GitHub Security Bug Bounty program turns one
It’s already been a year since we launched the GitHub Security Bug Bounty, and, thanks to bug reports from researchers across the globe, 73 previously unknown security vulnerabilities in our…
It’s already been a year since we launched the GitHub Security Bug Bounty, and, thanks to bug reports from researchers across the globe, 73 previously unknown security vulnerabilities in our applications have been identified and fixed.
Bugs squashed
Of 1,920 submissions in the past year, 869 warranted further review, helping us to identify and fix vulnerabilities fitting nine of the OWASP top 10 vulnerability classifications. 33 unique researchers earned a cumulative $50,100 for the 57 medium to high risk vulnerabilities they reported.
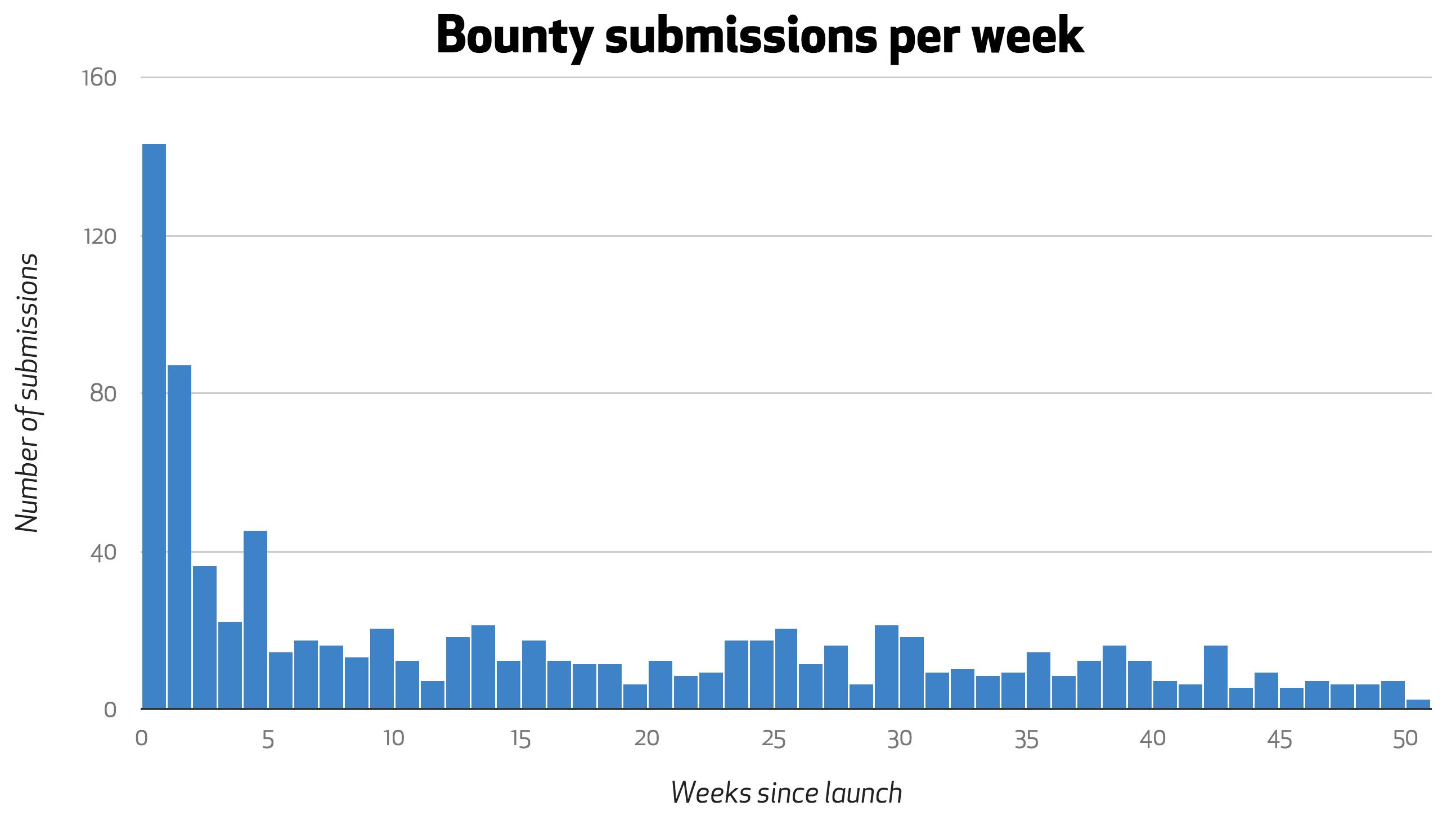
We also saw some incredibly involved and creative vulnerabilities reported.
Our top submitter, @adob, reported a persistent DOM based cross-site scripting vulnerability, relying on a previously unknown Chrome browser bug that allowed our Content Security Policy to be bypassed.
Our second most prolific submitter, @joernchen, reported a complex vulnerability in the communication between two of our backend services that could allow an attacker to set arbitrary environment variables. He followed that up by finding a way to achieve arbitrary remote command execution by setting the right environment variables.
New year, higher payouts
To kick off our Bug Bounty Program’s second year, we’re doubling the maximum bounty payout, from $5000 to $10000. If you’ve found a vulnerability that you’d like to submit to the GitHub security team for review, send us the details, including the steps required to reproduce the bug. You can also follow @GitHubSecurity for ongoing updates about the program.
Thanks to everyone who made the first year of our Bug Bounty a success. Happy hunting in 2015!
Tags:
Written by
Related posts

From pair to peer programmer: Our vision for agentic workflows in GitHub Copilot
AI agents in GitHub Copilot don’t just assist developers but actively solve problems through multi-step reasoning and execution. Here’s what that means.

GitHub Availability Report: May 2025
In May, we experienced three incidents that resulted in degraded performance across GitHub services.

GitHub Universe 2025: Here’s what’s in store at this year’s developer wonderland
Sharpen your skills, test out new tools, and connect with people who build like you.