A well-tuned and secure CI/CD workflow is a critical component for development teams looking to build more and ship fast. GitHub Actions gives teams access to powerful, native CI/CD capabilities right next to their code hosted in GitHub.
Starting today, GitHub will send a Dependabot alert for vulnerable GitHub Actions, making it even easier to stay up to date and fix security vulnerabilities in your actions workflows. These alerts will be powered by the GitHub Advisory Database. When a security vulnerability is reported in an action, our team of security researchers will create an advisory to document the vulnerability, which will trigger an alert to impacted repositories. Like all of the data in the GitHub Advisory Database, these advisories are searchable and forever free. Improvements like these strengthen GitHub and our users’ security posture, which is why we continue to invest in tightening connection points between GitHub’s supply chain security solutions and GitHub Actions to improve the security of our builds.
Dependabot alerts for GitHub Actions
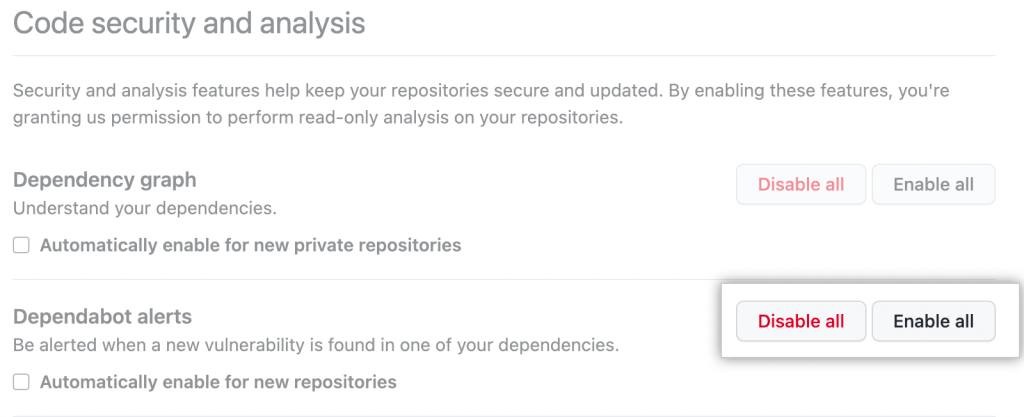
The GitHub Advisory Database powers Dependabot alerts for impacted GitHub repositories. If you already use Dependabot, you’re covered with no additional action required. To receive alerts on GitHub Actions and vulnerabilities impacting your code, you can enable Dependabot by selecting “Enable all” under the Code security and analysis tab.
Submitting an advisory for your GitHub Action
If you are the owner of a GitHub Action and you discover a vulnerability, you can start the process of creating an advisory from the security tab in your repository. Once the repository advisory is created and tagged within the GitHub Action ecosystem, the GitHub curation team will review the repository advisory and create a global advisory when appropriate.
For a seamless disclosure process, when creating a GitHub Action advisory, please ensure:
- The GitHub Action uses semantic versioning.
- You own the repository of the action you are creating the alert for.
- Package names are formatted as a user or organization name followed by the repository name with a slash in between: “org-name/repo-name.” An example would be “GitHub/GitHub’s-favorite-action.”
- There is only one action in the repository, so it is distinguishable from other actions.
Learn more about GitHub Actions
As the #1 CI/CD tool used on GitHub repositories, GitHub Actions helps teams of all sizes speed up their development velocity and increase the reliability of their software. By combining reusable workflows and GitHub Actions policies, such as limiting which actions can be used in your org or enterprise, customers can scale their efforts to maintain a more secure codebase across their enterprise. With more than 13,000 actions to choose from, there is an opportunity for every team to improve their development processes with a GitHub Action.
Learn more about GitHub supply chain security solutions
The GitHub Advisory Database publishes security advisories that power GitHub’s supply chain security capabilities, including Dependabot alerts and Dependabot security updates. The data is licensed under a Creative Commons license and has been since the database’s inception, making it forever free and usable by the community. For more information about our supply chain security capabilities, check out the following pages: