We’re living in a world where software and hardware are ubiquitous—even more than you might initially think! When you think of hardware, what’s the first thing that comes to mind? Your phone? Your laptop? What about your washing machine or car? Or, one of the many smart home devices very likely scattered throughout your home?
When you consider these embedded systems from an industrial perspective, the opportunities are endless. From lifts (or elevators) to aircrafts, manufacturing lines to traffic signals, or medical equipment to the innovative world of robotics.
Those systems fundamentally rely upon software. The type of software that you find in these devices has historically been specialized for a given task. In your car, you may have systems that deal with functional aspects, such as engine and transmission management, or safety-critical systems, including airbag deployment or control of anti-lock braking systems.
We rely on these types of control systems every day. And the likelihood is that you never think about the critically that they play in our day-to–day lives. After all, as Arthur C. Clarke said, “Any sufficiently advanced technology is indistinguishable from magic.”
We know that DevOps is all about the continuous delivery of value to end-users. For these types of systems, quality and security are fundamental, non-negotiable aspects. Whether it’s ISO 26262 for automotive, IEC 62304 for medical devices, or any of the other myriad of functional safety standards, compliance to the standards adds significant complexity to the development process. When you add in ISO 27001 and the new UN regulatory requirements for cybersecurity on top of industry coding standards like AUTOSAR and Misra, you can see why finding ways to automate becomes even more critical in the world of embedded development.
In this post, we explore how GitHub can add value throughout the development lifecycle when designing, building, and deploying systems of this kind.
We know that software development starts with a well-understood plan. The fun part comes once your team has a clear plan, writing the code and shipping incredible experiences for your users! GitHub assists with all areas of the software development cycle, from plan to build, to deployment and continuous feedback.
Fundamentally, this all starts with version control software. GitHub has been around since 2008, and you probably know the platform because of our Git version control capabilities (though, you’ll understand there’s a lot more to GitHub these days!). Prior to 2008, source code management took many different forms.
From a software development perspective, storing your code in version control is critical to unlocking the many benefits that we can gain from modern software engineering practices. Storing our code in a Git repository in GitHub provides:
- A fully traceable history of the development on our codebase.
- Engineering teams with the ability to work in separate branches, so they don’t interfere with each other’s active work in development.
- The ability to rollback to a prior version of the codebase if needed.
- The option to add branch protection rules to the production codebase, so that all changes must be peer-reviewed or pass a set of automated quality gates before being merged.
- And much more!
These few bullet points highlight how version control is vital to developing these critical systems. With a detailed set of historical changes, the ability to add quality gates with branch protection rules and mandatory peer-reviews via pull requests, compliance suddenly becomes part of the process, as opposed to an afterthought or some additional set of boxes to check.
Think about these types of systems from a security perspective. What happens if someone was able to take over a set of embedded computers in a vehicle? The impact of this would depend on which specific systems, but could potentially be catastrophic. For safety systems, then it could potentially lead to loss of life.
With that context, security, understandably, should be a high priority for development teams making these critical systems. At GitHub, we believe that security is everyone’s responsibility, and should not be an afterthought, or a one-time review before go-live. Instead, it’s something which can, and should, be incorporated into the development workflow. Just like compliance in the above section, it’s something that becomes a part of what you do every day.
GitHub has several tools that can help you to bring security into your workflow. Let’s explore some of them a little further.
One of your first concerns may be the code that you write. We are human, and we are not perfect, so we don’t always write perfect code. Earlier, we talked about branch protection rules as an option to add quality checks into our development lifecycle. What if we could add security as one of those quality checks, and review the code that we have written?
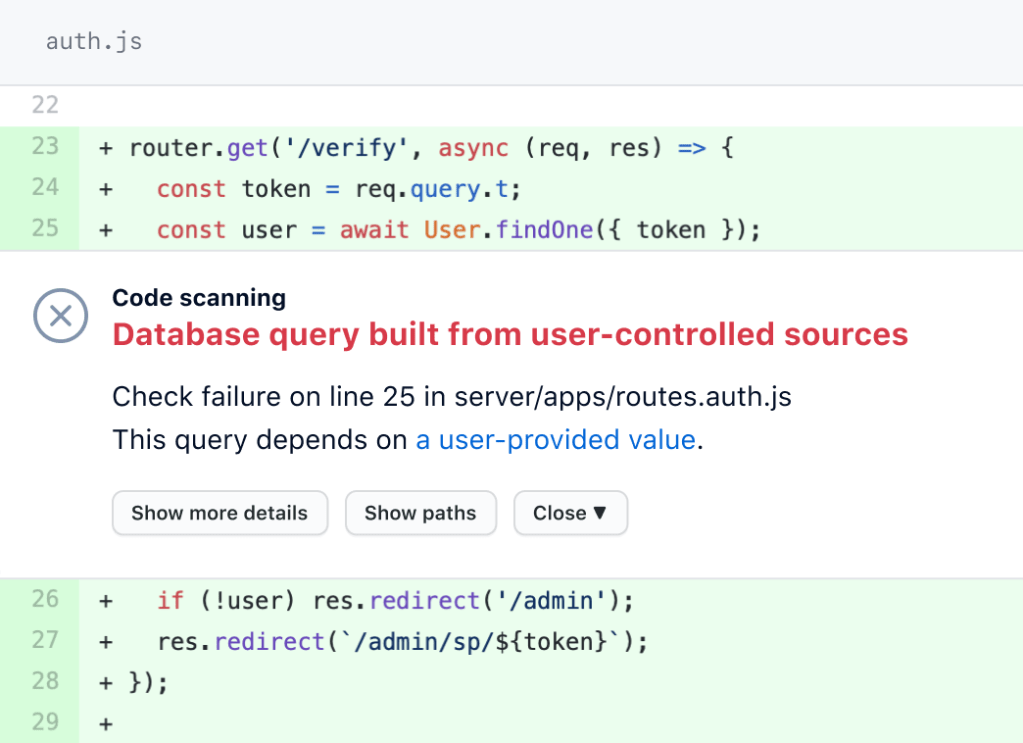
This is where GitHub code scanning capabilities come in. You can think of this from two perspectives; CodeQL (GitHub’s built-in code analysis engine that powers code scanning) and third-party integrations.
CodeQL supports several languages, including C, C++, Java, and Python; all common languages when building embedded systems. CodeQL is able to translate your code into a database-like structure. You’re then able to use a number of queries made by GitHub out-of-the-box, and can expand these with queries from the open source community to identify patterns that occur in your codebase, such as injection or buffer overflow vulnerabilities.
A CodeQL scan can be executed as part of the pull request flow that we mentioned earlier. So, security now becomes another check as part of your quality assurance process, before merging code into your production codebase.
In fact, Brittany O’Shea wrote a blog post last year about CodeQL queries that implement the standards, CERT C++ and AUTOSAR C++.
But what if you’re already using some security scanning tools? Not to worry—code scanning integrates with third-party tools, as long as they support the SARIF output format.
The software that you ship isn’t made of just the code you and your team have written. Open source software is increasingly being used, to build on the work of the wider community, rather than reinventing the wheel.
But now for the important question. How can you be sure that you’re not relying upon a vulnerable dependency in the software that you’re shipping? The answer isn’t to stop relying on open source. Instead, it’s about adopting open source software in a way that you are in control. This includes creating an Open Source Program Office (OSPO) in your organization to help manage your open source usage.
GitHub has tools available to help you keep your dependencies up to date. Let’s talk about Dependabot and dependency review.
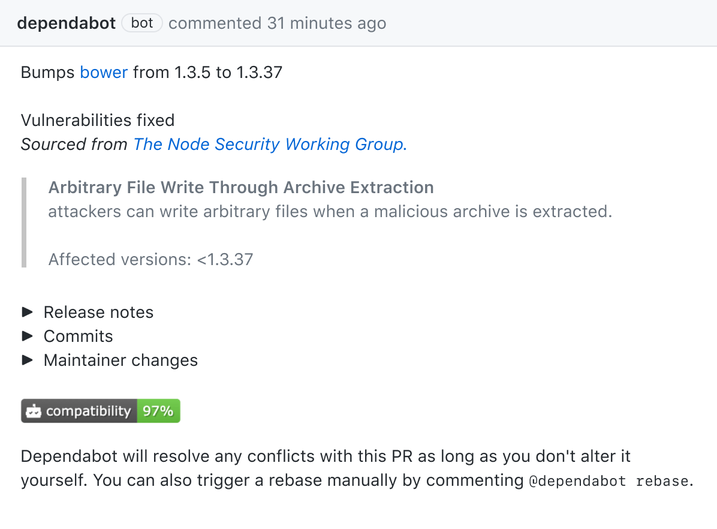
Dependabot is our handy tool to help you keep your dependencies up to date. Dependabot is able to identify if you are already using a package that contains a vulnerability. If you are using an insecure dependency, then it will privately alert you in your repository. This means you can take the appropriate action to expedite fixes and ensure your code is patched with the latest version. You can even directly open a pull request based upon the alert to expedite your fixes.
But Dependabot can help even further, by keeping your dependency versions proactively up to date. By tracking the contents of supported package manifests (such as Maven, pip, and others), it can open pull requests when more recent package versions are available. The best bit? As it’s a pull request, all of your quality checks must still be met! That includes any automated checks (more on those in a bit), and manual approvals must be met, before the changes can be merged.
While Dependabot primarily works on manifests that are already being used in production, what can you do to add guardrails to your quality assurance process? GitHub Advanced Security’s dependency review capability can help there.
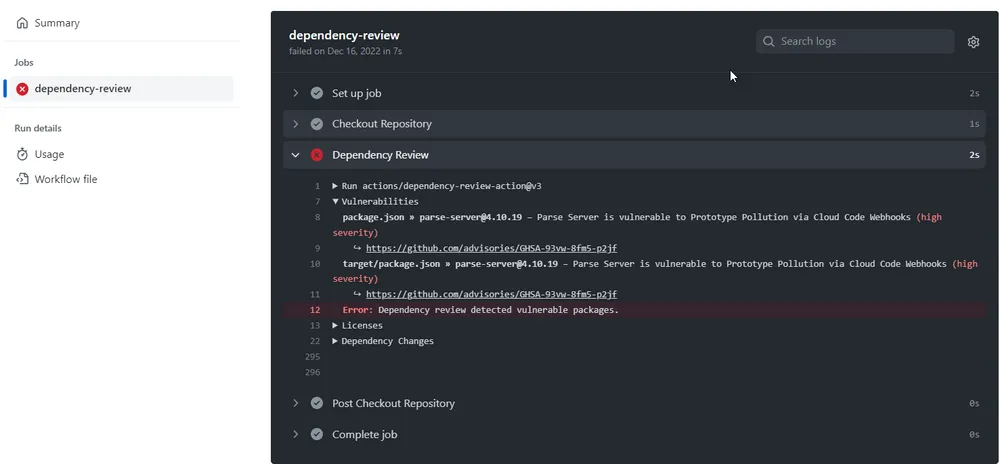
The Dependency Review GitHub Action is used in a pull request to scan for dependency changes. If a new vulnerability is detected (such as introducing a new package, or adjusting an existing package to a vulnerable version), then an error is raised by the GitHub Action, preventing the pull request from being merged.
According to the IBM “Cost of a Data Breach 2022” report, exposed secrets and credentials are the most common cause of data breaches and often go untracked. Storing secrets in source control is an anti-pattern and can be problematic in scenarios where you’re shipping software that is accessible to anyone. Think of software being shipped to untrusted hardware devices, such as a lift (or elevator), a car, manufacturing production line equipment or an Internet of Things (IoT) device. Malicious actors may be able to get access to the software running on the device, gain access to any credentials stored locally, and use these secret materials for a breach.
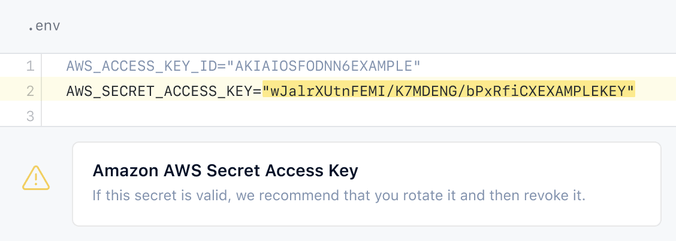
Fortunately, GitHub’s secret scanning capability can help. It can scan for hundreds of partner patterns, and allows you to even define your own custom patterns, too. This works well for retrospective scans of your codebase. Buthow do you prevent it from ever entering production? This is where secret scanning push protection comes in, which was recently updated to also identify custom patterns.
One of the main challenges from a security perspective is knowing where the weak points may be. As software engineers and engineering leads, we’re typically working in the scope of a project. However, our colleagues in security typically focus on the security posture of the overall organization. For them, it’s important to understand which repositories contain vulnerable code or packages, or whether secrets have been committed into those repositories.
We know that monitoring and observing these metrics is important, so we provide a security overview in GitHub Enterprise Cloud. This visualizes the results from GitHub Advanced Security, so that you have an all-up view of your current coverage and risk areas.
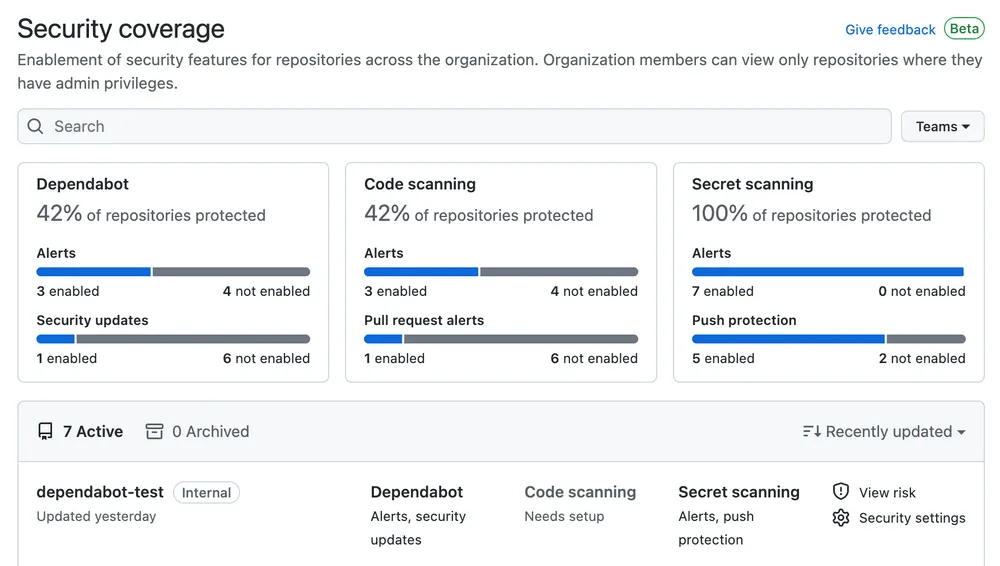
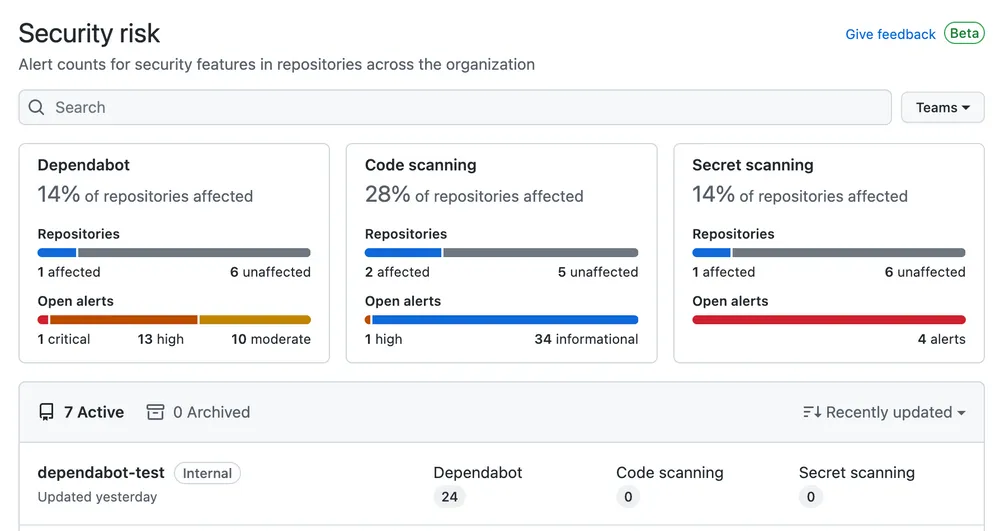
If you have invested in security information and event management (SIEM) tooling, then you’ll be pleased to know that there are integrations available with several providers to further aid your management and monitoring needs.
We’ve mentioned that these types of software can be critical, so safeguards and controls should be in place. But to empower your developers, you need to give them access to tools to get the job done. That includes the ability to easily build, test, and deploy your software.
Building on the earlier themes, you can use GitHub branch protection rules to ensure certain standards are met before code is ever allowed to be merged into your production codebase. Earlier, we talked about peer reviews and collaboration. But what about using automation to help accelerate the process?
This is where GitHub Actions comes in. GitHub Actions is our CI/CD solution that allows you to automate your software workflows. You can use GitHub Actions in the development lifecycle of your embedded systems to:
- Easily share common build and deployment patterns across your engineering teams using reusable workflows.
- Cross-compile across different hardware platforms with GitHub Action’s matrix capabilities, or with Arm development tools inside GitHub Actions cloud-hosted runners.
- Automatically build and test software as part of your continuous integration process. In your pull requests, ensure that a successful build takes place, and tests are successful before merging to production.
- Automatically package and deploy updated firmware images efficiently, so that they are available to end-users timely and efficiently.
- Automatically deploy firmware updates to embedded systems, by orchestrating updates and releases as part of your CD process.
This has been a high-level overview of GitHub, and how it can help from an embedded software perspective. With our collaborative platform to empower developer productivity and enable secure development, we’re sure there are many scenarios where GitHub can help you even further.
Want to find out more? We will be at Embedded World 2023, so come and chat with us there! We’ll be at stand no. 4-501a in Hall 4.
Not able to join us? Then start a free trial on GitHub Enterprise to explore how GitHub can help with your day-to-day development!
Written by
Chris is a passionate developer advocate and senior program manager in GitHub’s Developer Relations team. He works with execs, engineering leads, and teams from the smallest of startups, established enterprises, open source communities and individual developers, helping them ❤️ GitHub and unlock their software engineering potential.