Extend your dependency information in the GitHub Dependency Graph with new GitHub Actions
New Actions from Anchore, NowSecure, SBT, and Trivy are now available to create a more comprehensive GitHub Dependency Graph.

Earlier this month, we released an API that allowed you to upload dependency information directly to GitHub. Previously, GitHub built the dependency graph entirely from static scans of checked-in manifest files. That limited the completeness of the graph in some ecosystems. With the dependency submission API, you may upload dependency information directly to GitHub; for instance, from your build tool or container scanning service. By combining build time detection with static scanning, GitHub can provide a more comprehensive dependency graph and alert you of more vulnerabilities.
The API accepts a simple list of dependencies that reflect the current state of your repository in a commit. A typical flow will be to add a GitHub Action that supports the dependency submission API to your repository. Today, we are excited to announce new actions from our partners that will help you further enrich your visibility.
Learn more about the new actions
Anchore
Anchore’s sbom-action gives users the ability to scan both source code repositories and container images to generate comprehensive software bills of materials (SBOM), which can be uploaded into your GitHub Dependency Graph with the dependency submission API. The SBOMs generated through sbom-action identify nested dependencies and other information, such as file system and package metadata for components that can be used for highly accurate vulnerability matching. The sbom-action can be used in conjunction with another Anchore GitHub Action, scan-action. View supported ecosystems here.
NowSecure
NowSecure provides automated static and dynamic security analysis of iOS and Android mobile apps built in any language or framework including Swift, Objective-C, Java, Kotlin, Dart, React-Native and more. Through black-box dynamic SBOM generation, the new NowSecure GitHub Action for Mobile SBOMs identifies third-party components and transitive dependencies to populate the GitHub Dependency Graph, enabling automated Dependabot alerts for vulnerable mobile libraries. This can be used in conjunction with the NowSecure scan action which provides automated static and dynamic security testing for mobile applications. NowSecure is a paid service, but you can request a free mobile SBOM dependency scan from NowSecure here.
sbt
The sbt action enables Scala projects to submit dependencies to the dependency graph. This gives users with sbt builds who previously didn’t have visibility into their dependencies through the dependency graph the power to leverage the dependency graph and get Dependabot alerts on these dependencies. Scala is the 25th most popular language on GitHub, and this new action expands dependency graph functionality to Scala users.
Aqua Trivy
Aqua Trivy is a free, open source, cloud-native security scanner capable of detecting vulnerabilities in code repositories and container images and identifying misconfigurations in Infrastructure as Code (IaC) and Kubernetes across a wide variety of programming languages and operating systems. Developers using the Aqua Trivy action can now use it to populate the GitHub Dependency Graph with more comprehensive data from Aqua Trivy’s detailed SBOMs.
See it in action
Once set up these actions will populate the results of the scan into your dependency graph for review.
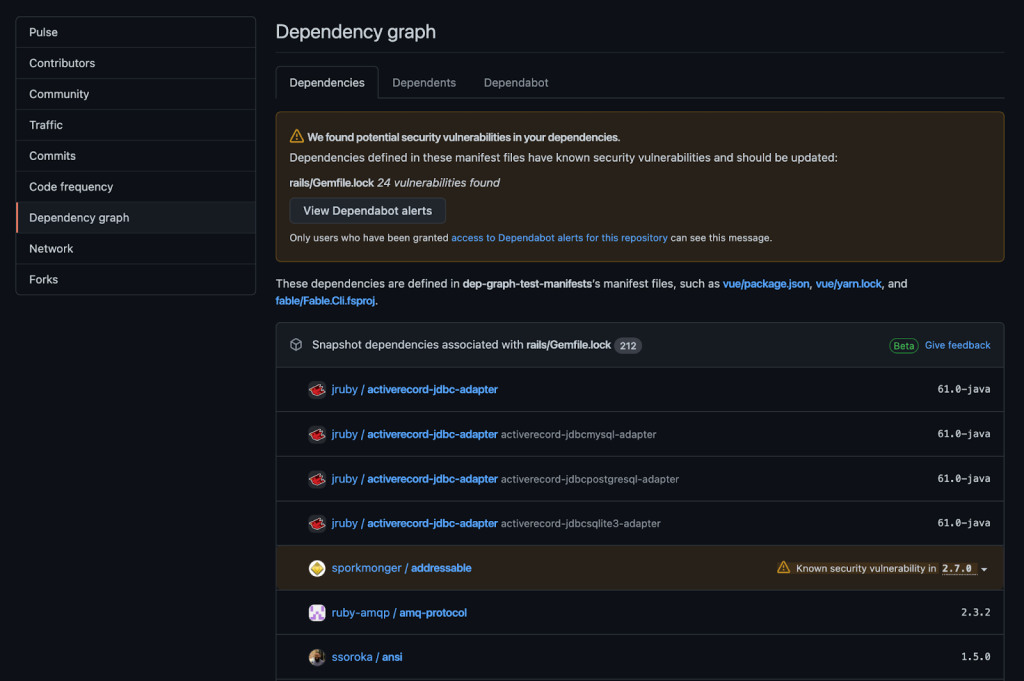
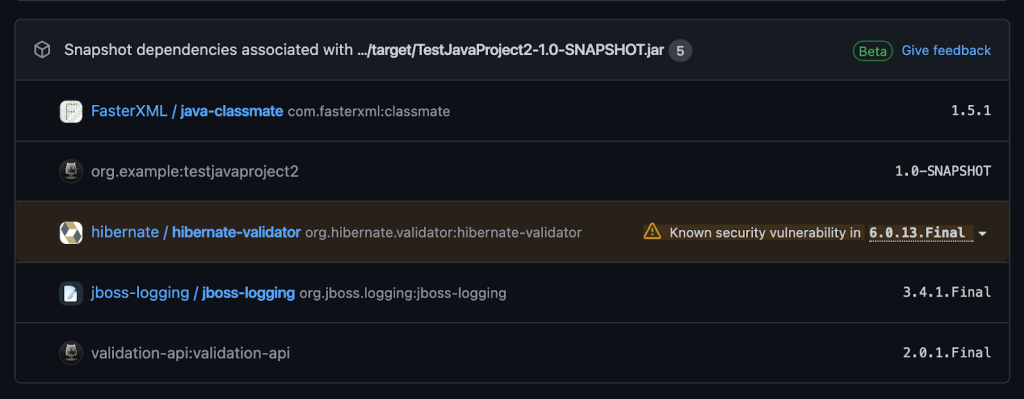
Start using the GitHub dependency submission API
To learn more about using the API, check out our documentation to get started, or use the Dependency Submission Toolkit to write your own detector!
Tags:
Written by
Related posts

How to scan for vulnerabilities with GitHub Security Lab’s open source AI-powered framework
GitHub Security Lab Taskflow Agent is very effective at finding Auth Bypasses, IDORs, Token Leaks, and other high-impact vulnerabilities.

AI-supported vulnerability triage with the GitHub Security Lab Taskflow Agent
Learn how we are using the newly released GitHub Security Lab Taskflow Agent to triage categories of vulnerabilities in GitHub Actions and JavaScript projects.

Community-powered security with AI: an open source framework for security research
Announcing GitHub Security Lab Taskflow Agent, an open source and collaborative framework for security research with AI.