GitHub Actions policy now supports blocking and SHA pinning actions
GitHub Actions is powered by a diverse ecosystem of first-party and community contributed actions. If one of these actions has a vulnerability or is compromised by a malicious actor, it can impact all of its dependents in the supply chain.
Tools like Dependabot can identify and upgrade actions versions with known vulnerabilities to help mitigate exposure. However, when an action is compromised to include malicious code, such as exfiltrating secrets or utilizing the permissions granted to the workflow to modify code or releases, users must act quickly and decisively to limit their exposure to these malicious changes. This release provides new features that allow developers and administrators to better respond and proactively limit the impact of compromised dependencies.
Block specific actions or versions
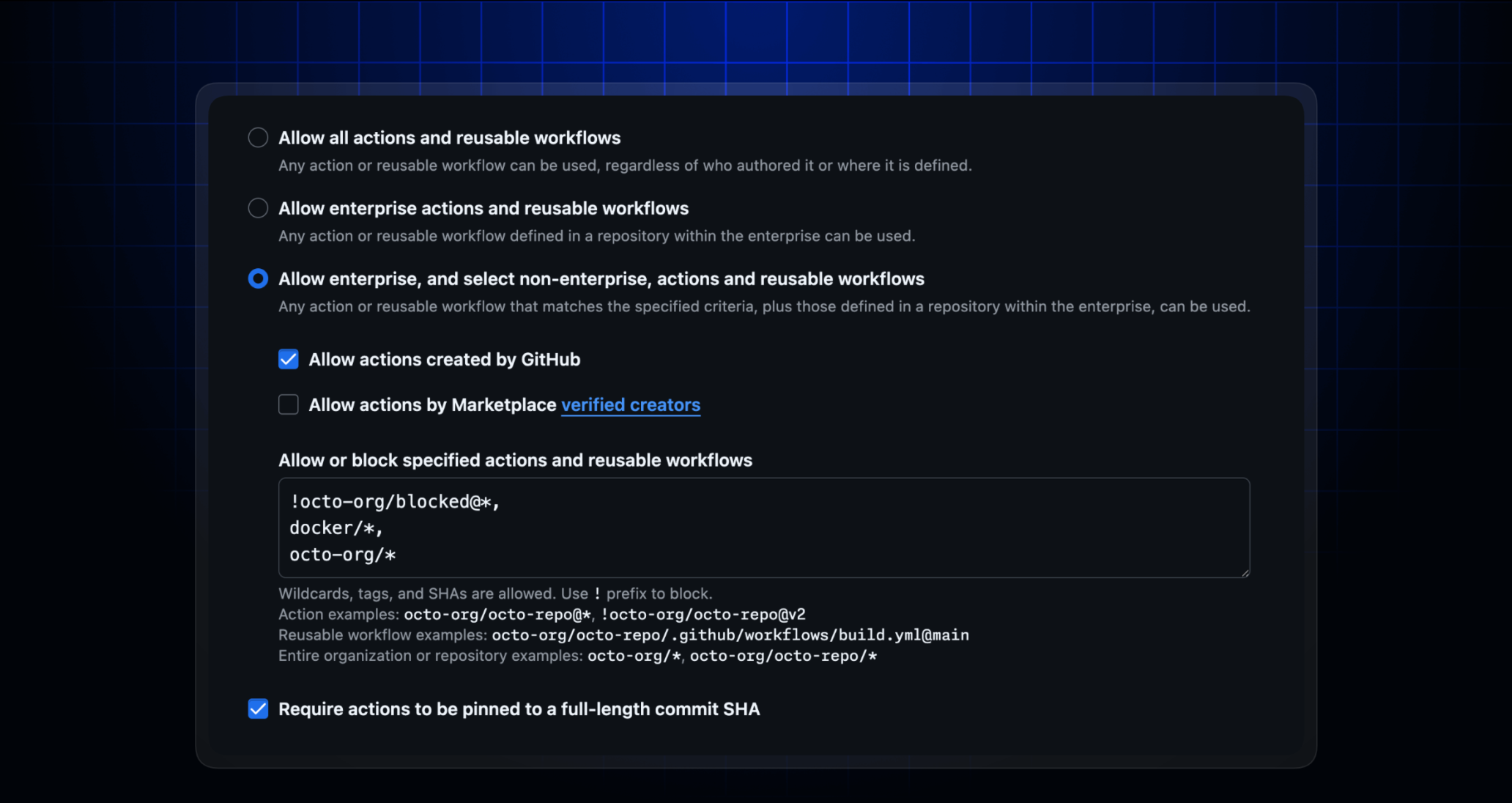
To provide better governance and respond to third-party workflows that are identified as malicious, the allowed actions and reusable workflows policy now supports explicit blocking. Prefix an entry with ! to block a specific action or version. The blocklist is evaluated last, overriding any other policy that would otherwise allow the action.
Enforce SHA pinning
To proactively limit the impact of a compromised dependency, GitHub recommends that workflows pin dependency versions to a specific commit SHA. This will prevent malicious code added to a new or updated branch or tag from being automatically used. Administrators can now enforce the use of SHA pinning through the allowed actions policy. A new checkbox appears under each radio selection, except when actions are disabled at the enterprise, organization, or repository level. The policy will check for a full commit SHA, and any workflow that attempts to use an action that isn’t pinned will fail.
Documentation
To enforce these new policies, refer to our updated documentation on allowed actions and reusable workflows and SHA pinning enforcement. The GitHub Well-Architected Framework has been updated to reflect these policies and recommended practices for GitHub Actions security.
Roadmap
Hardening the open source and GitHub Actions ecosystem is an ongoing focus and GitHub is introducing immutable releases towards this goal of strengthening supply chain security. Once a release is marked immutable, its assets and Git tag cannot be changed or deleted. The feature also adds release attestations for verifiable artifact integrity and integrates with protection rulesets, supporting both UI and API workflows.
For the GitHub Actions ecosystem, the benefits include the ability to pin tags with immutable references, preventing potential malicious updates to existing tags and enabling dependable updates via Dependabot. Workflows can now consume trusted, unalterable assets, and deployment pipelines gain improved stability and reproducibility through the use of immutable artifacts.