Visit our documentation to learn more about push protection, GitHub Advanced Security, or the secret scanning partner program.
Introducing secret scanning validity checks for major cloud services
Secret scanning now performs validity checks for select AWS, Microsoft, Google, and Slack tokens.

At GitHub, we launched secret scanning with the mission of eliminating all credential leaks. In support of this mission, this year we’ve made secret scanning and secret scanning push protection free on public repositories to help open source users detect and prevent secret leaks. We also shipped push protection metrics for GitHub Advanced Security customers to better understand trends across their organization.
But a good security experience isn’t just about reducing noise and delivering high-confidence alerts–it should make your remediation efforts simpler and faster. A key component of remediation is assessing whether a token is active or not. To that end, we introduced validity checks for GitHub tokens earlier this year, which removes manual effort and friction from the process. You can see a token’s status within the UI, saving you time and allowing you to prioritize remediation efforts more efficiently. This is especially useful when you have to comb through hundreds or even thousands of alerts.
Today, we’re excited to announce that we have extended validity checks for select tokens from AWS, Microsoft, Google, and Slack. These account for some of the most common types of secrets detected across repositories on GitHub. This is just the beginning–we’ll continuously expand validation support on more tokens in our secret scanning partner program. You can keep up to date on our progress via our list of supported patterns.
How to get started
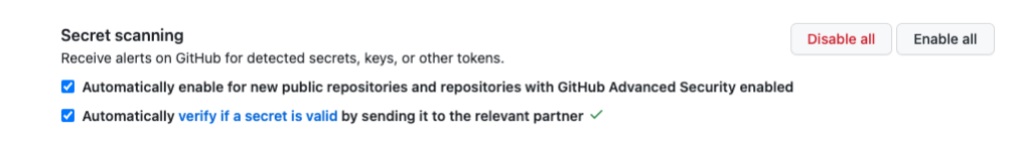
Enterprise or organization owners and repository administrators can activate validity checks by going to “Settings” and “Code security and analysis.” Scroll down to “Secret scanning” and check the box for “Automatically verify if a secret is valid by sending it to the relevant partner” to activate validity checks for non-GitHub tokens.
Once the setting is enabled, you can see within alerts whether the token is active or not. We perform checks periodically in the background, but you can also conduct a manual refresh by clicking ‘Verify secret’ in the top right corner.

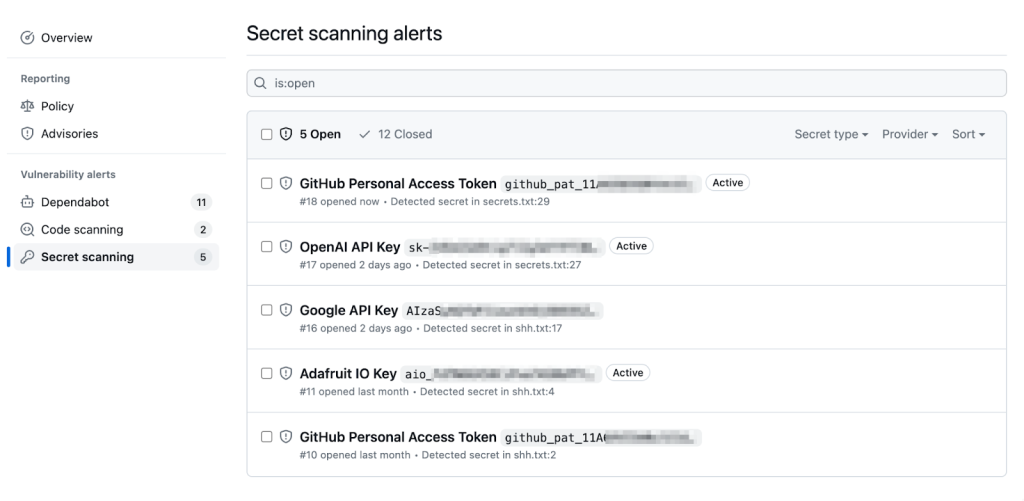
Validity checks are another piece of information at your disposal when investigating a secret scanning alert. We hope this feature will provide greater speed and efficiency in triaging alerts and remediation efforts. If you have feedback to share, please reach out to us in the Code Security community discussion.
Tags:
Written by
Related posts

GitHub availability report: January 2026
In January, we experienced two incidents that resulted in degraded performance across GitHub services.

Pick your agent: Use Claude and Codex on Agent HQ
Claude by Anthropic and OpenAI Codex are now available in public preview on GitHub and VS Code with a Copilot Pro+ or Copilot Enterprise subscription. Here’s what you need to know and how to get started today.

What the fastest-growing tools reveal about how software is being built
What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their teeth? Let’s take a look at Octoverse data to find out.