Category Forms on GitHub Discussions
Maintainers of GitHub repositories can now use Category Forms to create templates for their Discussions, which means that users can start new discussions with all the necessary information already included. We hope this leads to less repetitive back and forth conversation with maintainers, as users are more likely to capture all relevant details in their first Discussion post.
Similar to Issue Forms, maintainers can create a discussion template, which will live in .github/DISCUSSION_TEMPLATE/. Each template will map 1:1 with the available Discussion Categories slugs. For example, the template for the “Announcements” category will be .github/DISCUSSION_TEMPLATE/announcements.yml. Once created, Category Forms in Discussions will be familiar to users who have seen them in issues:
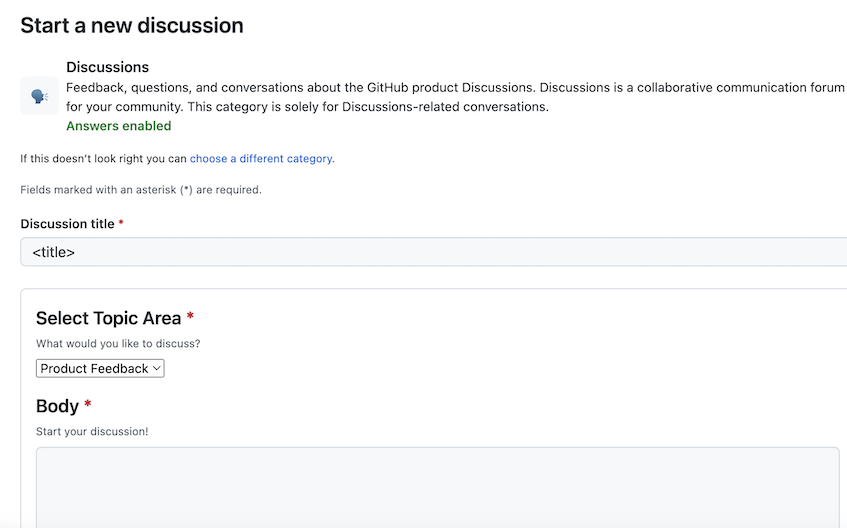
Learn more about Category Forms
For questions or feedback, please visit our community.
