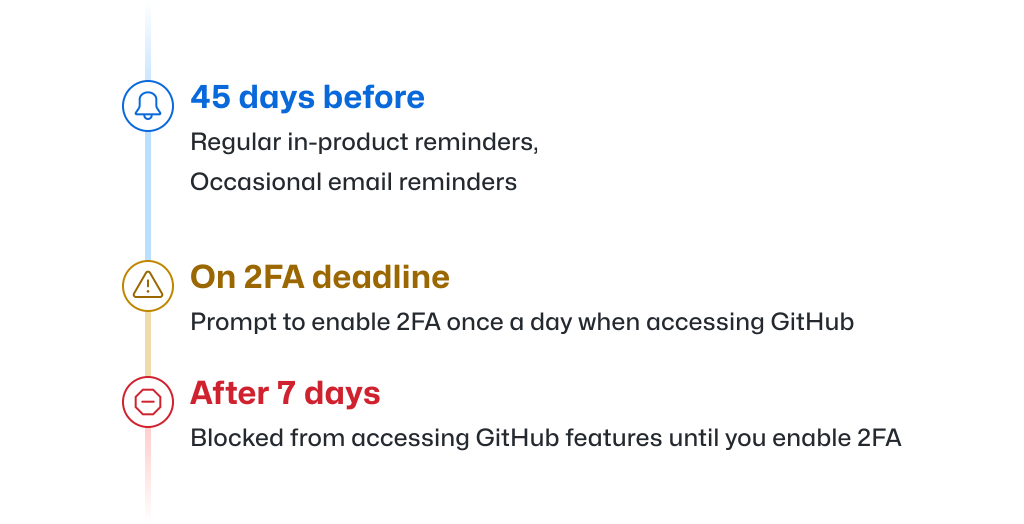
1. If you are selected for a pending 2FA enablement group,
you will receive advance notification by email informing you of your deadline to enable 2FA and providing guidance on how to do so. This notification will occur approximately 45 days before the deadline.
More details
- When your group timeline begins, you will also begin receiving regular reminders of the pending deadline via announcement banners at the top of GitHub.com, which will guide you to the 2FA onboarding process.
- During your 45 day notification period, you’ll receive occasional emails notifying you of your pending 2FA enablement deadline.
2. Once the enablement deadline passes,
you will be prompted to enable 2FA the first time you access GitHub.com each day. You may snooze this prompt once a day for up to one week to provide you with flexibility, but after that week you will be unable to access GitHub.com features until you enable 2FA.
More details
- This one week snooze period only starts when you sign in after the deadline, so if you’re on vacation, don’t worry – you won’t come back locked out of GitHub.com.
3. Twenty-eight (28) days after you enable 2FA,
you will be presented with a 2FA check-up while using GitHub.com, which validates that your 2FA setup is working correctly. Previously signed in users will be able to reconfigure 2FA if they have misconfigured or misplaced second factors or recovery codes during onboarding.
Any user that later qualifies for enablement will be enrolled in the process outlined above.
Looking Forward
During the last six months, GitHub has been hard at work researching, planning, and implementing improvements to our 2FA onboarding and account lockout recovery processes. You can expect additional improvements and optimizations to the account lockout recovery experience in the first half of 2023. Finally, we’re hard at work to bring passkey support to GitHub.com to make strong authentication even easier to use. If you’d like to get a head start and enable 2FA today, more information is available in our initial announcement.
Tags:
Written by
Related posts

GitHub availability report: January 2026
In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Pick your agent: Use Claude and Codex on Agent HQ
Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What the fastest-growing tools reveal about how software is being built
What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.