Download version 3.7 now, and, for help upgrading, use the Upgrade Assistant to find the upgrade path from your current version of GHES to this new version.
GitHub Enterprise Server 3.7 is now generally available
GitHub Enterprise Server 3.7 is available now, including a single view of code risk, new forking and repository policies, and security enhancements to the management console.
GitHub Enterprise Server 3.7 is now generally available. This release continues our trend of bringing record numbers of new features to our GitHub Enterprise Server (GHES) customers, designed to enable developers to build every day while providing administrators with tools to run GitHub Enterprise at scale, with reliability at its heart.
Highlights of the GHES 3.7 release include:
- Reusable workflows and new support for Google Cloud Storage, making it easier to build with GitHub Actions at scale.
- Security overview gives developer managers and security teams a centralized view of security.
- An improved management console to keep your instance more secure than ever with automated user onboarding and offboarding.
- New forking and repository policies, so adopting innersource best practices is easier, all while balancing auditability and maintaining projects for the long term.
- Code scanning alerts are now surfaced in the pull request conversation tab for more collaborative security reviews.
It’s easier to deploy GitHub Actions, securely, at scale
GiHub Actions is the developer automation tool, designed to make it easy to automate any workflow and share those workflows easily across teams. Released initially in GHES 3.5, reusable workflows enable enterprise developers to share workflows within a company and enforce their usage across projects.
This release brings two major enhancements to reusable workflows that make it easier for teams to share automation:
- Reusable workflows can now be nested together, enabling teams to craft novel but compliant workflows quickly. Read more about reusing workflows.
- Reusable workflows now support matrix job definitions, making it easier to run a single CI job over many different hosting environments, for example. For more information about matrices, see Using a matrix for your jobs.
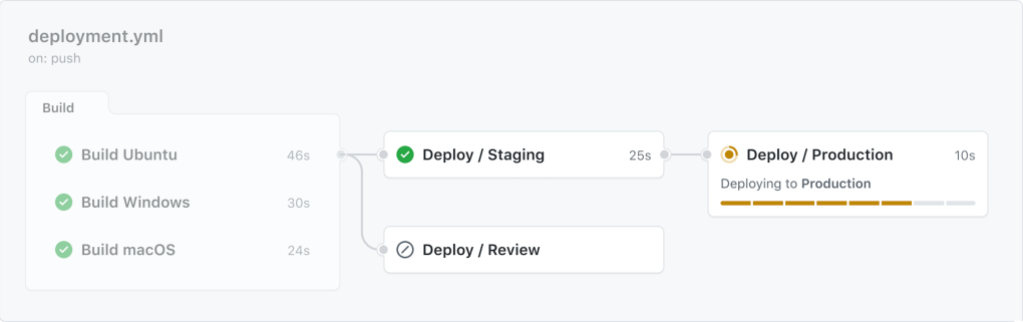
Companies using GitHub Pages can also now deploy those pages directly from a repository using GitHub Actions—so you can use GitHub Actions as a single CD provider for your apps and GitHub Pages, with deployment gates and environments built in.
GitHub Actions now supports Google Cloud Storage
With GHES 3.7, administrators can configure Google Cloud Storage for GitHub Actions to store logs, artifacts, and caches from a server instance, set up directly from the management console.
Adopt innersource best practices with new developer workflows and enterprise policies
GitHub has long been the platform for sharing code across companies, and enabling teams to innovate faster by breaking down organizational silos. To make it easier for any developer and company to adopt innersource practices, while balancing security and auditability, GHES 3.7 brings a wealth of enhancements to the forking experience, forking policies and repository creation policies. Here are a few examples.
Keep all repositories in your Organizations
When enterprise developers create repositories in their personal namespace, administrators can be left with long-term problems: from a lack of auditability and policy enforcement to long-term maintainership problems when developers leave. A powerful new forking workflow helps to address this challenge, backed by two new enterprise policies for administrators.
Developers can now fork a repository into the same Organization and name the fork at the same time. The fork will retain the same visibility as its upstream repository, whether that’s private, public, or internal.
And administrators can enable two enterprise-wide policies that ensure all new repositories are owned by compliant, auditable organizations: they can restrict new repositories to Organizations only, and they can restrict forks to Organizations, too. Together, these changes are designed to make it easier for any company to innovate with innersource.
Keep your instance more secure than ever
Identity providers, such as Azure Active Directory and Okta, are often the best source of the truth for which employees should have access to a GHES instance and what team they’re in. Today, administrators can configure SAML SSO with an identity provider, but offboarding and team management are completely separate. That can result in duplicate work, and complex time-sensitive offboarding processes.
This release includes a private beta of SCIM user management, which allows administrators to provision and suspend user accounts in fully automated fashion via the new SCIM APIs, and populate team membership—- directly from your identity provider. Read more about the SCIM APIs, or reach out to your account manager to try the private beta now.
Meanwhile, the management console has just gotten a security facelift, with stricter password policies and a complete audit log.
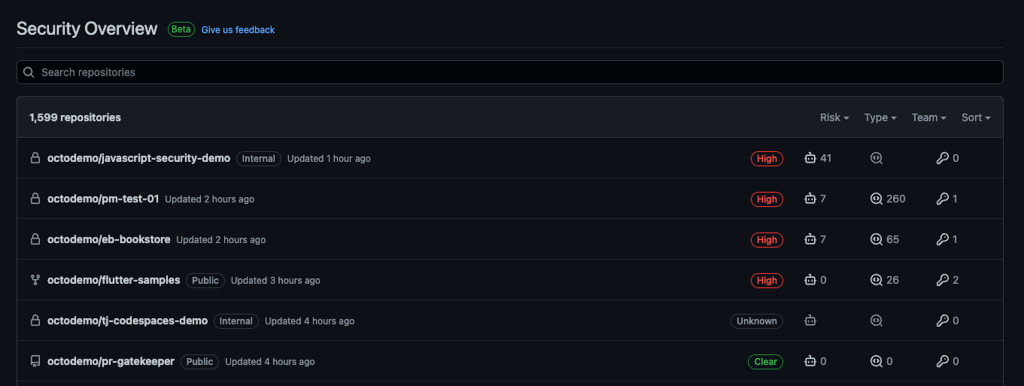
Security teams now have a single view of code risk
Every enterprise customer now has access to security overview, which provides a centralized view of your security posture across the entire enterprise. Application security teams, engineering leaders, and developers can see Dependabot alerts, code scanning and secret scanning alerts, and more, all in one place. You can find the security overview in the Code Security tab of the enterprise account:
Reduce the chance of missing dependencies or code scanning alerts
GitHub’s dependency graph automatically scans most popular manifest formats, but some manifests like those from Gradle, Scala SBT, or Maven either cannot be scanned statically, or do not include transitive dependencies automatically. The dependency submission API allows CI workflows to submit dependencies from recent builds to GitHub’s dependency graph in the form of a simplified software bill of materials (SBOM). These dependencies are then visible in the GitHub dependency graph and can generate Dependabot alerts for vulnerabilities. To learn more about expanding the dependency graph with the submission API, read here.
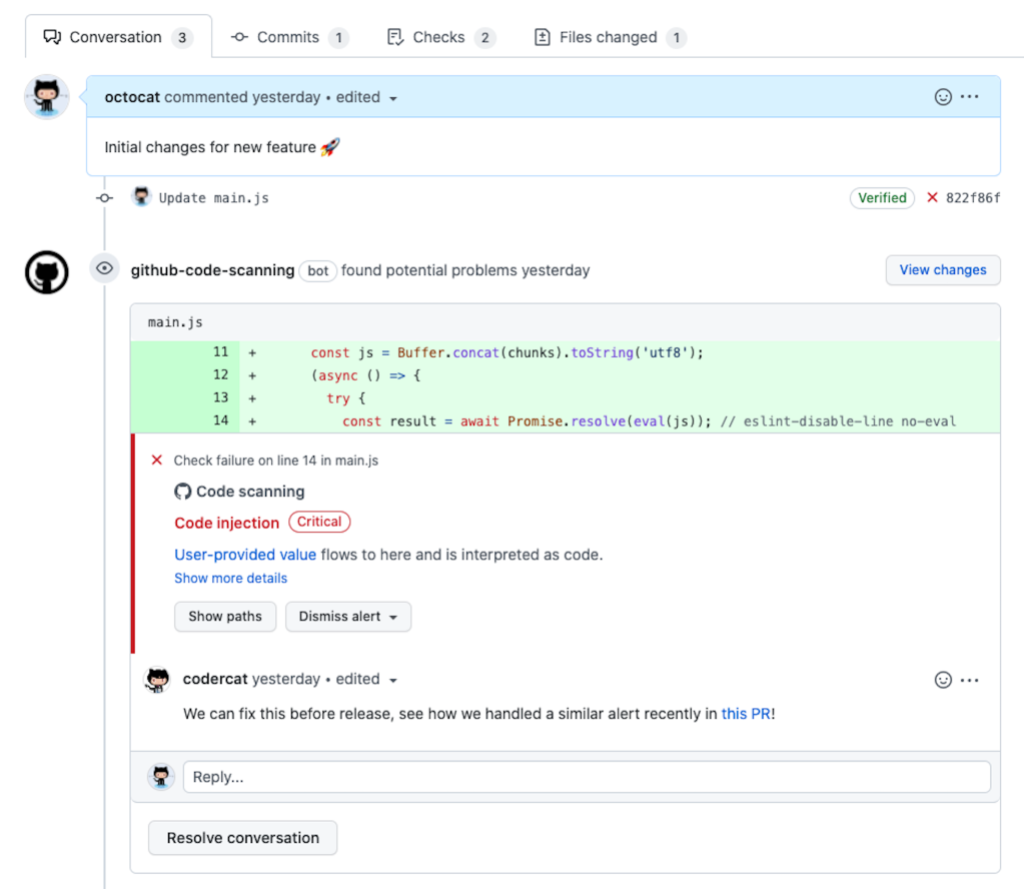
To make it even easier to assess the impact of security vulnerabilities, we are making code scanning alerts more collaborative, accessible, and relevant. We now display security alerts on the pull request’s Conversation tab by adding them as interactive annotations. Developers can comment on these annotations and continue to use all existing functionality to effectively triage the alert (including show paths, dismiss alert, and show details):
Try it out today
To learn more about GitHub Enterprise Server 3.7, read the release notes, and download it now.
Not using GHES already? Start a free trial to innovate faster with the platform developers know and love.
Tags:
Written by
Related posts

From pair to peer programmer: Our vision for agentic workflows in GitHub Copilot
AI agents in GitHub Copilot don’t just assist developers but actively solve problems through multi-step reasoning and execution. Here’s what that means.

GitHub Availability Report: May 2025
In May, we experienced three incidents that resulted in degraded performance across GitHub services.

GitHub Universe 2025: Here’s what’s in store at this year’s developer wonderland
Sharpen your skills, test out new tools, and connect with people who build like you.