Detect secrets in your code more accurately with dry runs for custom patterns now available in GitHub Advanced Security
Learn how you can seamlessly define trusted custom secret patterns to detect secrets unique to your organization with GitHub Advanced Security.
We’re on a mission to eliminate credential leaks. To that end, GitHub Advanced Security’s secret scanning can detect and create alerts for over 180 secret types. However, many organizations have unique secret types that could also lead to the exposure of critical systems or intellectual property. In June of 2021, we added support for custom patterns to help detect these.
Since introducing support for custom patterns, we’ve worked closely with our community of users to improve them. To make it easy to iterate and experiment, we added support for dry runs, which is now generally available. To add to this, we added the ability to specify additional match requirements to make customer patterns more powerful. Because mistakes happen, we also added support for editing existing patterns. And to keep track of changes, we included custom pattern updates in the audit log.
Custom Patterns with dry runs helps us ensure we’re only catching risks that we care about, and allows us easily filter out other results that another team may not be concerned about in the same way. We can also easily apply at an enterprise level or just at the repository level, because a high risk vulnerability in one repository, may not be viewed the same in another repository. Our developers can work the way we want to work, while staying protected and having the same high bar for security.
– Justin Watts // Director, Engineering Productivity, Telus
Today, custom patterns provide a powerful and easy-to-use way to detect credentials across your enterprise. Since adding support for dry runs in public preview, nearly 50% more customers now use custom patterns.
Define a custom pattern for secret scanning
You can define custom patterns for your enterprise, organization, or repository. Secret scanning supports up to 500 custom patterns for each organization or enterprise account, and up to 100 custom patterns per repository.
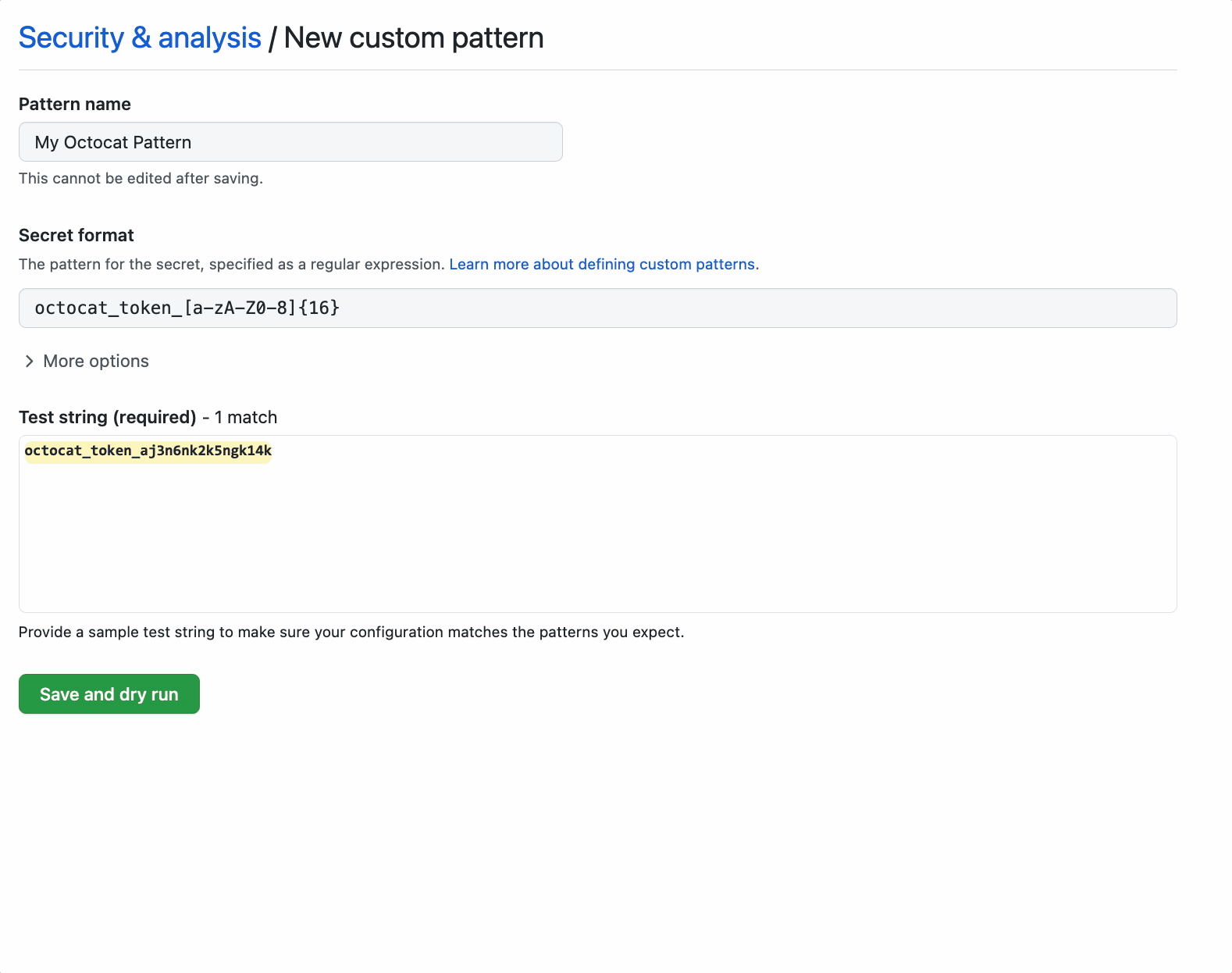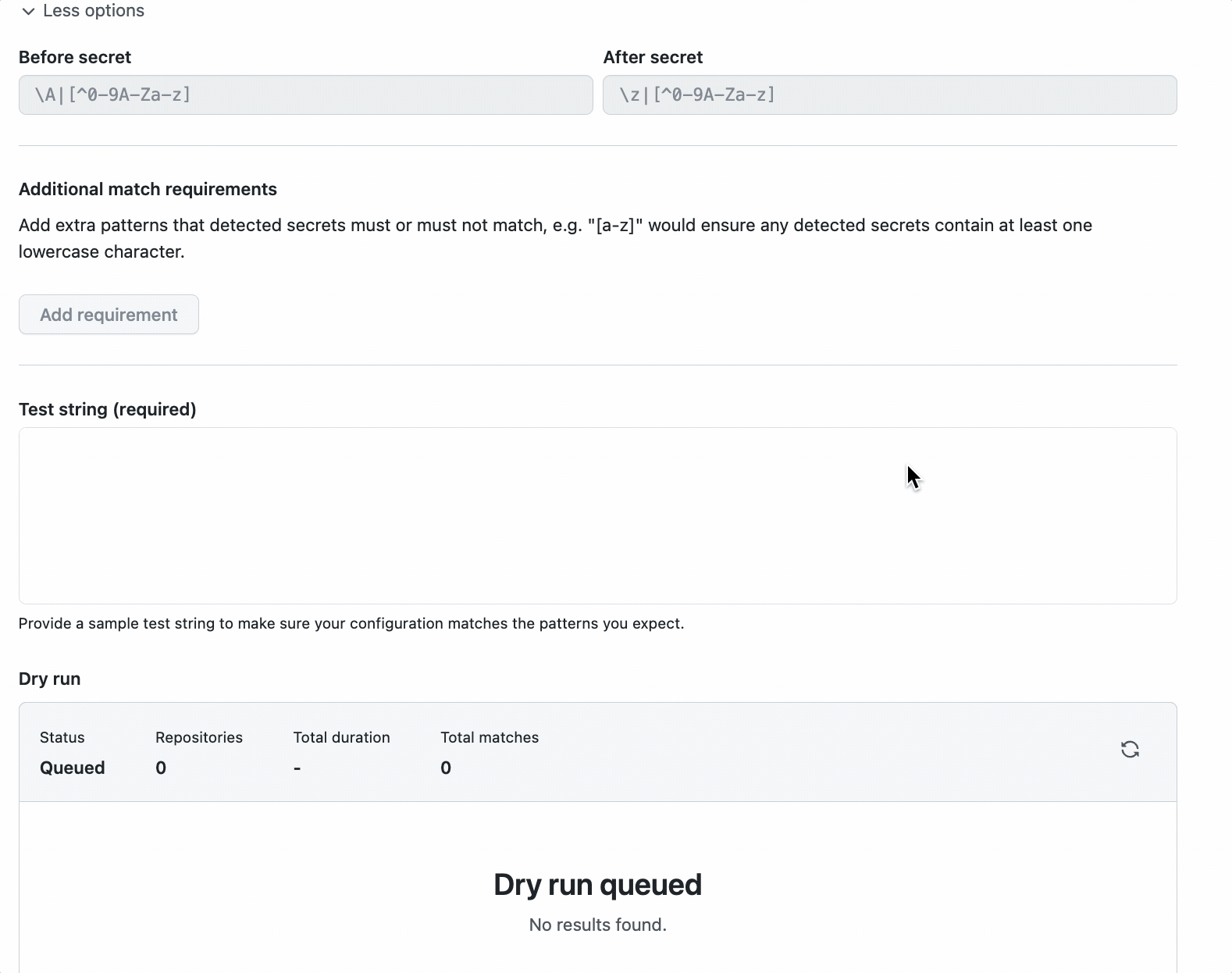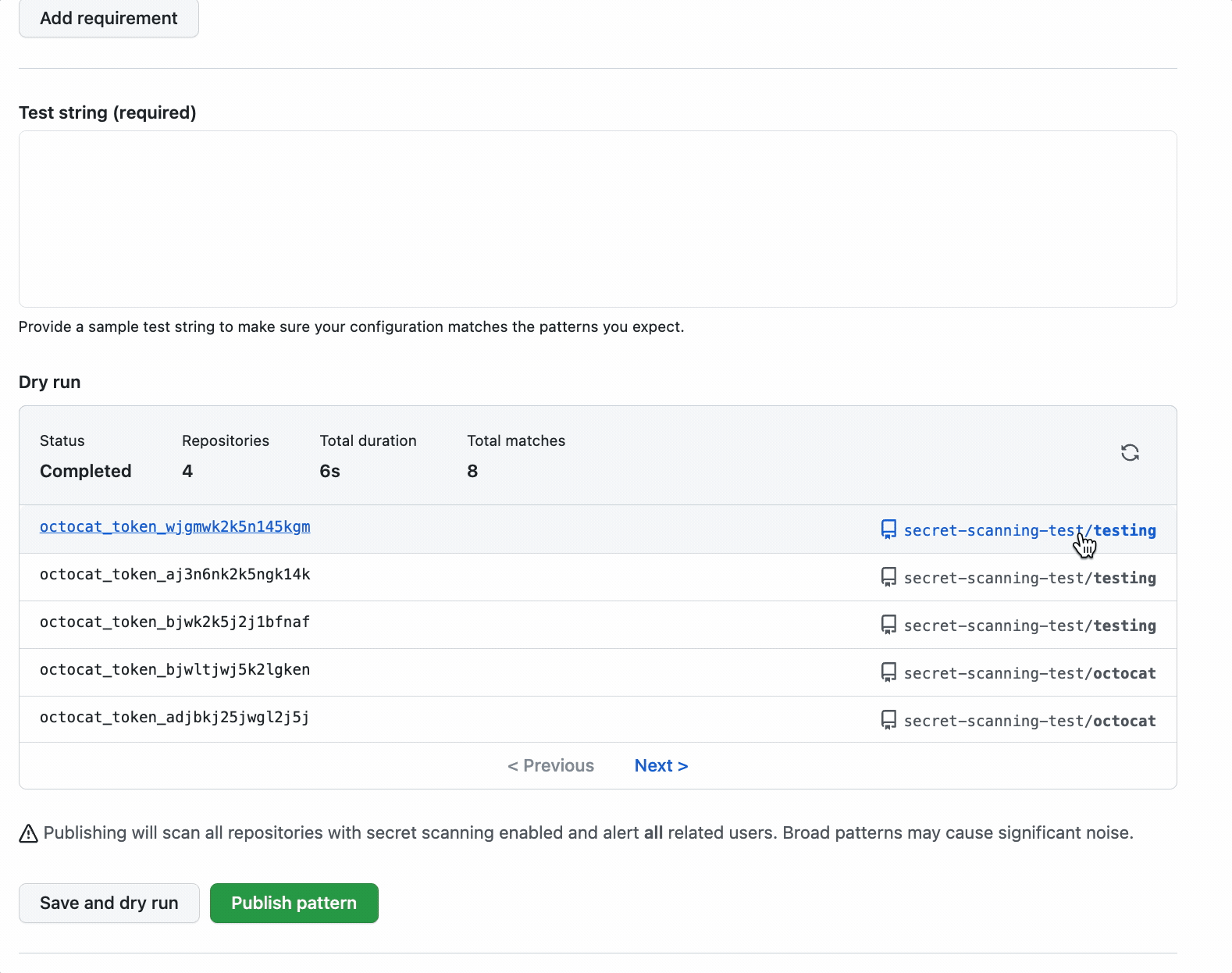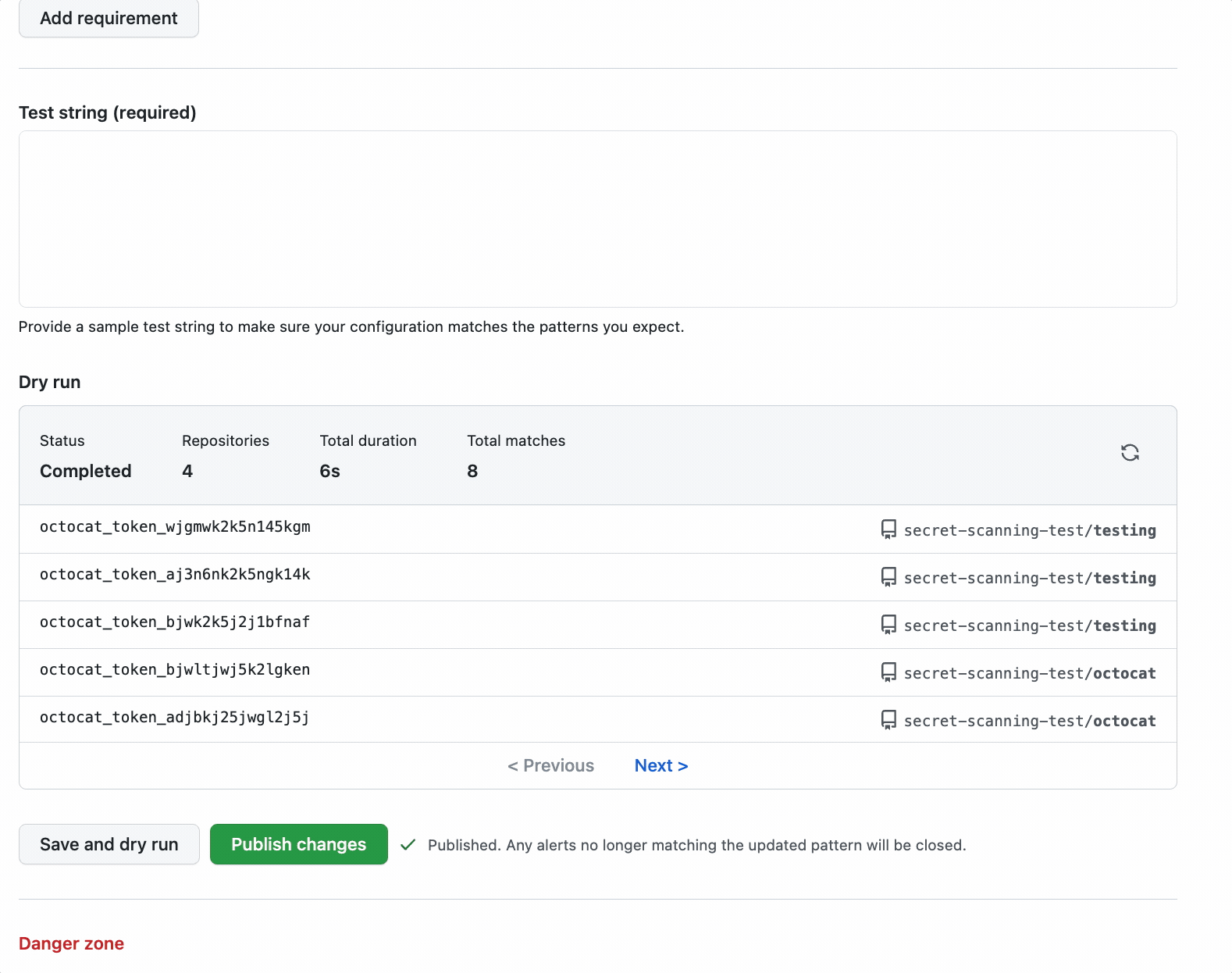
To define a custom pattern, navigate to the custom patterns section under secret scanning, which lives on the security tab of your repository. From there, you can create a new custom pattern.
Once you have defined your pattern’s requirements, you can then save the pattern and conduct a dry run to view unpublished results across all of your repositories. Dry runs typically take a few seconds, so we will save the pattern as a draft and send you an email when the results are ready for review if you want to navigate away from the dry run. We won’t send any other notifications, yet.
Once you are happy with your custom pattern, you can publish your pattern to generate official secret scanning alerts across all of your repositories. Like all our backfills, admins will receive notifications of any detected historical results, and both admins and commit authors will receive notifications of any new alerts from that point onwards.
Learn more about GitHub Advanced Security
GitHub Advanced Security helps secure organizations around the world through its secret scanning, code scanning, supply chain security capabilities, forever-free Dependabot alerts, and Dependabot security updates. To learn more about our secret scanning capabilities or GitHub Advanced Security, check out the following pages:
- Learn more about secret scanning
- Learn more about GitHub Advanced Security
- Watch GitHub Checkout video on dry runs for custom patterns
To try GitHub Advanced Security in your organization or see a demo, please reach out to your GitHub sales partner.
Tags:
Written by
Related posts

GitHub availability report: January 2026
In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Pick your agent: Use Claude and Codex on Agent HQ
Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What the fastest-growing tools reveal about how software is being built
What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.