If you use versioned reusable workflows in GitHub Actions, you can now use Dependabot version updates to keep those workflows up-to-date in your repositories! This is useful for anyone using reusable workflows and pinning references to them from the caller workflow, either by commit SHA or by tag.
Dependency graph and Dependabot now parse and update package-lock.json files set with lockfileVersion: 3, which is used by npm v9. Users will receive Dependabot alerts for dependencies with known vulnerabilities.
What’s new?
This feature makes it easier to enable Dependabot alerts and check enablement status across all your repositories at an enterprise level, with updates across both enablement UI and APIs. These updates will ship today for GitHub.com and will ship for GitHub Enterprise Server users in 3.9.
Changes to the REST API
Dependabot alerts have been added to existing endpoints:
- Enablement for existing repositories: Enable or disable a security feature for all repositories in an enterprise
- Enablement for new repositories: Enable a security feature for any new, future repositories for an enterprise
- Status checking: Get code security and analysis features for an enterprise
‘Code security and analysis’ settings
You can also adjust your enablement settings from your enterprise settings page (under ‘code security and analysis’). Options include enable all, disable all, and enable for new repositories for your enterprise.

What's new?
Starting today, anyone with repository write or maintain roles will be able to view and act on Dependabot alerts by default. Previously, only repository admins could view and act on Dependabot alerts. This change will help ensure that alerts are visible to the same developers responsible for fixing them.
How do I opt in?
No action needed–this change will be applied to all existing and new repositories starting today.
What's not changing?
This doesn’t affect custom roles, the Security Manager role, or organization permissions for Dependabot alerts. Only repository admins can enable or disable Dependabot alerts.
What about alert notifications?
This change also will not affect your alert notification or repository watching settings. So, if you aren’t opted in to Dependabot alert notifications based on your user settings, you won’t receive any.
If you are currently receiving notifications on alerts, any new repositories will be included with existing Dependabot alerts notifications.
Learn more about this change here.
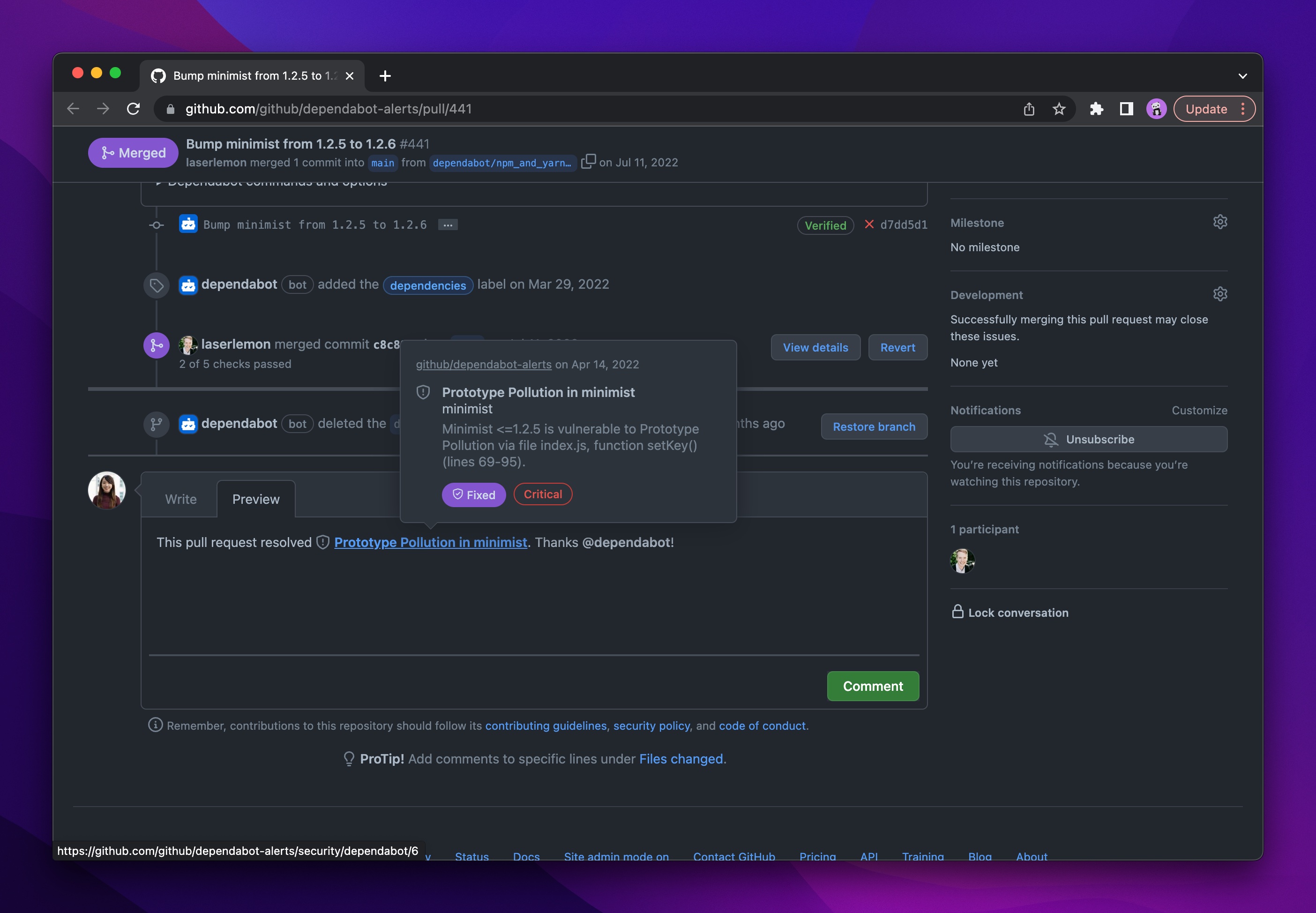
Starting today, when linking to a Dependabot alert in an issue and or pull requests, anyone with permissions to view the alert will see a rich Dependabot alert mention, with detailed hovercard and a prettified link with the title of the alert.
Card details include:
- Alert title, repository, and description
- Date that the alert was opened
- Alert severity and status (fixed, dismissed, or open).
What’s new?
Starting today, Dependabot will pause automated pull request activity if you haven’t merged, closed, or otherwise interacted with Dependabot for over 90 days. To resume activity when you’re ready, simply interact with Dependabot.
This change will help Dependabot be more focused to the repositories you care about.
When will Dependabot become paused?
This change only applies to repositories where Dependabot pull requests exist but remain untouched. If no Dependabot pull requests have been opened, Dependabot will never become paused.
The following must be true for at least 90 days:
- Has not had a Dependabot PR merged
- Has not had changes made to the Dependabot config file
- Has not had any @dependabot comment-ops performed
- Has not had any Dependabot PRs closed by the user
- Has received at least one Dependabot PR before the 90 day window
- Has at least one Dependabot PR open at the end of the 90 day window
- Has had Dependabot enabled for this entire period
How will Dependabot let me know?
Dependabot will add a banner notice to open Dependabot pull requests, the repository settings page (under “Dependabot”) as well as your Dependabot alerts page (if Dependabot security updates are affected).
Who can use this feature?
This change does not apply to Dependabot alerts or subsequent notifications. So, only repositories that have automated Dependabot version updates or security updates, but haven’t interacted with these pull requests for a while, will be affected.
This change will start to roll out today, expanding through January 2023 to include all repositories owned by individuals and by organizations with free and Team plans.
Later, it will roll out to GitHub Enterprise Cloud and GitHub Enterprise Server customers, where this improvement has the added benefit of enhanced efficiency with your self-hosted GitHub Actions runners.
Learn more about this change.
We've hardened our Dependabot support for private registries such that it will no longer make package requests to public registries if private registries are configured for the following ecosystems:
- Bundler
- Docker
- Gradle
- Maven
- npm
- Nuget
- Python
- Yarn
Learn more about configuring Dependabot version updates to only access private registries.
Dependabot security updates now supports the Pub ecosystem, making it easier for you to fix vulnerable dependencies in your Dart or Flutter apps. With security updates enabled, Dependabot will automatically raise a pull request to update vulnerable Pub dependencies to the latest patched version.
GitHub's audit log allows organization and enterprise admins to quickly review the actions performed by members of their organization or enterprise. For Dependabot alerts, the audit log includes actions such as repository enablement, creation or reintroduction of alerts, dismissal of alerts, and resolving of alerts.
The audit log now supports the following improvements:
- Dismissal comments, if provided with a Dependabot alert, are now displayed in the audit log
- The audit log API for Dependabot alerts now supports several new fields:
alert_number,ghsa_id,dismiss_reason, anddismiss_comment. - Additional minor improvements, including links back to the alert and correct timestamps added to events.
This release is available for organization and enterprise admins (including GHES 3.7 and later).
For more information, view documentation on Dependabot alerts in the GitHub audit log.
Dependabot security updates now supports the GitHub Actions ecosystem, making it easier for you to fix vulnerable GitHub Actions dependencies. With security updates enabled, Dependabot will automatically raise a pull request to update vulnerable GitHub Actions used in your workflows to the minimum patched version.
Dependabot expands its existing Hex private registry support beyond Hex organizations by adding support for self-hosted Hex repositories. You can configure your self-hosted Hex package repository as a private registry for use with Dependabot version updates. Special thanks to @sorentwo for their contribution to Dependabot!
Learn more about configuring Dependabot version updates and its supported ecosystems and package managers.
Dependabot version updates now proactively updates Docker image tags in Kubernetes manifests.
When specifying the Docker ecosystem in dependabot.yml include an entry for each directory where a Kubernetes manifest which references Docker image tags is located. Kubernetes manifests can be either Kubernetes Deployment YAML files or Helm charts. Dependabot will parse the unrendered version of the manifest in order to keep your Docker image tags updated.
Learn more about configuring Dependabot version updates.
Dependabot helps you keep your dependencies up-to-date with Dependabot version updates. These pull requests are configured via a dependabot.yml file.
Starting today, if you fork a repository with an existing dependabot.yml, Version updates will be disabled by default. To enable Dependabot pull requests based on this configuration, you can click “enable” from your forked repository’s “Code security and analysis” settings page.
After enabling Dependabot version updates, you will also be able to disable with a single click from this settings page.

Learn more about configuring Dependabot version updates.
You can now retrieve all your Dependabot alerts at the GitHub enterprise level via the REST API. This new API endpoint supplements the recently introduced Dependabot alerts REST API, Dependabot alerts org-level REST API, and Dependabot alerts webhook.
For more information, see Dependabot alerts in the REST API reference or learn more about Dependabot alerts in our documentation.
GitHub Actions workflows often specify the version of an action using the commit SHA. Since commit SHAs are immutable, this ensures that Actions always picks the same version. Commit SHAs, however, are not very human friendly, so best practice is to include the semver version in a comment next to the SHA. Dependabot will now update the semver version in comments when updating Actions workflows with a commit SHA version.
Dependabot is open source, and we're thankful to first-time contributor @jproberts for this great addition!
Removing the security vulnerability banner
The yellow banner stating "We found potential security vulnerabilities in your dependencies" is being removed. Please use the "Security" alert count in your repository navigation as an indicator for when your repository has Dependabot alerts. You can also adjust your notifications settings to opt-in to email and web notifications, as well as email digests for your Dependabot alerts.
About this change
We've been working to steadily improve our security alert notifications and indicators. As part of our notifications strategy, we are removing this legacy banner.
Available alert notifications and indicators
Today, when Dependabot detects a dependency-based vulnerability, Dependabot lets you know based on your user notifications settings and repository watching settings. You can opt to receive:
- Web-based notifications on alerts in your GitHub inbox
- Email based notifications on alerts
- Email digests (weekly or daily roll-ups of alerts).
From the UI, you can also use the "Security" alert count in your repository navigation as an indicator for when your repository has alerts. This Security tab includes the count for all active Dependabot alerts, code scanning alerts, secret scanning alerts, and any security advisories that you have permissions to view.
Learn more about GitHub Advanced Security, Dependabot alerts, and configuring notifications for alerts.
Dependabot now supports updates to Python dependencies for pyproject.toml files that follow the PEP 621 standard for our supported Python package managers.
Learn more about Dependabot's supported ecosystems and package managers.
Dependabot now supports now supports the increase-if-necessary versioning strategy for the Python ecosystem.
This allows you to reduce Dependabot version updates when your current dependency requirement is already satisfied by a new version.
Learn more about configuring versioning strategies in your dependabot.yml file.
Dependabot has added support for updating dependencies in Yarn v2 and Yarn v3 manifests (package.json, and yarn.lock files). This is in addition to the existing support for Yarn v1. There is no action required for existing repositories where Dependabot security updates is enabled, however, if you would like to receive proactive updates with Dependabot version updates, you should add configuration for the npm ecosystem to your dependabot.yml file.
For more information:


