Enhanced push protection features for developers and organizations
Introducing two new secret scanning push protection features that will enable individual developers to protect all their pushes and organizations to gain insights and trends across their repositories.
Since the initial release for free public repositories earlier this year, one quarter of public repositories with secret scanning enabled have also been leveraging push protection to prevent you from pushing code that contains secrets. We’re thrilled by this adoption from the open source community. By fixing potential leaks before they occur, you and your teams can reduce the risk of a security incident and save countless hours of remediation time and productivity loss.
Previously, push protection enablement was only possible at the repository level, leaving you reliant on administrators to update the repository settings. Also, organizations were unable to quantify the total impact of push protection at a macro level. Until now.
We’re enhancing push protection’s reach and data insights with two new features in public beta–push protection for users and push protection metrics for organizations. Now, you can ensure pushes to public repositories are protected across the entire GitHub platform within your personal account settings. And organization owners have access to insights and trends around preventing secret leaks.
Push protection for users
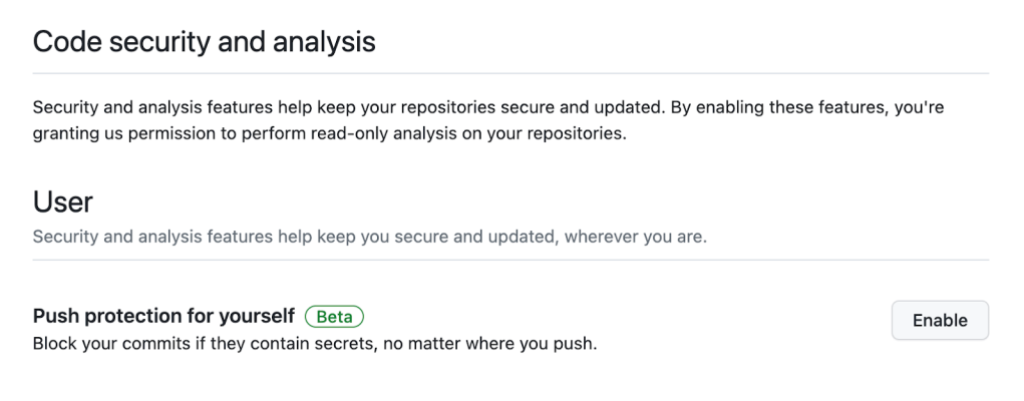
Push protection for users allows you to take control of your code security by enabling push protection within your individual settings. You no longer have to worry whether the repository administrator has push protection enabled or not, but rather have the peace of mind that every line of code you commit to public repositories is push protected.
This is starting as an opt-in feature during beta, but soon it will be enabled by default for all GitHub Free users.
Push protection metrics
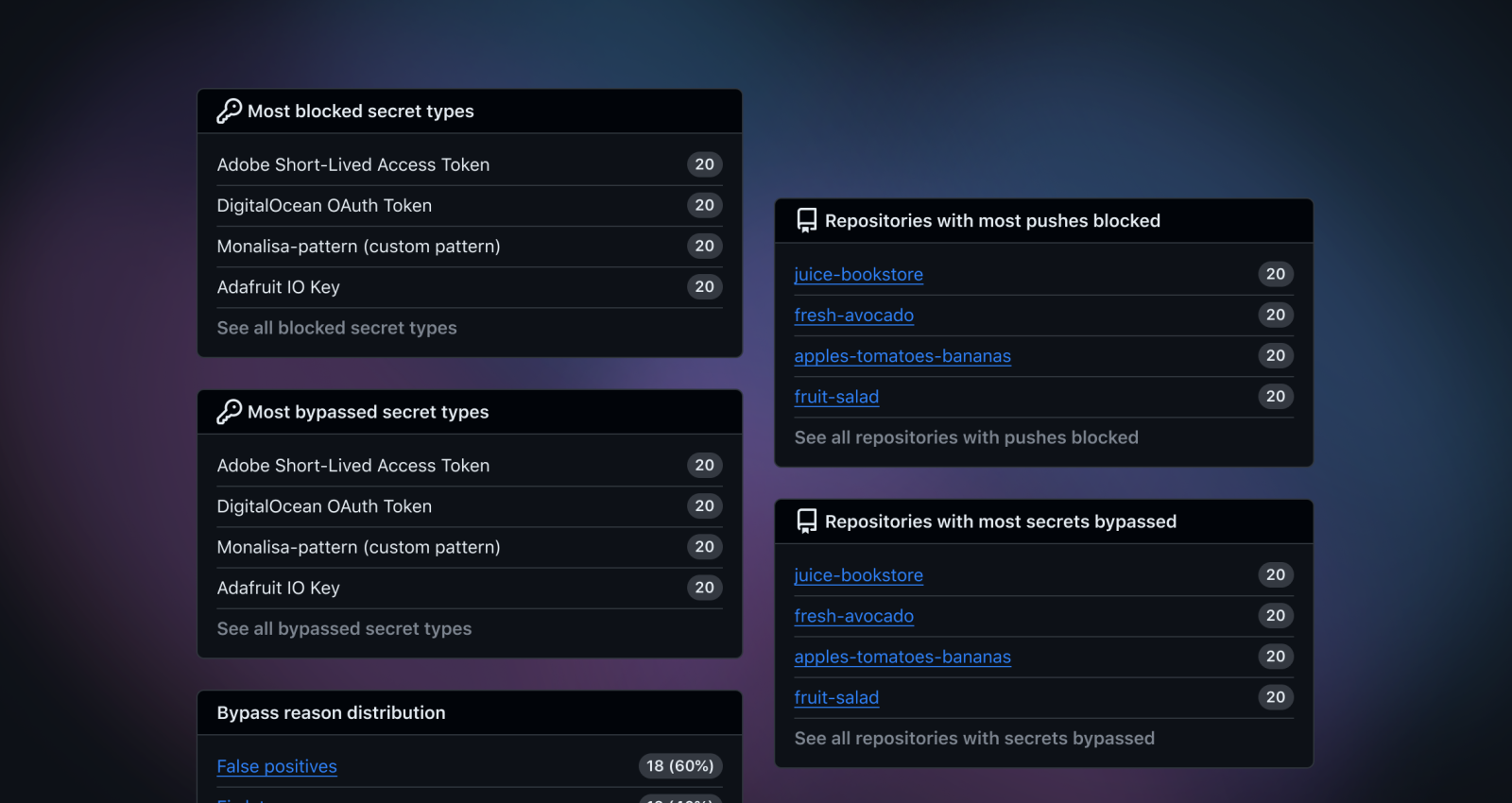
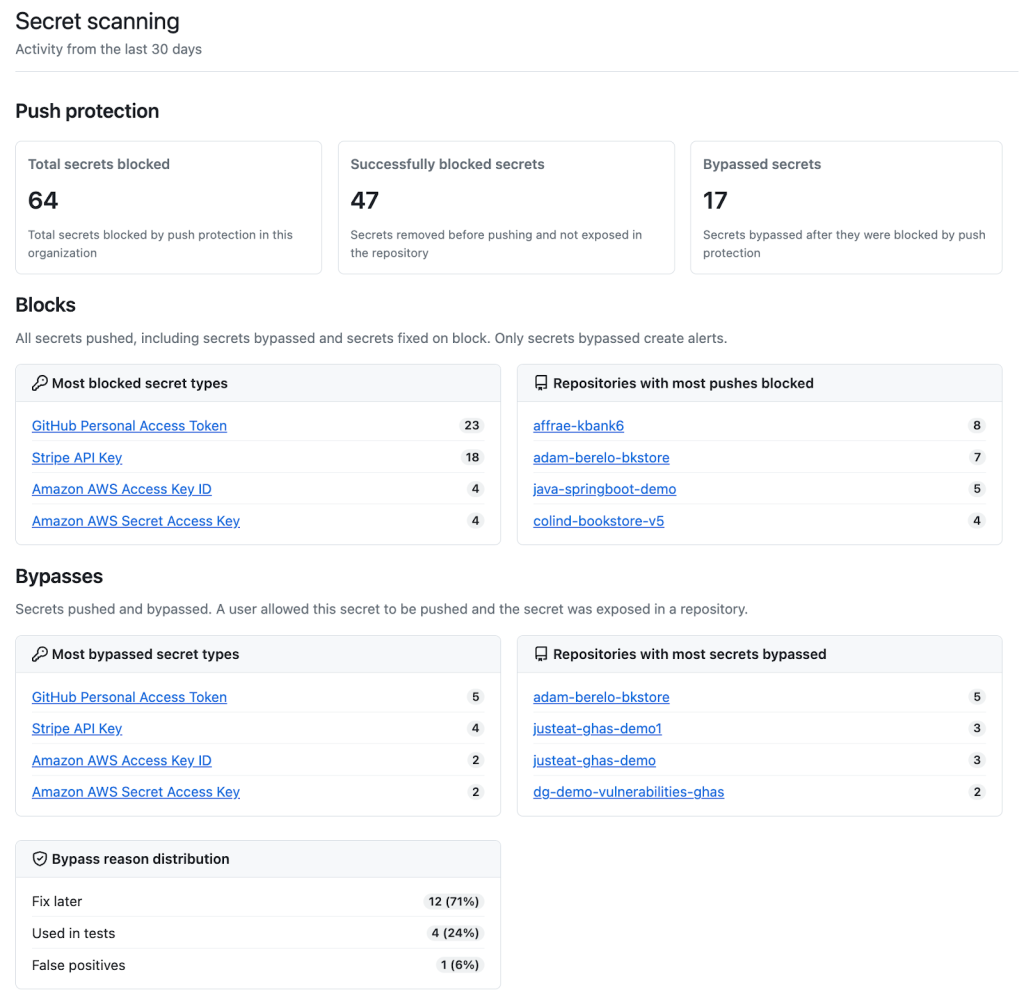
In addition to empowering you and fellow developers, we are introducing push protection metrics for organizations. This feature allows organizations to measure the impact of push protection across their repositories through valuable data insights and trends, such as problematic secret types or repositories.
Organizations now have visibility into the number of total secrets intercepted by push protection, as well as the number of successful blocked secrets and the number of bypassed secrets. Push protection will also show what secrets are most commonly blocked and what repositories have the most push protection alerts. Finally, they’ll receive bypass insights–the most common reasons why bypasses occur as well as the most frequent secret types and repositories associated with bypassed push protection alerts.
How to get started
You can access these new features with a few clicks.
Push protection for users. Head to your personal GitHub settings by clicking on your avatar and then “Settings.” From there scroll down to “Security” and click to “Code security & analysis.” Under the “User” section, click “Enable” next to “Push protecting for yourself” to ensure that every line of code you commit will be safeguarded by push protection.
Push protection metrics. Organization owners and security managers can access push protection metrics within security overview. Within your organization view click on the “Security” tab. From there on the left hand side you can click “Secret scanning” under “Metrics.” Here, you can dive into the data around push protection and optimize your strategy around preventing secret leaks.
More information
For more information and detailed instructions, check out our documentation and reach out to our code security community for additional support.
Tags:
Written by
Related posts

From pair to peer programmer: Our vision for agentic workflows in GitHub Copilot
AI agents in GitHub Copilot don’t just assist developers but actively solve problems through multi-step reasoning and execution. Here’s what that means.

GitHub Availability Report: May 2025
In May, we experienced three incidents that resulted in degraded performance across GitHub services.

GitHub Universe 2025: Here’s what’s in store at this year’s developer wonderland
Sharpen your skills, test out new tools, and connect with people who build like you.