Learn more about Dependabot alerts, security updates, and version updates.
Dependabot alerts are now visible to more developers
Default settings will allow developers with write and maintain access to see and resolve Dependabot alerts.

Dependabot alerts were launched as GitHub’s first security alerts five years ago. Since then, developers have kept dependency-based vulnerabilities out of their code with over 80 million closed alerts.
Historically, Dependabot alerts have only been available to admin users, but that means the alerts aren’t visible to the developers who are responsible for fixing them. We believe in a developer-first approach to security, so starting next month, we’re shipping a change to better empower developers to keep their code secure.
Starting February 7, anyone with repository write or maintain roles will be able to view and act on Dependabot alerts by default.
What’s changing?
Previously, Dependabot alerts were visible and actionable to developers with admin access to a repository. Starting February 7, Dependabot alerts will be visible and actionable to anyone with repository write and maintain access.
How do I opt in?
No action needed–this change will be applied to all existing and new repositories on February 7.
What’s not changing?
This doesn’t affect custom roles, the Security Manager role, or organization permissions for Dependabot alerts. Only repository admins can enable or disable Dependabot alerts.
What about alert notifications?
This change also will not affect your alert notification or repository watching settings. So, if you aren’t opted in to Dependabot alert notifications based on your user settings, you won’t receive any.
If you are currently receiving notifications on alerts, any new repositories will be included with existing Dependabot alerts notifications.
- Dependabot alerts digests and email notifications: these aggregate lists will include any new repositories (if you’re watching all activity or security alert activity for each repository).
- Dependabot alerts web notifications: these GitHub notifications (which also aggregate by vulnerability) will link to any affected repositories as well (again, if you’re watching all activity or security alert activity for that repository).
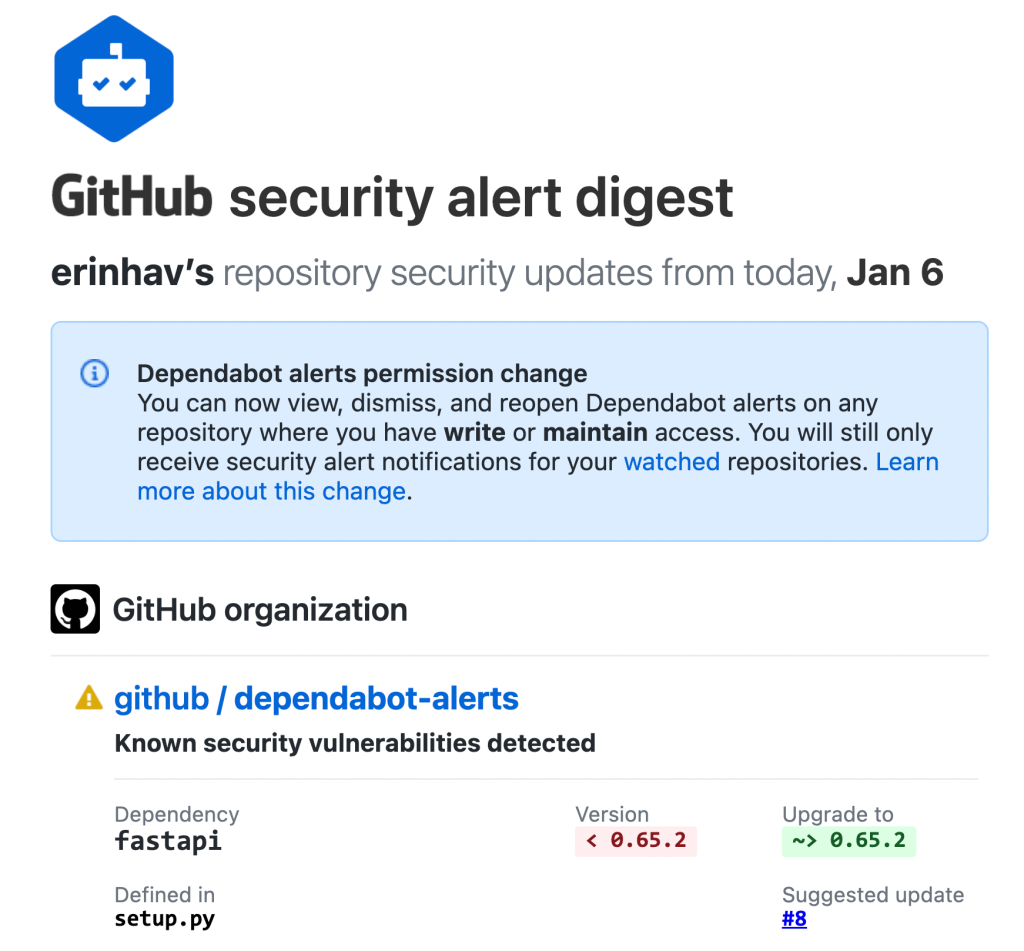
How do I opt out of Dependabot alert notifications for these repositories?
If you don’t want to receive Dependabot alert notifications on any repositories, you can navigate to github.com/watching, which lists repositories where you’re watching all activity, or watching a custom set of activity. You can do this in advance of February 7, when alerts permissions will change.
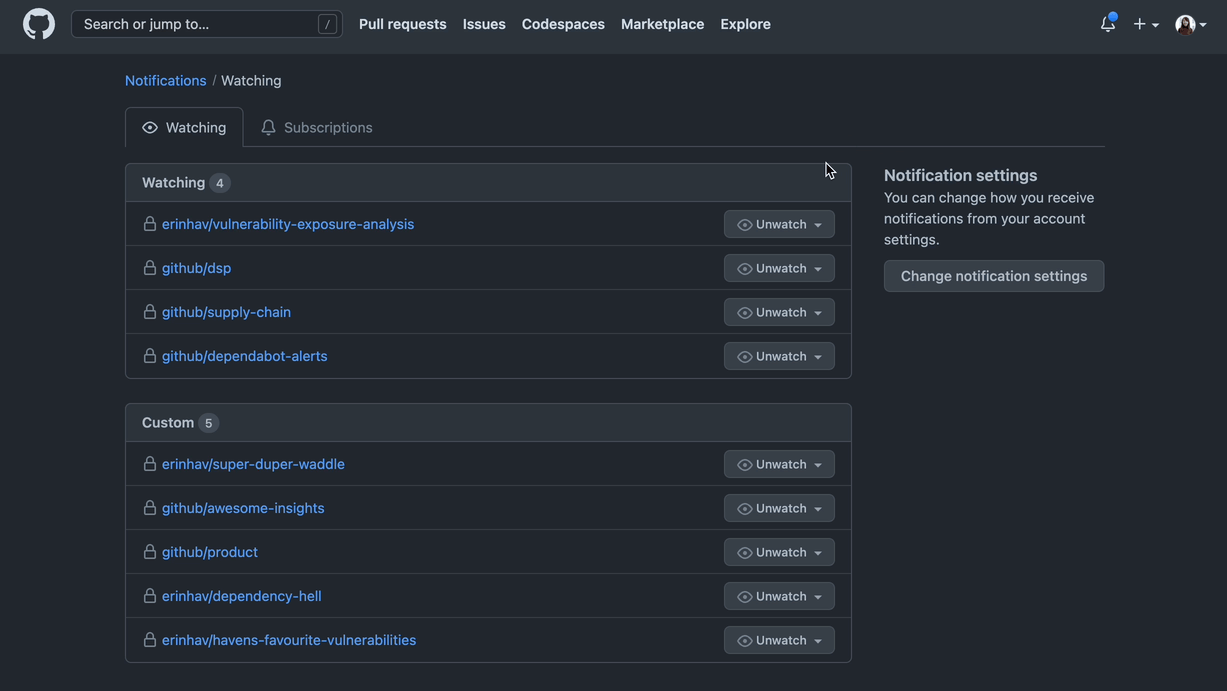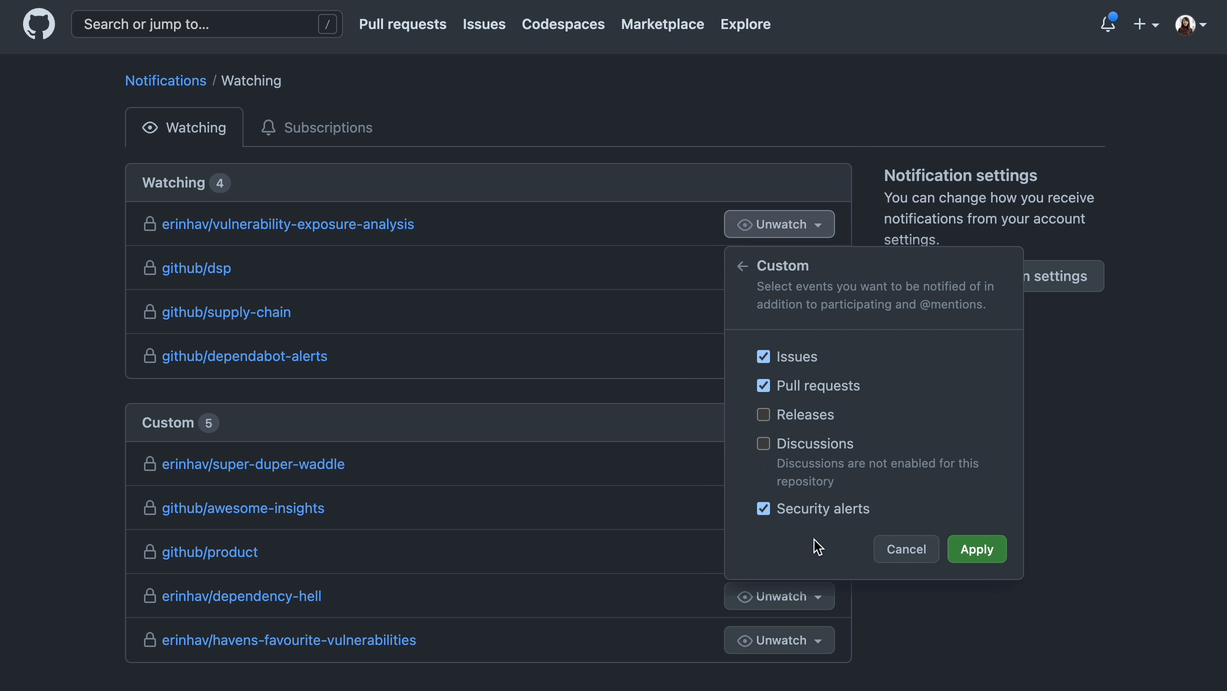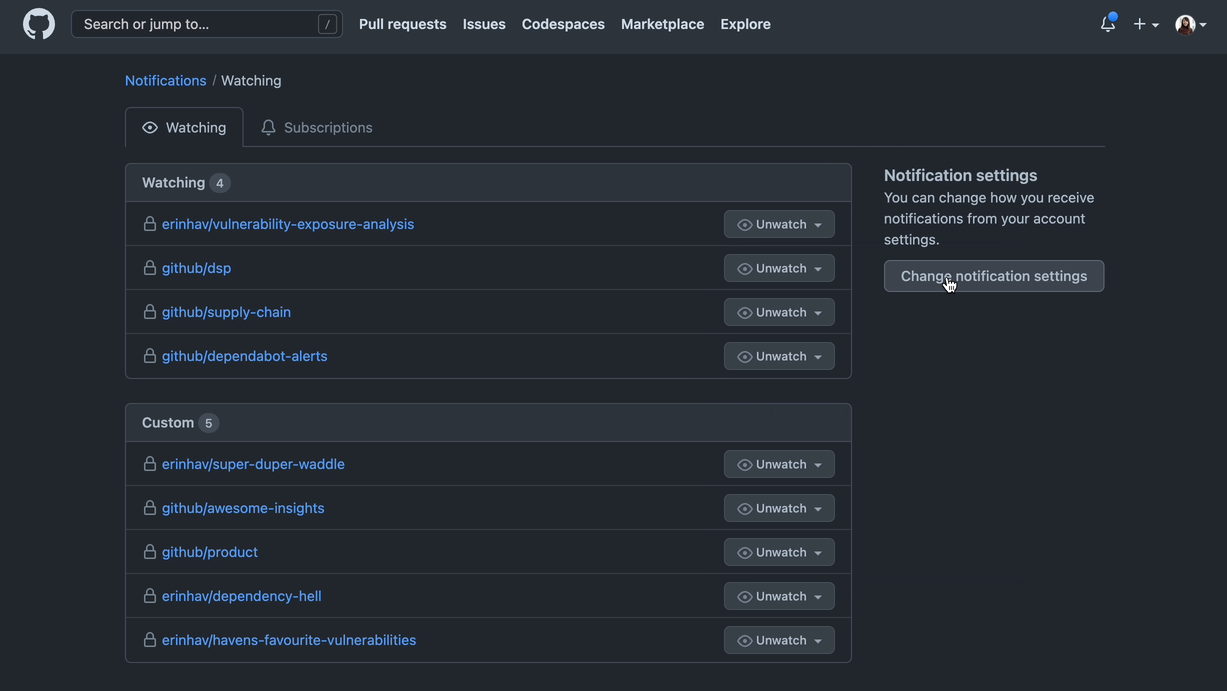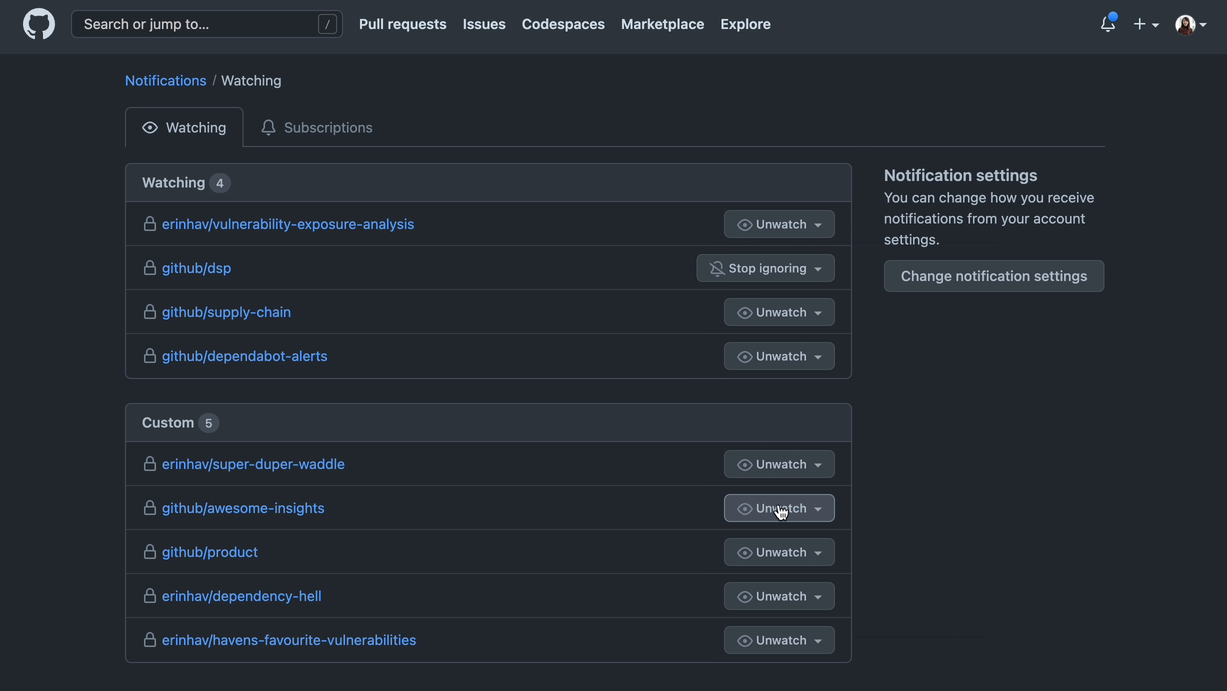
You can also adjust when and how you receive notifications on Dependabot alerts. For example, instead of receiving an email notification when a new vulnerability is detected, you can subscribe to weekly email digests instead.
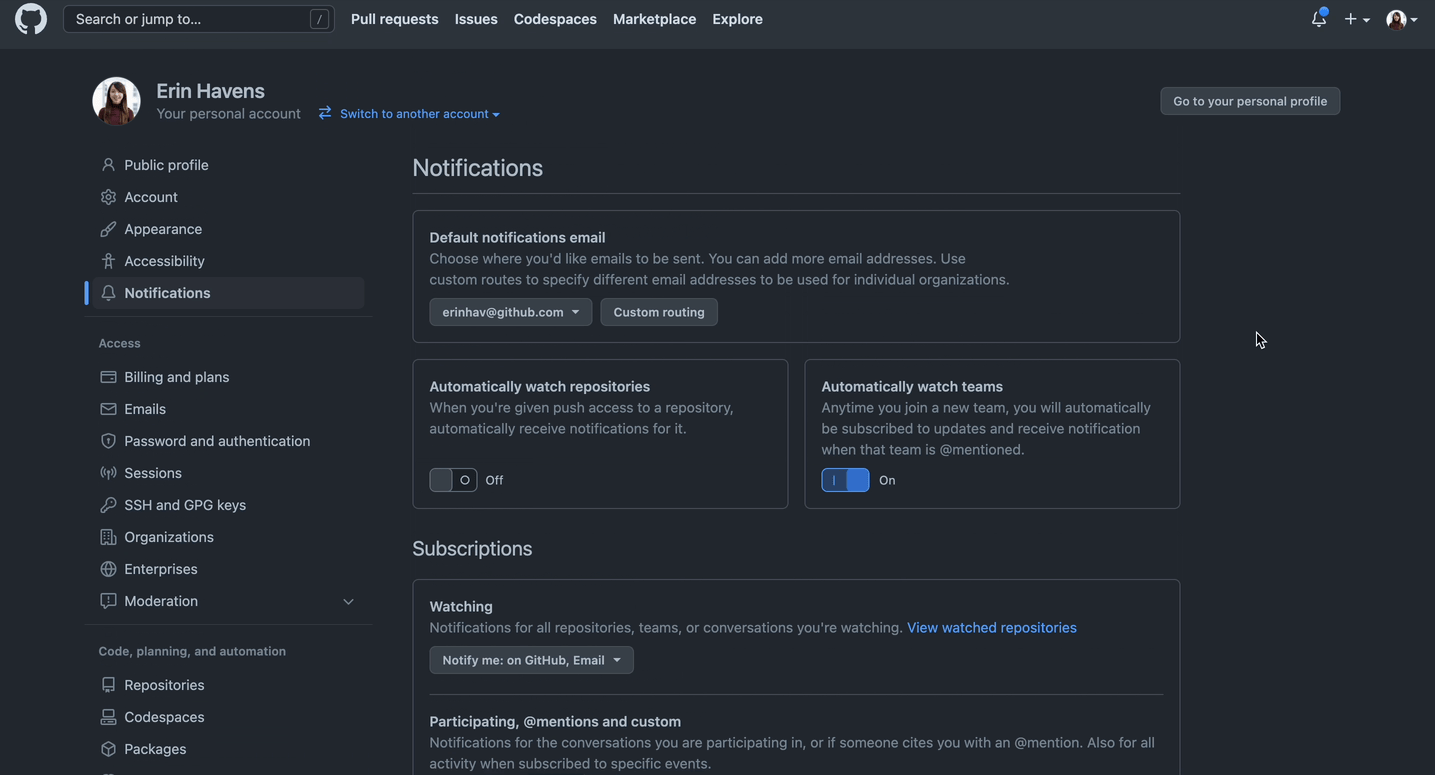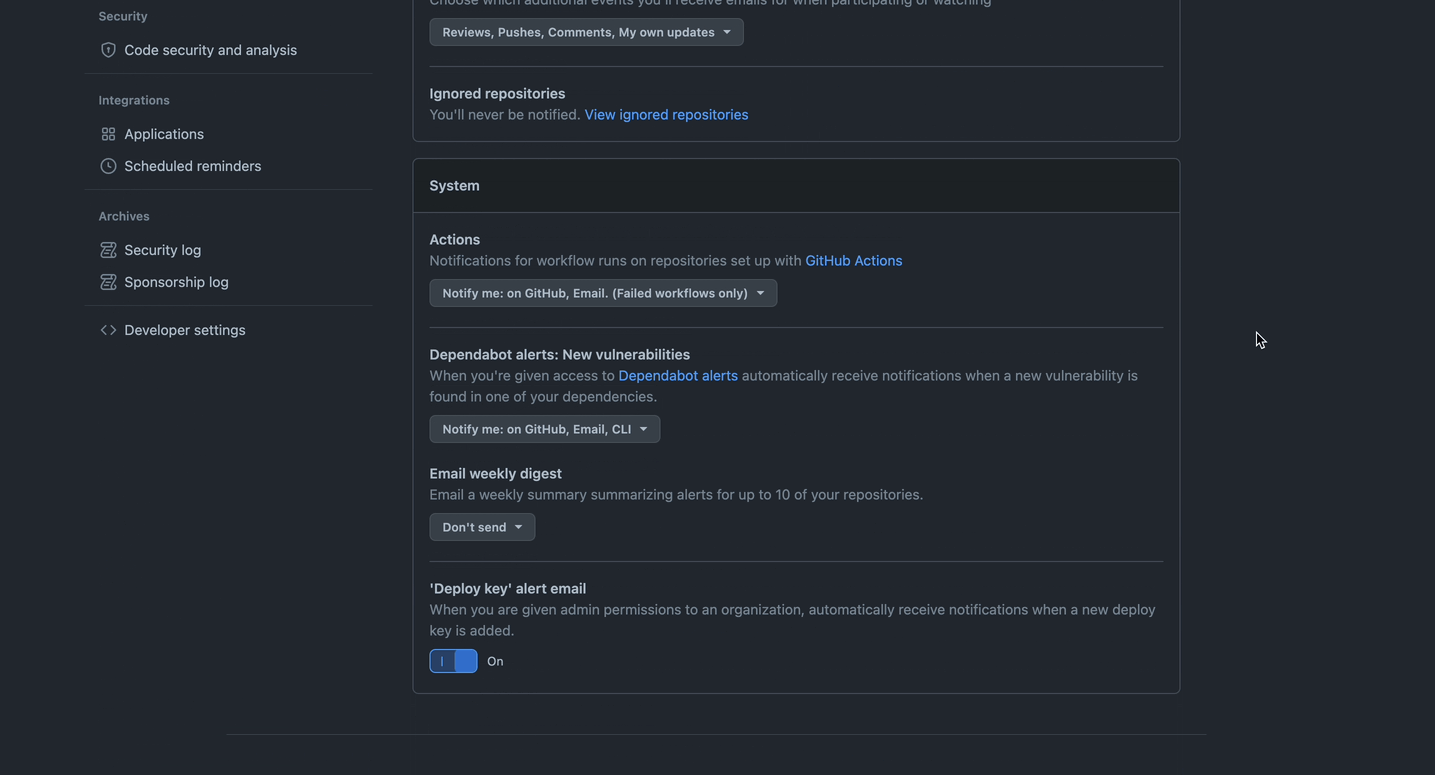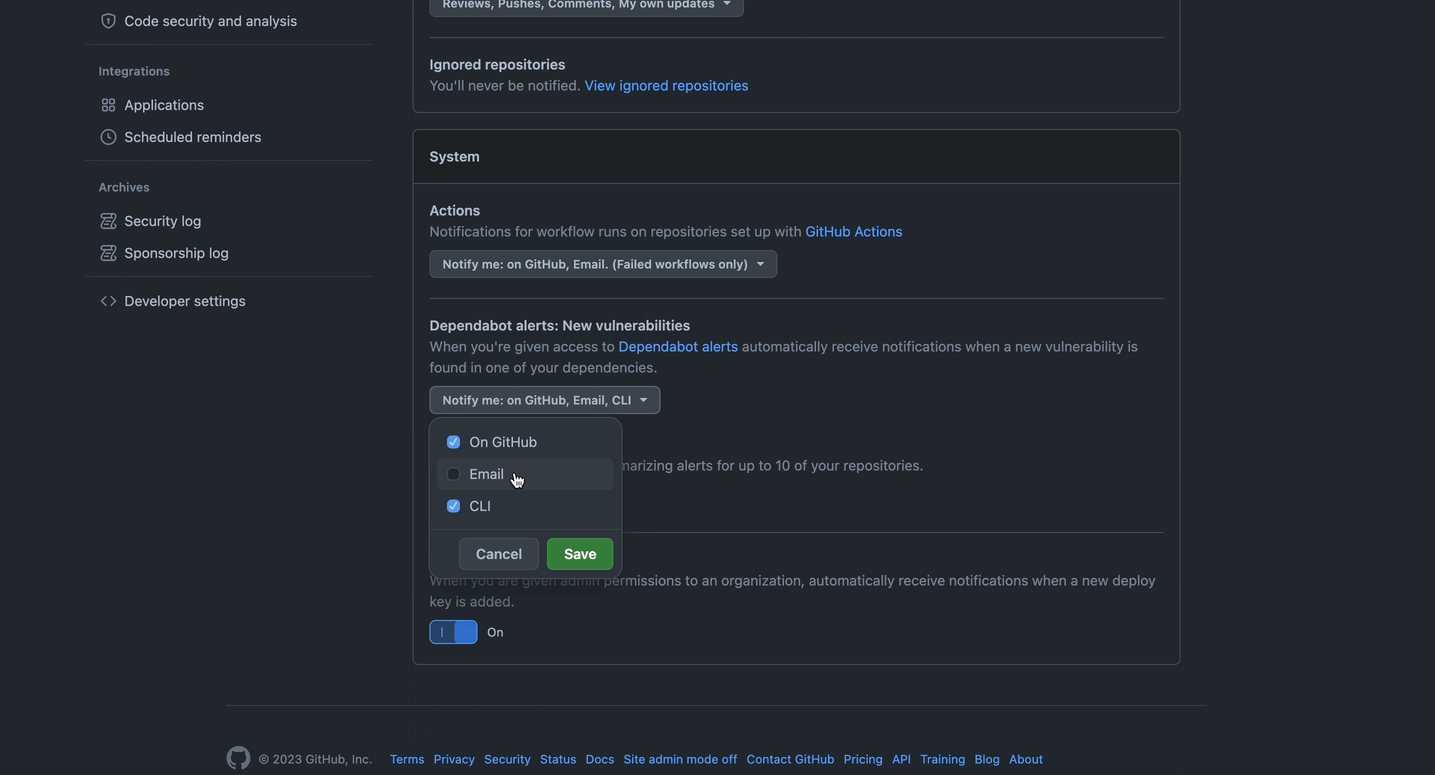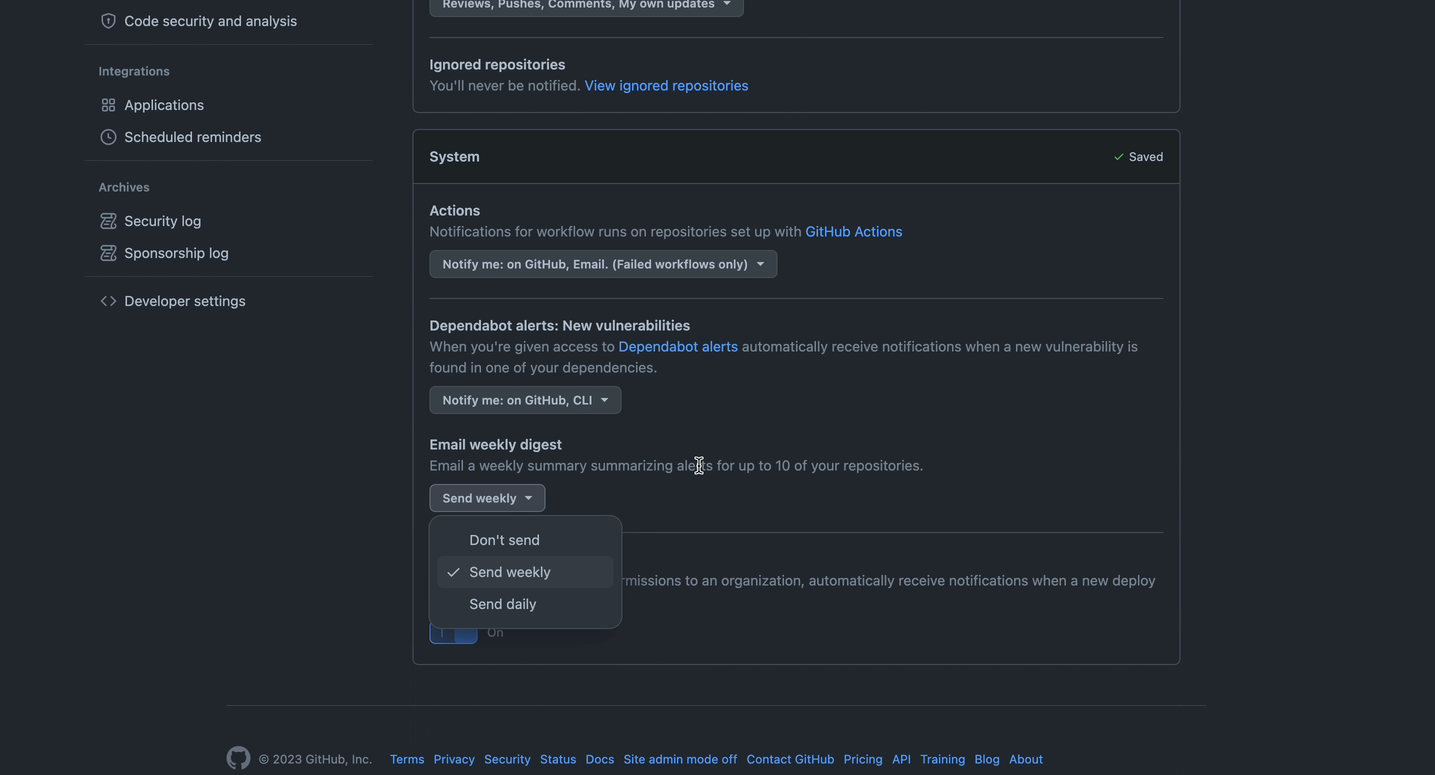
You can adjust your notification settings across email, CLI, and web.
Tags:
Written by
Related posts

GitHub availability report: January 2026
In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Pick your agent: Use Claude and Codex on Agent HQ
Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What the fastest-growing tools reveal about how software is being built
What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.