Private vulnerability reporting now generally available
Open source maintainers and security researchers embrace a new best practice to report and fix vulnerabilities.

Today, we’re announcing the general availability of private vulnerability reporting, a private collaboration channel that makes it easier for researchers and maintainers to report and fix vulnerabilities on public repositories. “One of the biggest struggles as a researcher has been making initial contact to disclose the vulnerability to the maintainer,” explains Jonathan Leitschuh, GitHub Star, GitHub Security Ambassador, and Senior Open Source Security Researcher for the Open Source Security Foundation (OpenSSF) Project Alpha-Omega. “Private vulnerability reporting is a massive step forward.”
At GitHub Universe 2022, we announced the public beta of private vulnerability reporting to test a solution to these problems and get feedback from maintainers and security researchers. Since then, maintainers for more than 30k organizations have enabled private vulnerability reporting on more than 180k repositories, receiving more than 1,000 submissions from security researchers.
Benefits for maintainers
But numbers alone don’t tell the whole story, so we reached out to a number of these early adopters, including Jordan Tucker, maintainer of JSON5. With more than 60 million weekly downloads, JSON5 ranks in the top 0.1% of most depended-on packages on npm, and has been adopted by major projects like Chromium, Next.js, Babel, Retool, WebStorm, and more. What makes JSON5 so popular? While the JSON file format is commonly used for machine-to-machine communication, the JSON5 extension makes it easier to write and maintain by hand.
When pentesting expert Jonathan Gregson discovered a JSON5 vulnerability, he initially made contact with Jordan through a GitHub issue to coordinate the submission—and that’s where things got complicated. Jordan wanted to avoid a public discussion without resorting to an unwieldy email thread. “We first tried another vendor to submit the vulnerability, but we never heard back from them.” So, he searched for an alternative and discovered the public beta of GitHub’s private vulnerability reporting feature. “I enabled it on my repository and asked Jonathan to submit a report on GitHub. From there, everything was quick and painless.”
The resulting fix (CVE) triggered more than 11 million alerts, a testament to both the popularity of JSON5, and to the value of private vulnerability reporting as a best practice that helps maintainers and security researchers keep open source projects healthy and secure.
Private vulnerability reporting makes it so much easier for the open source community to report and fix vulnerabilities, and I would encourage every maintainer to enable it on their public repositories.
Benefits for security researchers
We also spoke with Marco Squarcina, a postdoctoral researcher in the Research Unit Security and Privacy at TU Wien. In the course of his academic research, Marco discovered a vulnerability that bypasses security for cookies. “Once I found out that it was possible to submit through GitHub’s private vulnerability reporting feature, I contacted several maintainers and asked them to enable it so I could report the issue without relying on back-and-forth emails.”
From Marco’s perspective, however, the real advantage is for project owners. “Emails about a vulnerability can seem phishy or go unnoticed. Because private vulnerability reports open a collaboration channel with a draft pull request, maintainers get everything they need right on GitHub.” Marco is credited as the reporter on the GitHub Security Advisory, which also resulted in a CVE.
New features and automations
Thanks to feedback from the open source community, we’ve implemented a number of improvements for the general availability of private vulnerability reporting:
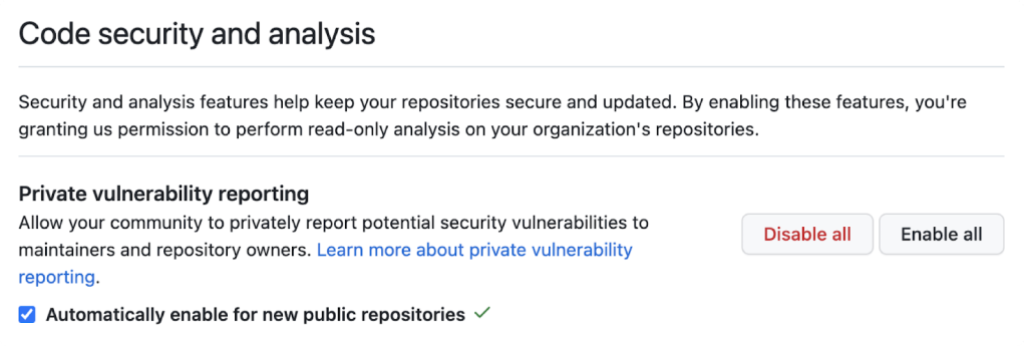
- Enable at scale. During the public beta, private vulnerability reporting could only be enabled on individual repositories. Now, maintainers can enable private vulnerability reporting on all repositories in their organization:
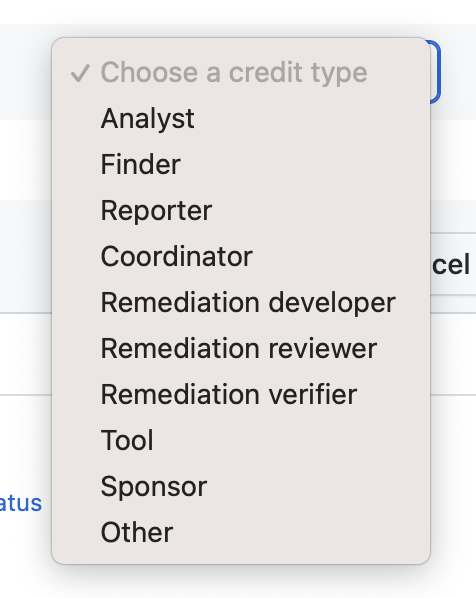
- Multiple credit types. Maintainers can choose how to credit those who find and contribute to vulnerabilities and remediation:
- Integration and automation. A new repository security advisories API supports several new integration and automation workflows:
- Integration with third-party systems: maintainers can pipe private vulnerability reports from GitHub to third-party vulnerability management systems.
- Automated submissions: security researchers can also use the API to programmatically open a private vulnerability report on multiple repositories, a time-saving convenience when packages share a common vulnerability.
- Vulnerability alerts: anyone can keep a close eye on critical repos by scheduling automatic pings for notifications of new vulnerability reports.
Private vulnerability reporting, together with the rest of GitHub’s security capabilities like Dependabot, code scanning, and secret scanning, is free for public repositories.
Learn more about private vulnerability reporting:
- About private vulnerability reporting
- Repository security advisories
- Repository security advisories API
Tags:
Related posts

3 ways to get Remote Code Execution in Kafka UI
In this blog post, we’ll explain how we discovered three critical vulnerabilities in Kafka UI and how they can be exploited.

Attack of the clones: Getting RCE in Chrome’s renderer with duplicate object properties
In this post, I’ll exploit CVE-2024-3833, an object corruption bug in v8, the Javascript engine of Chrome, that allows remote code execution (RCE) in the renderer sandbox of Chrome by a single visit to a malicious site.

Execute commands by sending JSON? Learn how unsafe deserialization vulnerabilities work in Ruby projects
Can an attacker execute arbitrary commands on a remote server just by sending JSON? Yes, if the running code contains unsafe deserialization vulnerabilities. But how is that possible? In this blog post, we’ll describe how unsafe deserialization vulnerabilities work and how you can detect them in Ruby projects.