Release
GitHub Copilot Extensions now supported in JetBrains IDEs
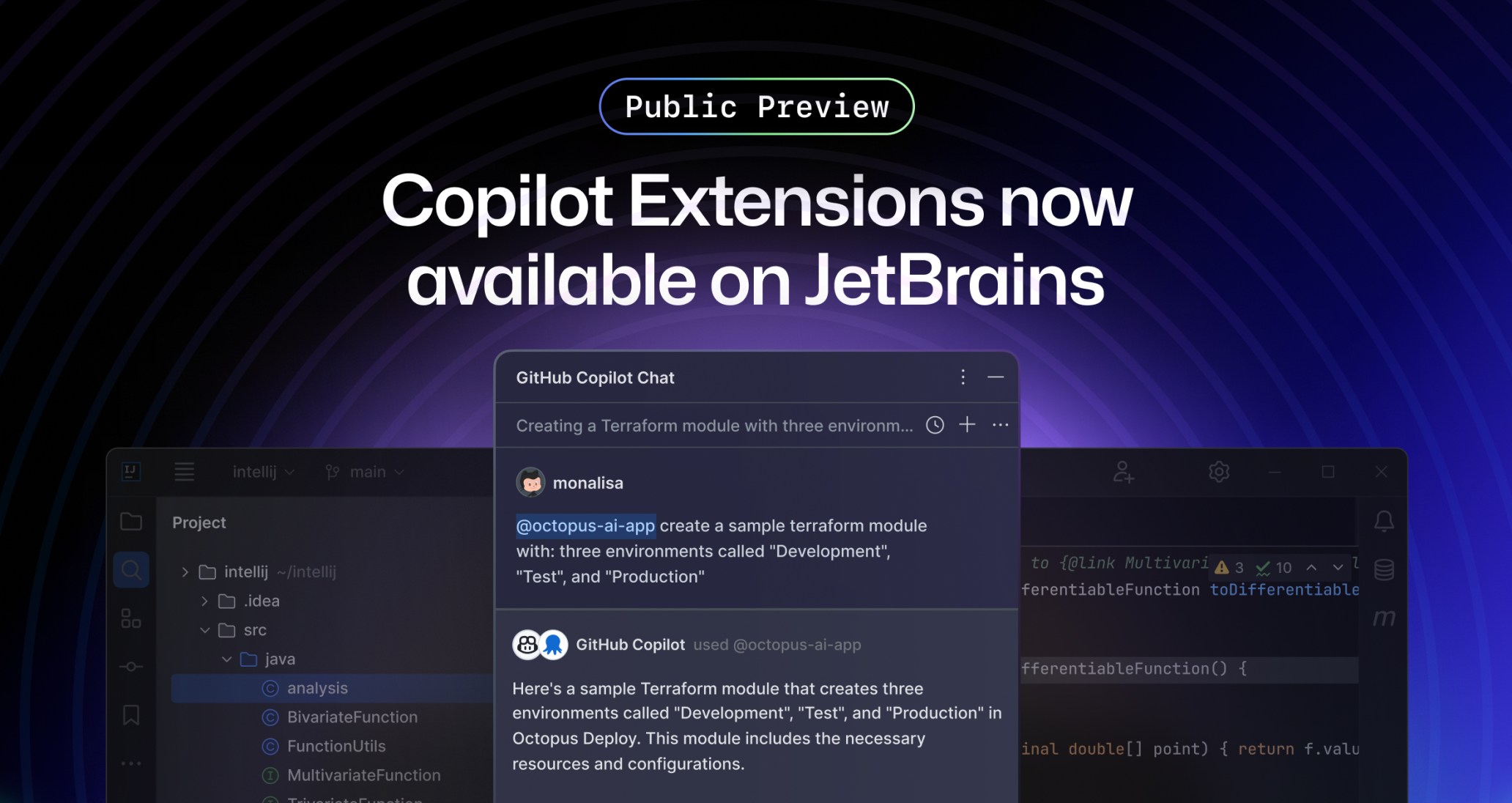
GitHub Copilot Extensions are now available in public preview for JetBrains IDEs! With Copilot Extensions, you can expand GitHub Copilot’s capabilities and context directly within your preferred JetBrains IDE environment. Use extensions to query third-party tools or private data using natural language, all without leaving your favorite editor.
What’s new ✨
- Full Copilot Extensions support across JetBrains IDEs
- Seamless integration with IntelliJ IDEA, PyCharm, WebStorm, and more
- Access to the complete GitHub Marketplace extensions ecosystem
- Natural language interactions with your development tools
Key features 🚀
- Query external tools and services in natural language, without context switching
- Access private data securely through extensions
- Customize your Copilot Chat experience in JetBrains IDEs
Getting started 🔧
- Update to the latest version of the GitHub Copilot plugin for JetBrains IDEs
- Enable Copilot Extensions in your IDE settings
- Browse and install extensions on the GitHub Marketplace
- Start using an extension with ‘@’ followed by the extension name, then type in your prompt
Developers can also build custom extensions for internal use or publish them to the GitHub Marketplace. For more information, see our documentation on building Copilot Extensions.
Requirements 📋
- Access to GitHub Copilot
- Compatible JetBrains IDE
- Latest GitHub Copilot plugin version for JetBrains IDEs
- One or more Copilot Extensions installed (VS Code chat participants are not supported)
To learn more, see our docs on using and installing Copilot Extensions.