New improvements and best practices for account security and recoverability
Finding compromised passwords and two-factor recovery checkups

Strong authentication credentials are critical to preventing malicious access to your account. Everyone on GitHub has a password, so a strong password is an excellent starting point. And, for even stronger assurances, we highly encourage users to enable two-factor authentication (2FA). We’re introducing two new features to help you balance the security, usability, and recoverability of your accounts.
Enforcing stronger passwords
Common password advice is to use a long and unique password for each website you have an account with. It’s challenging to remember a strong and unique password for each website without either using a password manager or using a trivially discovered theme. As a result, password reuse is extremely prevalent. Regardless of the strength of a password, a single breach can nullify its security when used elsewhere.
Several years ago, security researcher Troy Hunt sought to tackle the compromised passwords problem with his HaveIBeenPwned.com project. While Troy hosts a service that people and services can use to check for compromised passwords, he also generously made the approximately 517 million record dataset available for download. Using this data, GitHub created an internal version of this service so that we can validate whether a user’s password has been found in any publicly available sets of breach data.
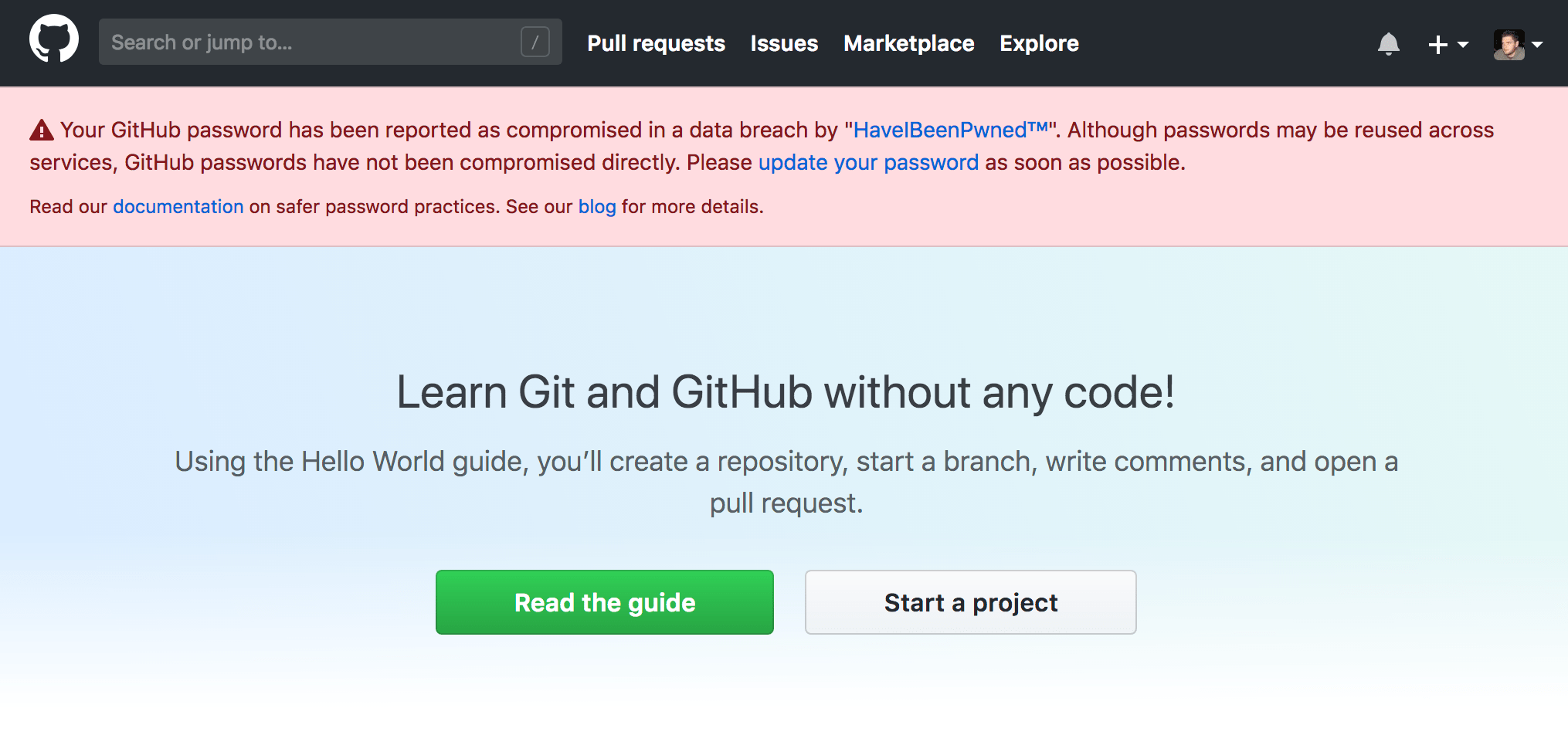
Starting today, people using compromised passwords will be prompted to select a different password during login, registration, or when updating their password. Don’t worry, your password is protected by the password hashing function bcrypt in our database. We only verify whether your password has been compromised when you provide it to us.
Two-factor authentication checkup
Using two-factor authentication is a best practice and can help protect you even when low quality or compromised passwords are used. However, two-factor authentication can be a double-edged sword. Two-factor authentication ensures that access to a single factor, such as your password or email address where a password reset can be sent, is not sufficient to access an account. But, if you lose access to your two-factor credentials, it can lead to losing access to your account.
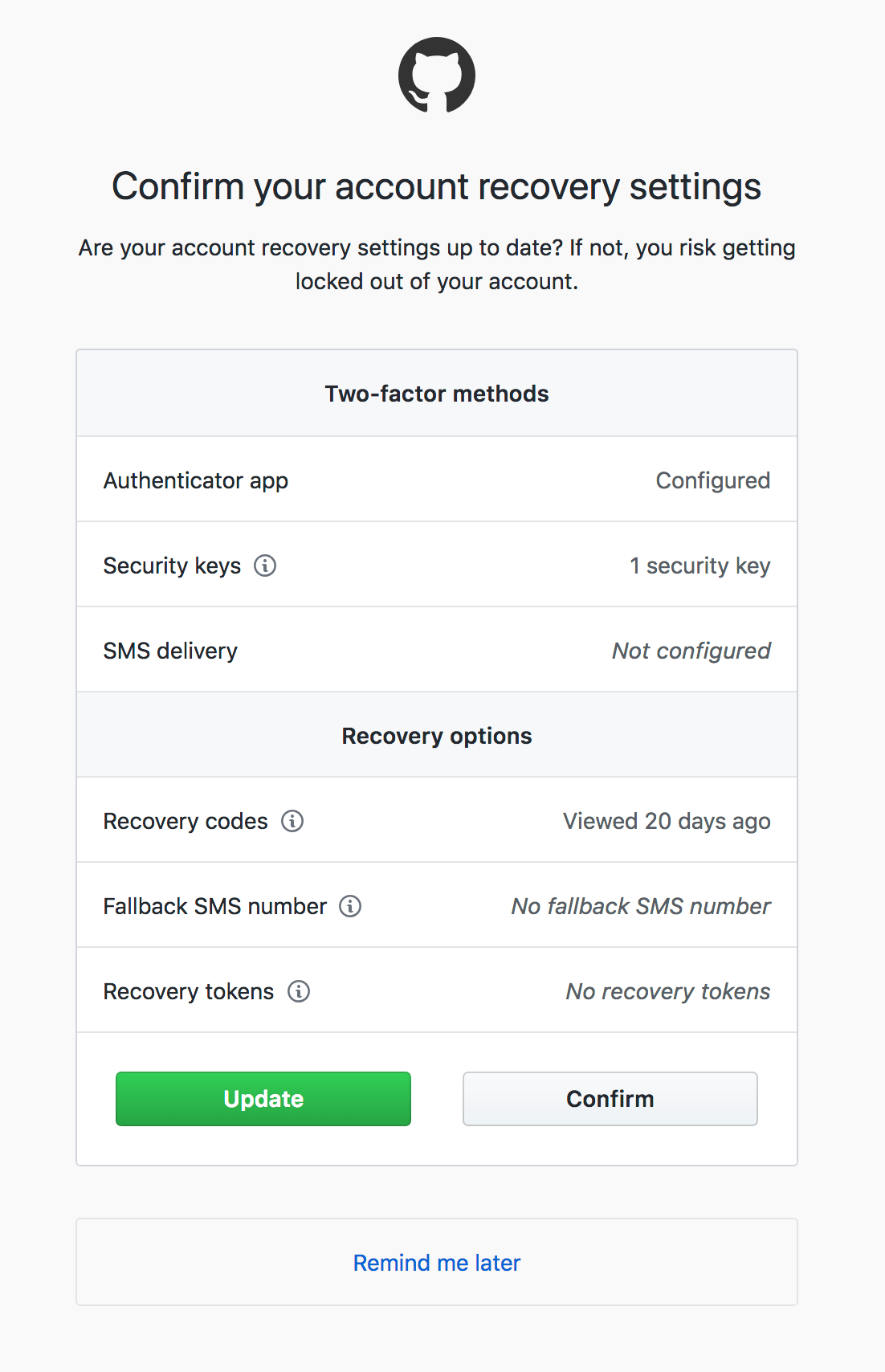
If you have two-factor authentication enabled, GitHub will now periodically remind you to review your 2FA setup and recovery options. We highly recommend using a 2FA authenticator application that supports cloud backups in the event your phone is lost, stolen, or falls in the ocean.
These new account security enhancements will help improve the security of your account. We hope you will take this opportunity to review the security of your account. Balancing security, usability, and recoverability is a personal decision.
- Update your password to a long, unique value that is generated by a password manager. Consider a cloud-synchronized password manager.
- Use two-factor authentication. Using a TOTP application is more secure than using SMS to deliver codes, but has a higher chance of irrecoverable loss leading to account lockout. Consider a cloud-synchronized application that supports securely backing up your two-factor credentials.
- Ensure you have a method of recovering your account if you lose access to your two-factor device. Having a hardware U2F key is a secure option. Also, be sure to store your two-factor backup codes somewhere secure like a password manager or a secure physical location. Consider linking your account to Facebook via Recover Accounts Elsewhere.
- Update your primary email address if necessary and determine if a backup email address is desirable. These settings will determine which email address(es) are allowed to perform a password reset.
- Review other GitHub credentials. While we remove SSH keys, deploy keys, OAuth authorizations, and personal access tokens that have not been used in a year, it’s always a good idea to manually review them periodically.
- Consider signing up for HaveIBeenPwned notifications. You do not need to provide a password.
If you haven’t already set up two-factor authentication on your GitHub account, visit your account settings and click on the “Security” tab.
Written by
Related posts

GitHub availability report: January 2026
In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Pick your agent: Use Claude and Codex on Agent HQ
Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What the fastest-growing tools reveal about how software is being built
What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.