GitHub Copilot General Availability in the CLI
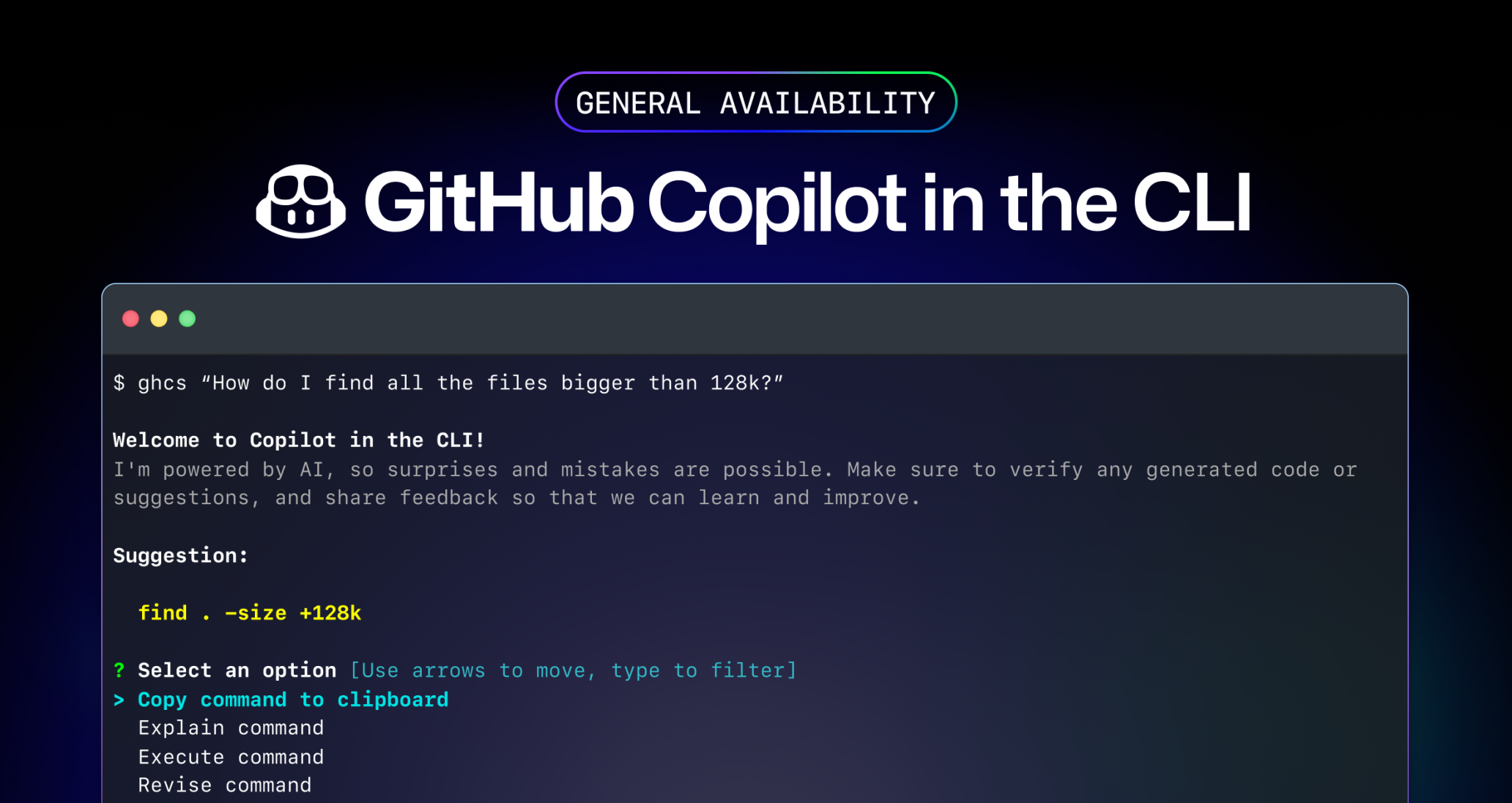
GitHub Copilot in the CLI is now generally available
We are excited to announce Copilot in the CLI is now generally available (GA) for all our Copilot Individual, Business, and Enterprise customers.
Copilot in the CLI allows users to access the power of GitHub Copilot to get command suggestions and explanations without leaving the terminal. Starting today, developers can also use GitHub Copilot to execute suggested commands based on feedback shared during the public beta.
GitHub Copilot in the CLI has also gained a couple of helper aliases for Bash, PowerShell, and Zsh. The new gh copilot alias command generates shell-specific configuration for ghcs and ghce aliases. These aliases use fewer keystrokes to jump into the gh copilot experience. Additionally, the new ghcs alias streamlines the process for executing commands suggested while making them available for later reuse!
How to get started?
If you were already using Public Beta:
- Update the extension to v1.0.0 by running
gh extension upgrade gh-copilot.
If you haven’t enabled Copilot in the CLI yet or coming from the GitHub Next technical preview
- Copilot Individual users: You automatically have access to the Copilot in the CLI.
- Copilot Business and Enterprise users: Your organization admins will need to grant you access to Copilot in the CLI.
After receiving access to Copilot in the CLI, consult our guide on how to install the tool and get started.
How to give us your feedback?
We are dedicated to continuous improvement and innovation. Your feedback remains a crucial part of our development process, and we look forward to hearing more about your experiences with GitHub Copilot in the CLI. Please use our public repository to provide feedback or ideas on how to improve the product.