
A short guide to mastering keyboard shortcuts on GitHub
Say goodbye to constant mouse clicking and hello to seamless navigation with GitHub shortcuts.
Today, we're shipping a new feature for Dependabot alerts which helps you better understand how you're affected by a vulnerability.
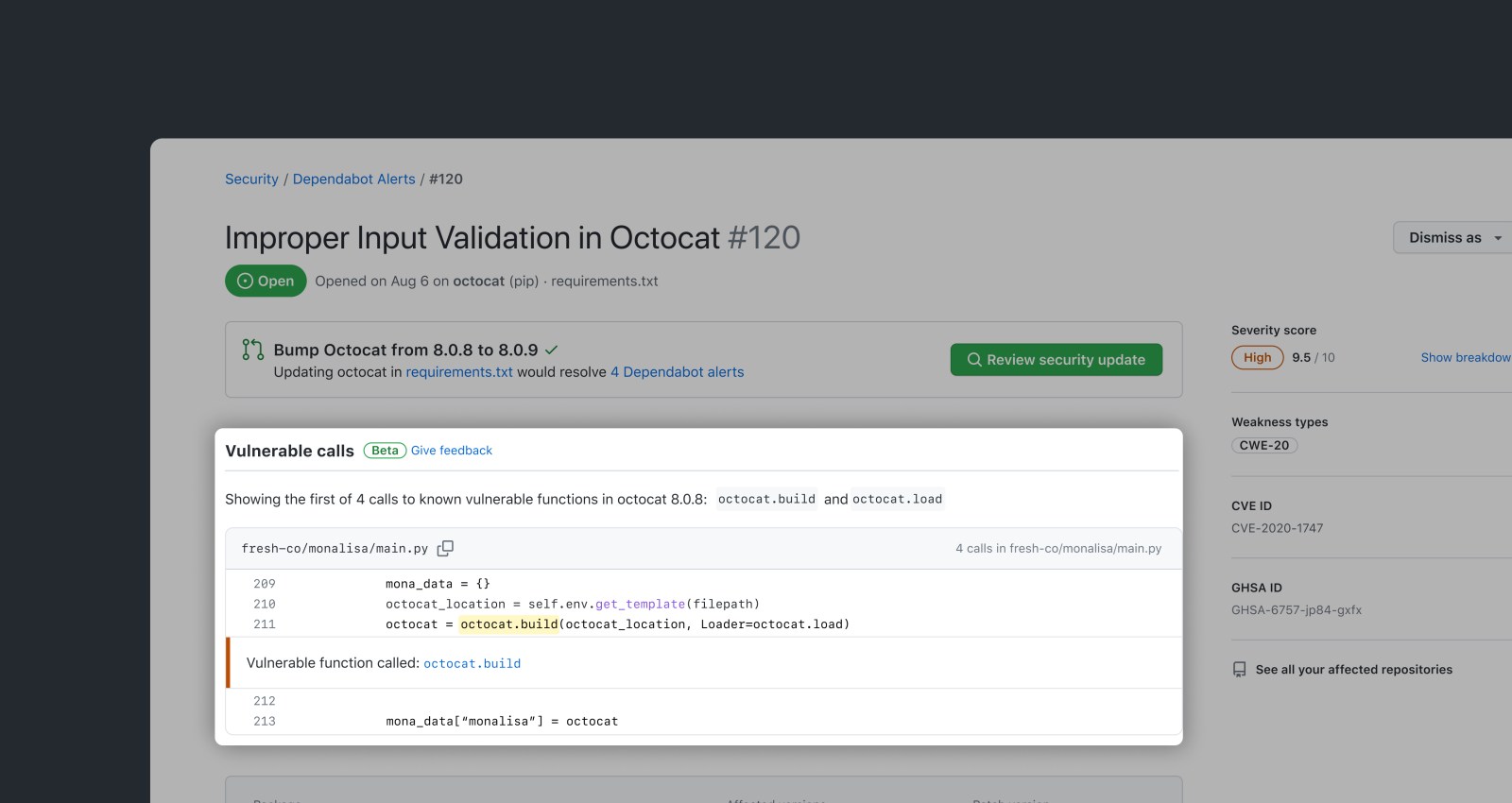
Since our February ship of improvements to Dependabot alerts, Dependabot has helped developers resolve nearly 3 million alerts. Today, we’re shipping an exciting new feature which will make Dependabot alerts even more insightful. Dependabot alerts will now surface whether your code is calling vulnerable code paths, so that you can prioritize and remediate alerts more effectively.
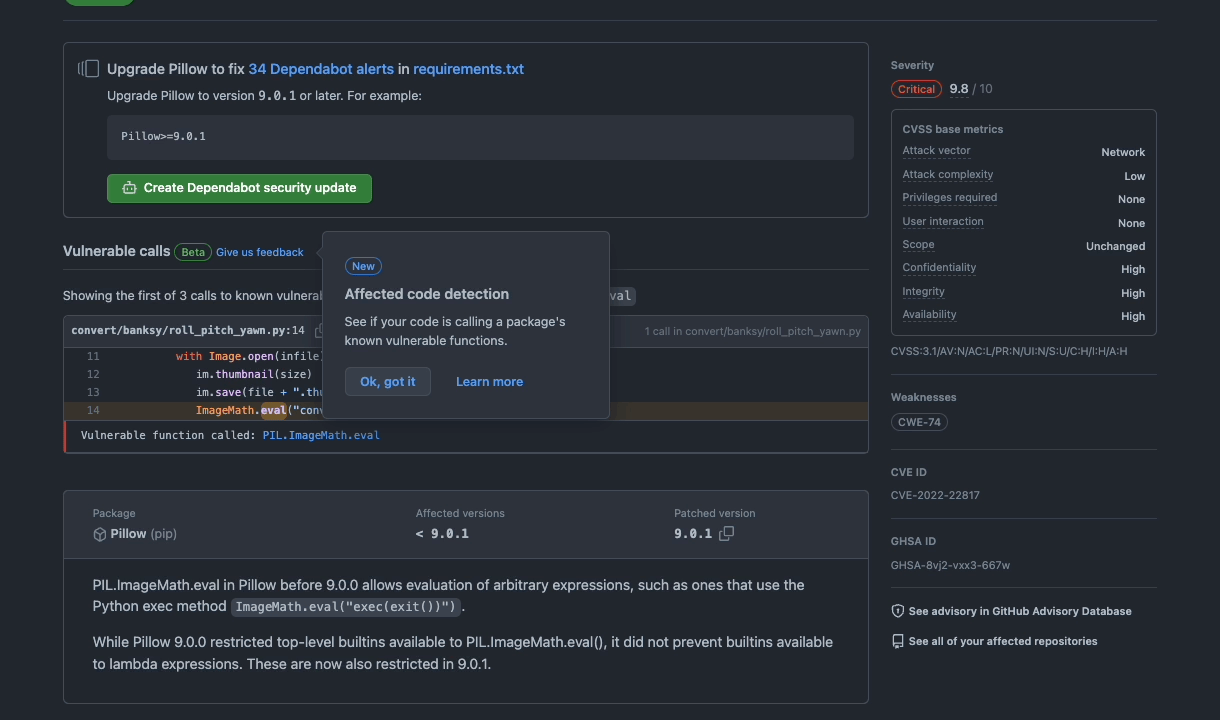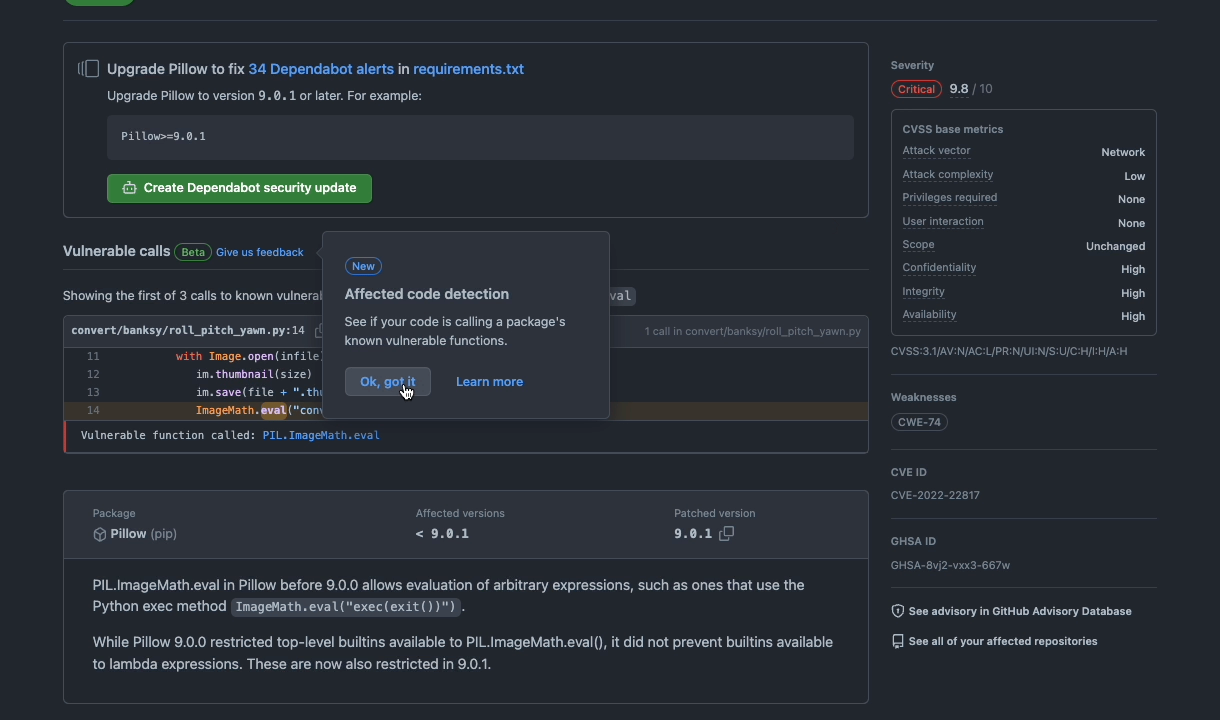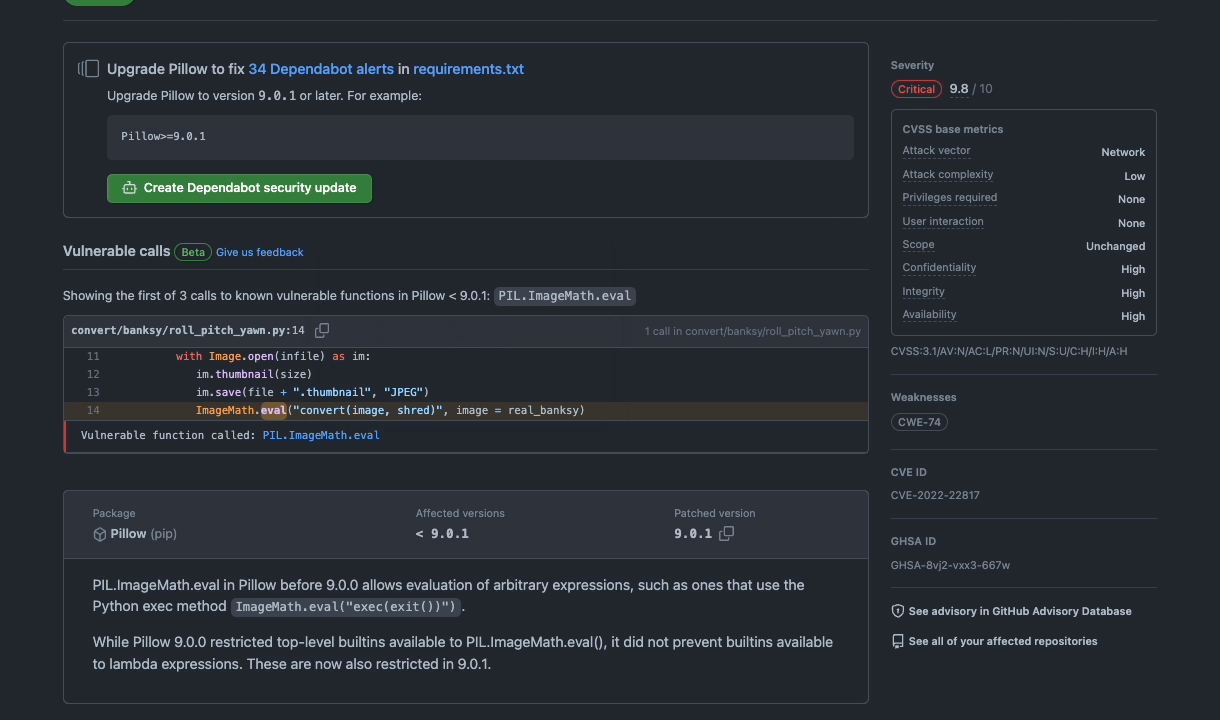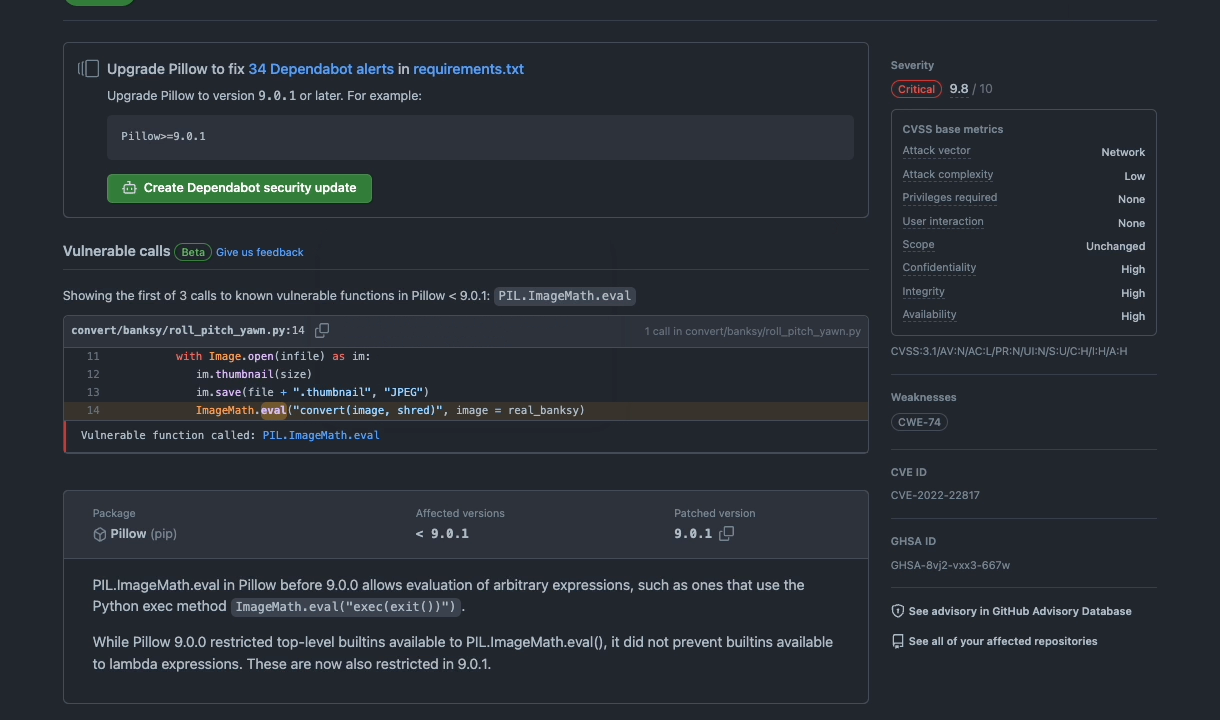
Dependabot alerts will now use GitHub’s precise code navigation engine to determine if a repository directly calls a vulnerable function. That information will then be surfaced to developers via the UI for Dependabot alerts.
Today, GitHub curates information on vulnerable packages in our Advisory Database. Moving forward, as part of the advisory publication process, GitHub will curate information on affected functions for each source library. Leveraging GitHub’s semantic code graph, we perform static analysis with these functions in order to generate an affected call graph for your repository, which is surfaced in a Dependabot alert.
This implementation is powered by Stack Graphs, the same framework that powers Precise Code Navigation. This provides a no-configuration experience that works for any advisories with annotated vulnerable functions.
Today, we have details of vulnerable functions for 79 Python advisories from the pip ecosystem. We’ll continue backfilling data on vulnerable functions for Python advisories through the beta, as well as supporting any new Python advisories. In addition, we plan to make it possible for anyone to view affected functions in GitHub’s advisory database, as well as to suggest vulnerable functions via community contributions in the near future.
This feature is enabled for supported Dependabot alerts on public repositories, as well as on repositories with GitHub Advanced Security enabled.
We don’t yet support indirect calls to vulnerable functions, but we’re working on it!
Over the next coming months, we’ll continue to improve Dependabot alerts with new features that help you better understand how you’re affected by a vulnerability, including through flagging development dependencies and transitive dependency paths.
Through this beta for affected code detection in Dependabot alerts, we’ll continue to add support for more historical Python advisories from the pip ecosystem. After beta testing with Python we will add support for other ecosystems. Please keep an eye on the public roadmap for more information.
Let us know what you think about the feature – your feedback helps shape the future of Dependabot alerts.