Visit our documentation to learn more about push protection, GitHub Advanced Security, or the secret scanning partner program.
Push protection is generally available, and free for all public repositories
Announcing the general availability of push protection–a feature that proactively prevents secret leaks in your public and private repositories.
At GitHub, we believe that by empowering developers with intuitive security built into their workflows, we can, together, shift security from reactive to proactive. Since the beta release of secret scanning’s push protection feature for GitHub Advanced Security users in April 2022, developers using push protection have prevented 17,000 potential secret leaks–saving over 95,000 hours revoking, rotating, and remediating exposed secrets.
Today, push protection is generally available for private repositories with a GitHub Advanced Security (GHAS) license. In addition, to help developers and maintainers across open source proactively secure their code, GitHub is making push protection free for all public repositories.
Push protection prevents secret leaks without compromising the developer experience by scanning for highly identifiable secrets before they are pushed. We partner closely with service providers to ensure tokens have a low false positive rate, ensuring developer trust in our alerts. When a secret is detected in code, developers are prompted directly in their IDE or command line interface with remediation guidance to ensure that the secret is never exposed. As Ger McMahon, Product Area Leader ALM Tools and Platforms at Fidelity Investments, explains:
“Incorporating secret scanning with push protection directly into the development workflow reduces friction which enables developers to create secure and high-quality code.”
How push protection creates a frictionless developer experience
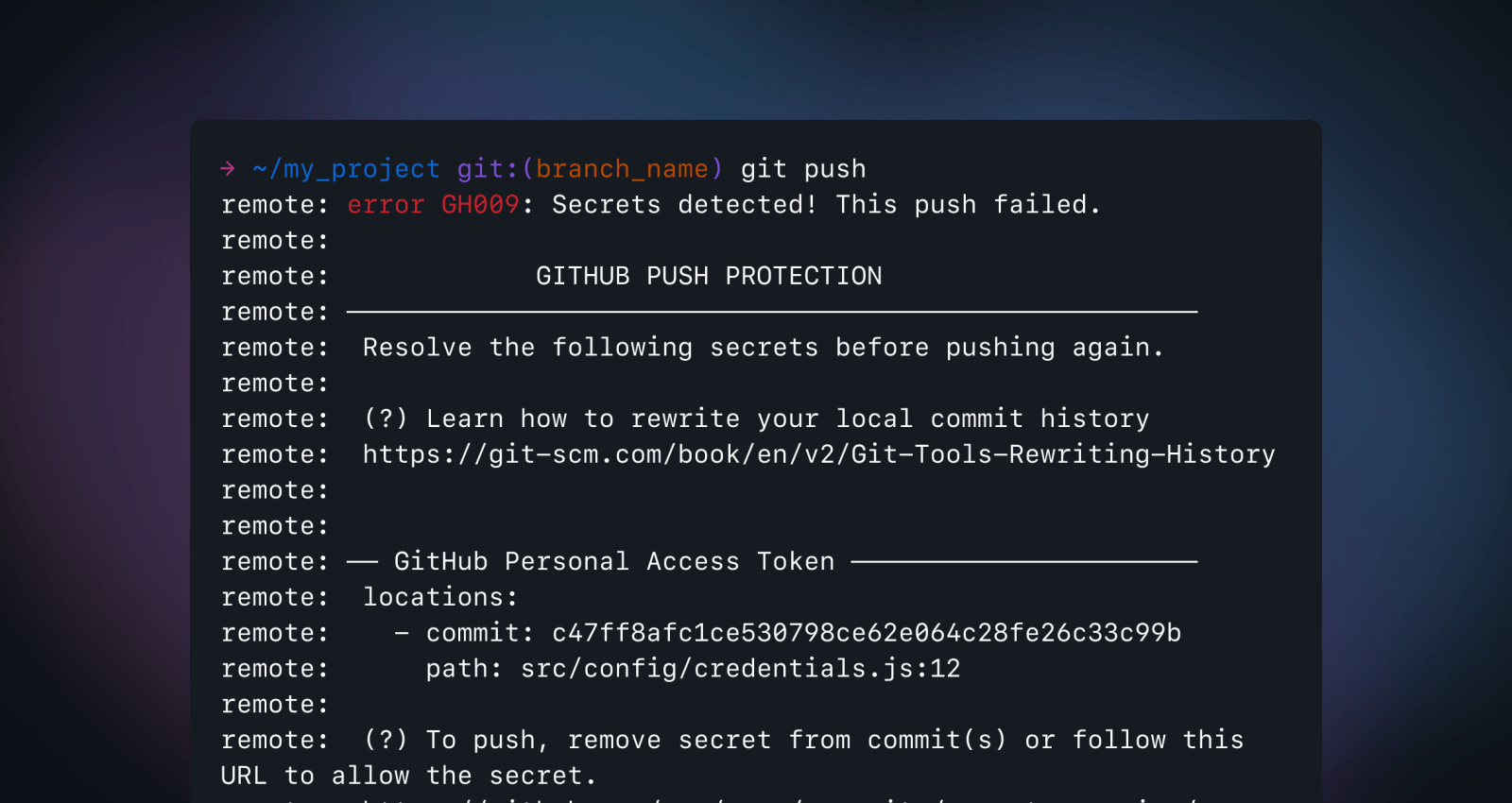
Developers need tools they can trust—GitHub designed push protection with this in mind. If you are pushing a commit containing a secret, a push protection prompt will appear with information on the secret type, location, and how to remediate the exposure. Once you have removed the secret from your commit history, you can re-push your commit. Push protection only blocks secrets with low false positive rates, so when a commit is blocked, you know it’s worth investigating.
In certain instances, you may need to push code that has a secret in it–for example, fixing an outage with speed and addressing the secrets after. You can bypass push protection by providing a reason, for example, it’s used for testing, is a false positive, or is an acceptable risk that will be fixed later. Repository and organization administrators and security managers will receive an email alert on all bypasses and can audit any bypasses via their enterprise and organization audit logs, alert view UI, REST API, or webhook events.
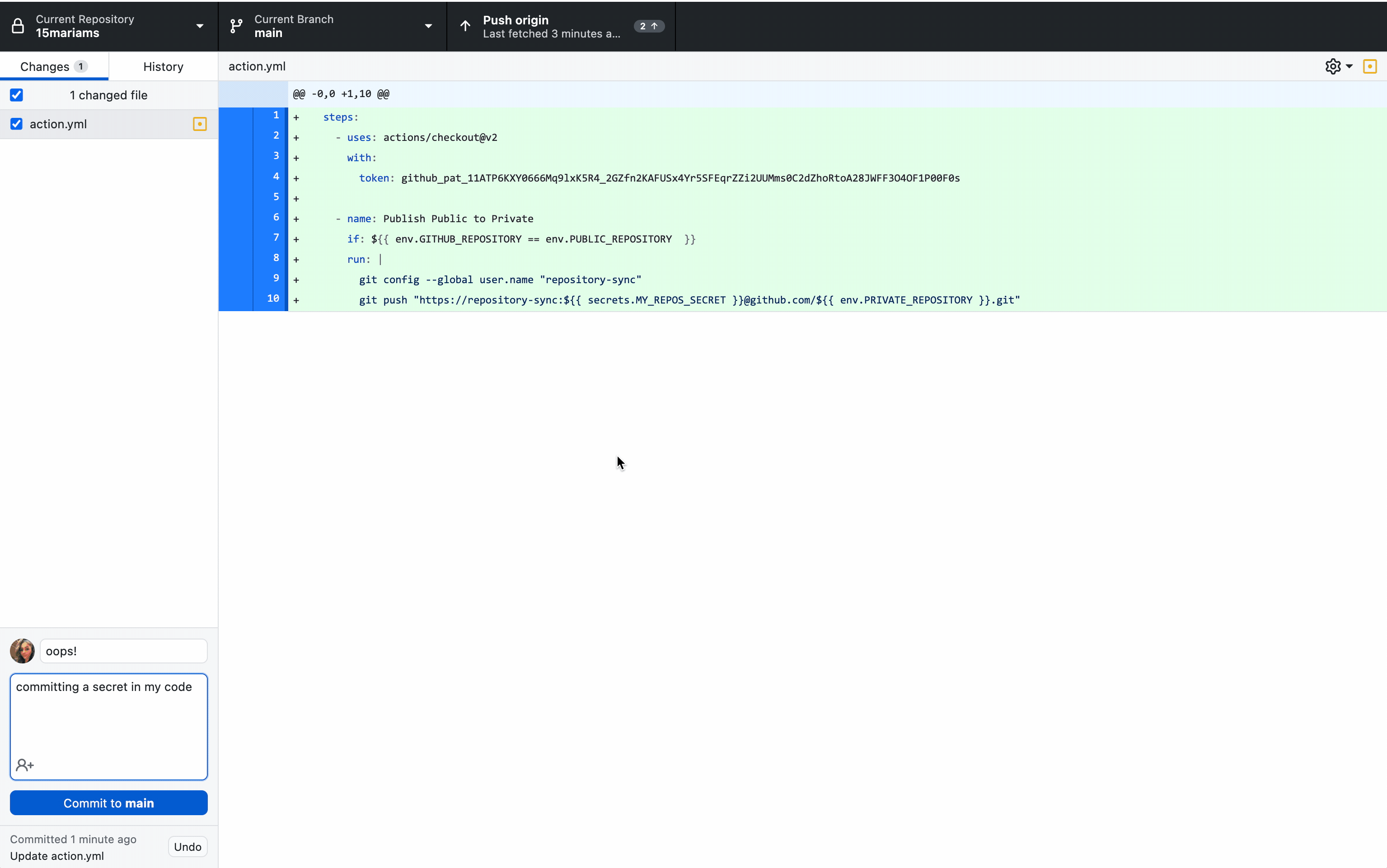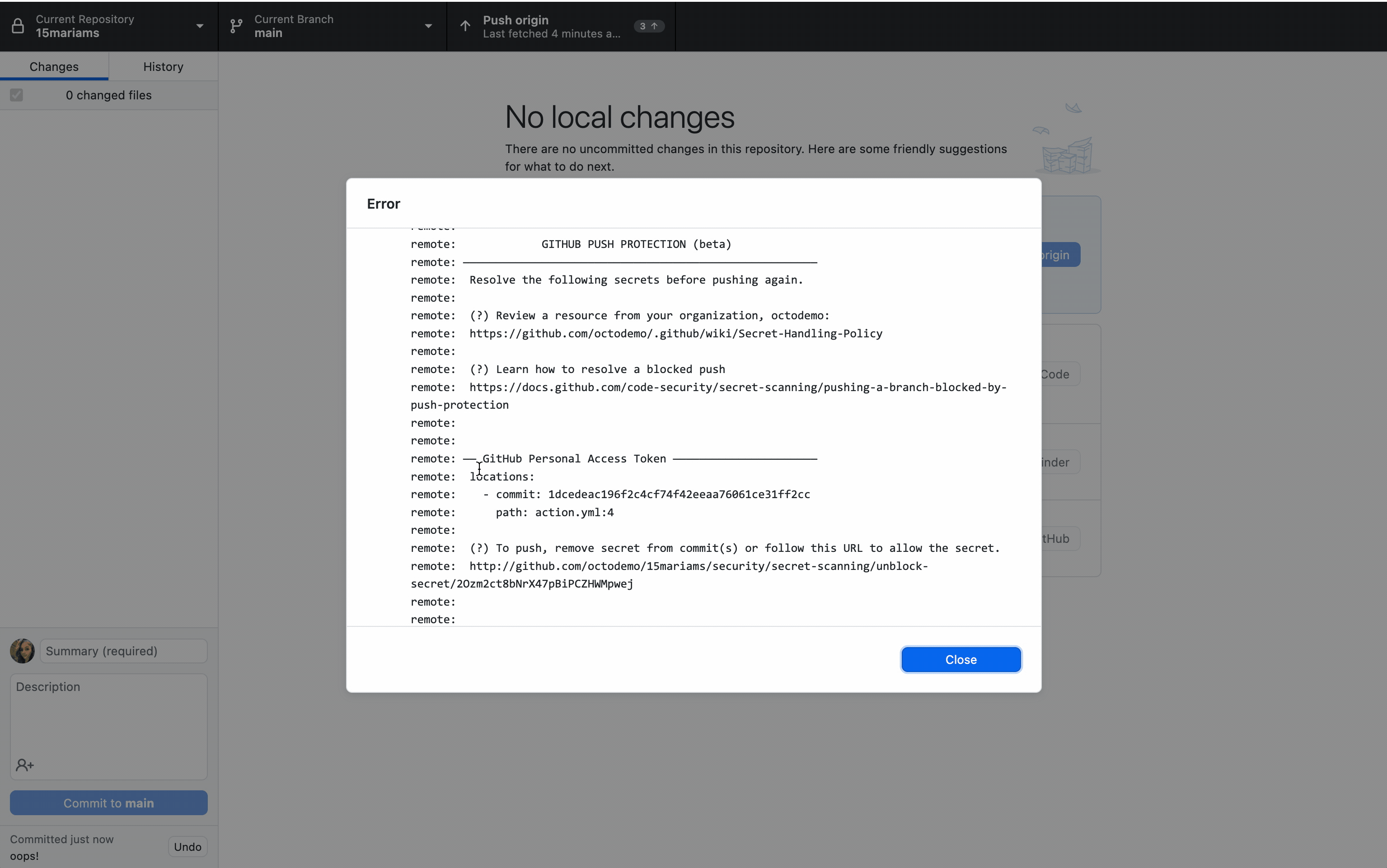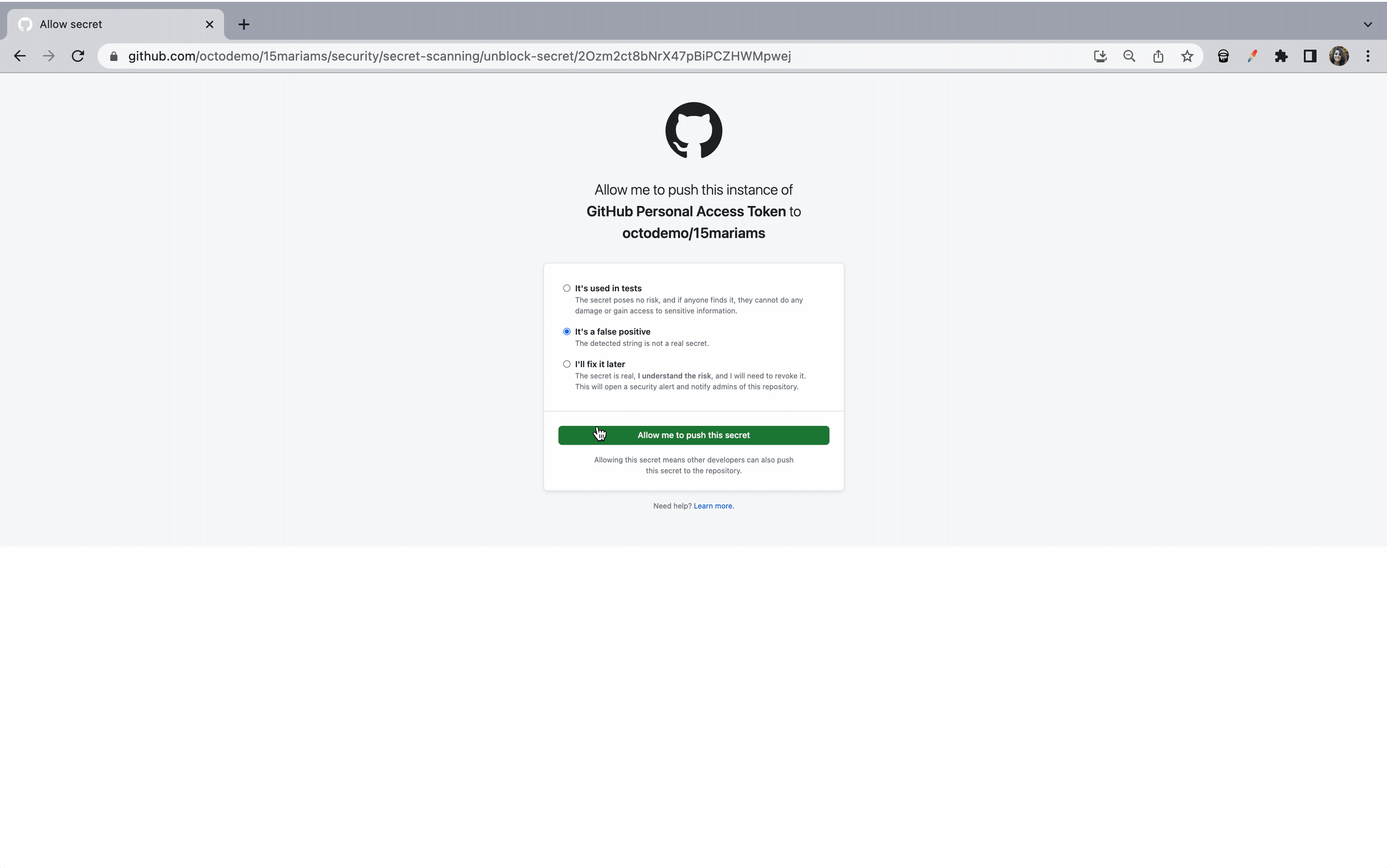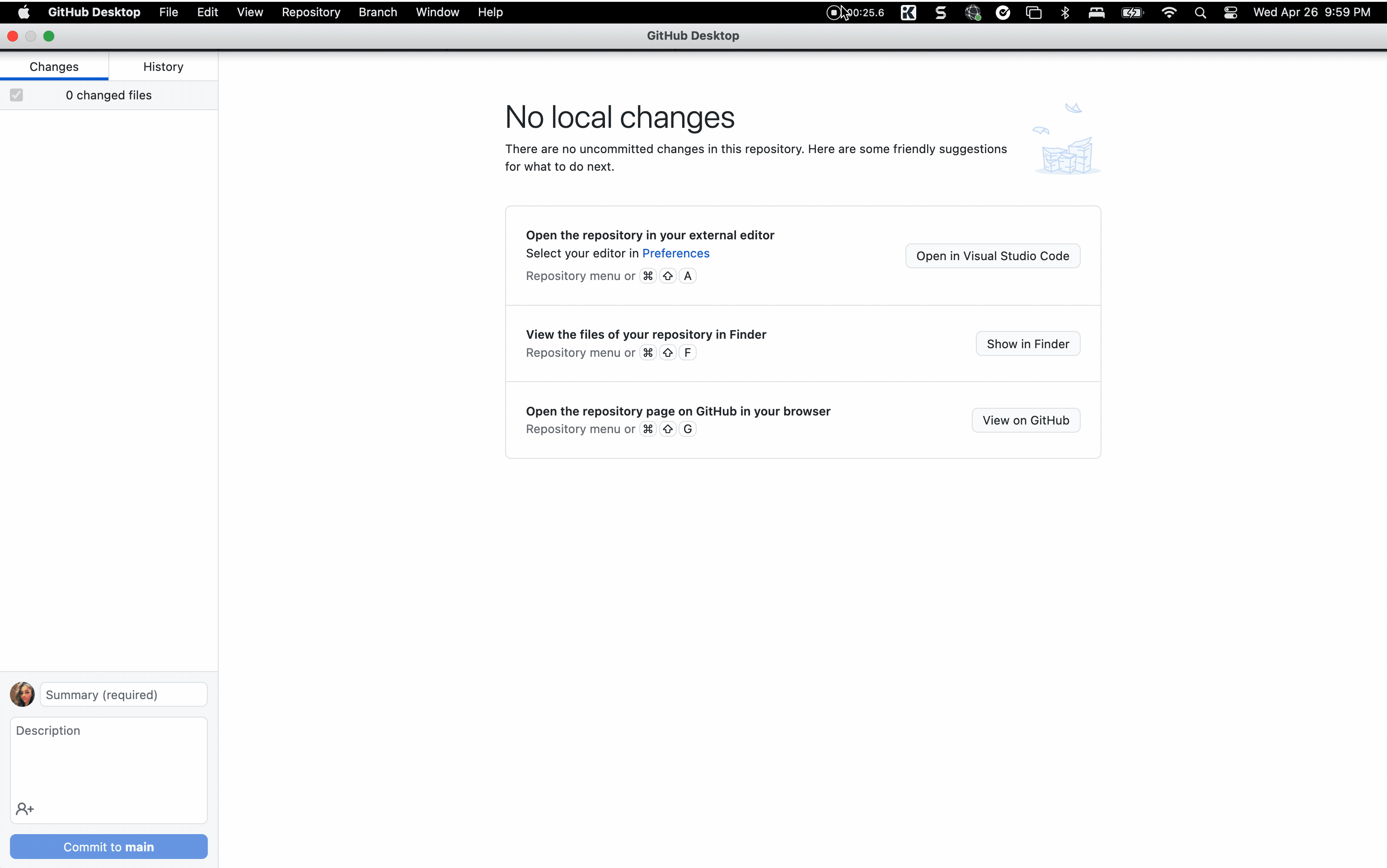
According to Leo Stolyarov, Director and Cloud Practice Lead at KPMG, this approach ensures an improved security posture without compromising on velocity.
“Secret scanning push protection is a frictionless feature that has brought better security awareness and protection from leaked secrets without compromising developer experience.”
Learn more or get started with push protection
To enable push protection in a repository, organization, or enterprise, go to your “Code security and analysis” settings and scroll down to the secret scanning section. You can enable both “Secret scanning” and its subset, “Push protection” by selecting the enable all button.
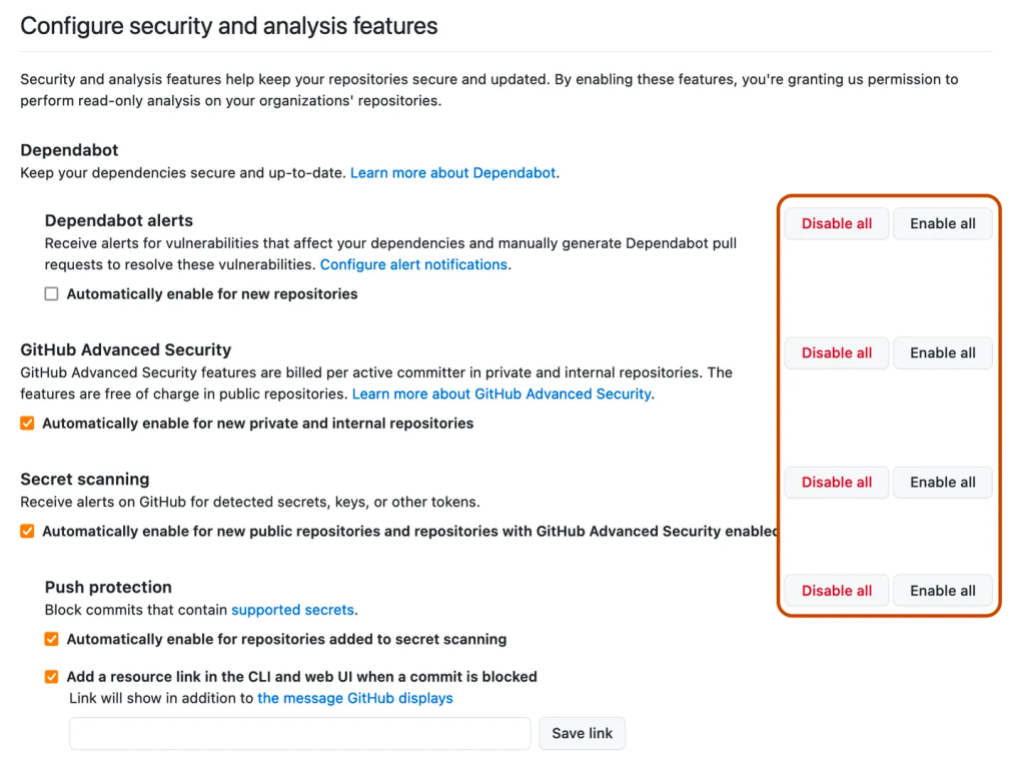
You can automatically enable push protection or provide a custom resource link that will appear in a push protection message via the checkboxes under the “Push Protection” section. This will ensure push protection is applied to any new repository created in your enterprise or organization.
GitHub Advanced Security customers can also customize their deployment further by enabling push protection on their custom secret patterns.
Tags:
Written by
Related posts

GitHub availability report: January 2026
In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Pick your agent: Use Claude and Codex on Agent HQ
Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What the fastest-growing tools reveal about how software is being built
What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.